On December 7, 2022, Praetorian Labs released a regular expression-based (RegEx) version of our Nosey Parker secrets scanning tool (see press release). This version improves on two primary pain points the community has historically encountered with other secrets scanning tools. First, Nosey Parker RegEx offers the fastest secrets scanning capability on the market–100 gigabytes of Linux Kernel source history on a laptop in five minutes. Additionally, the user-friendly reporting format enables users to find security incidents and their locations quickly, saving them time-consuming manual searches.
A fast, effective secrets scanning tool is a necessity for every cybersecurity engineer, as inadvertently exposed secrets often provide attack paths into an organization. An attacker who can find and exploit one of these secrets in source code or configuration files ultimately can gain access to passwords, access tokens, and other keys that unlock additional systems. Scanning for, discovering, locating, and concealing these security breaches is a critical part of many defensive security roles. It also is incredibly time intensive without the right tool, which is where Nosey Parker RegEx comes into play.
Initial Response
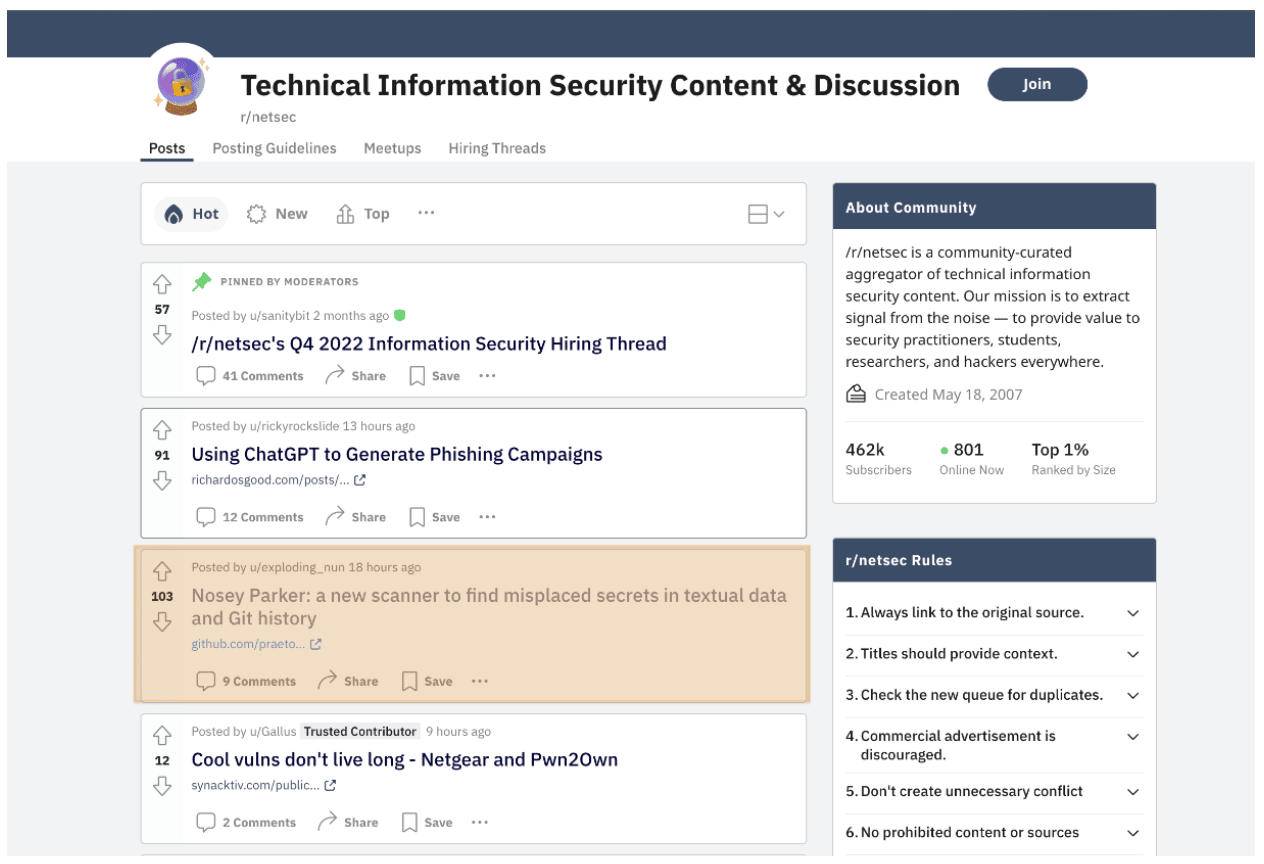
Over 1,500 unique hits to its Github repository on December 9, 2022 alone suggests that we have offered a viable solution to the community’s need for a faster, more efficient secrets scanning tool. Nosey Parker RegEx even made the front page of a couple reddits (see figure)! We are proud of the impact that this tool seems to be making, and are excited to see what novel use cases and innovative rules the community contributes moving forward.
Figure: Nosey Parker RegEx featured on the front page of this and another reddit on 12/9/2022.
Nosey Parker RegEx is a portion of Nosey Parker, a purely machine learning-powered version of the tool embedded in our Chariot platform. Chariot is our total attack lifecycle solution and demands constant flexibility and adaptability from all its embedded modules. Therefore, the embedded tool uses machine learning to look beyond the patterns offered by the RegEx tool and learn as it goes. For a deeper dive on the more robust features and why they matter, check out our post from earlier this year . To learn about accessing the features of the embedded Nosey Parker module, reach out to our Chariot team.