Achieve Penetration Testing Compliance Requirements for Free!
Take advantage of Chariot’s attack surface management capabilities along with a team of expert managed security engineers to achieve powerful human driven continuous penetration testing.
After the 15-day engagement you will receive:
- An Attack Surface Health Report
- A Detailed Summary of Findings
- A Live Debrief with Praetorian Team
- Satisfy PCI DSS, ISO 27001, NY-DFS, SOC 2, and more!
Some restrictions apply. Trial account given upon qualification meeting. Only new accounts are eligible for offer. Offer applies to external network testing only.
15-Day Free Pilot Continuous Penetration Testing
Please provide your contact information
Trusted by the World’s Most Iconic Brands

Stay Ahead of Potential Attacks
Address Exploitable Risk, Not Superficial Detections
Our team of industry leading security engineers will deliver 15-days of free continuous human driven penetration testing against your environment.
- Address exploitable risk, not superficial detections
- Reduce complexity through an all-in-one offensive platform
- Bring the attacker's perspective to every challenge
- Integrate technologies and expertise into a cohesive, efficient, and effective Continuous Threat Exposure Management strategy
- Quantify risks and focus on material threats rather than attempting to address every potential issue
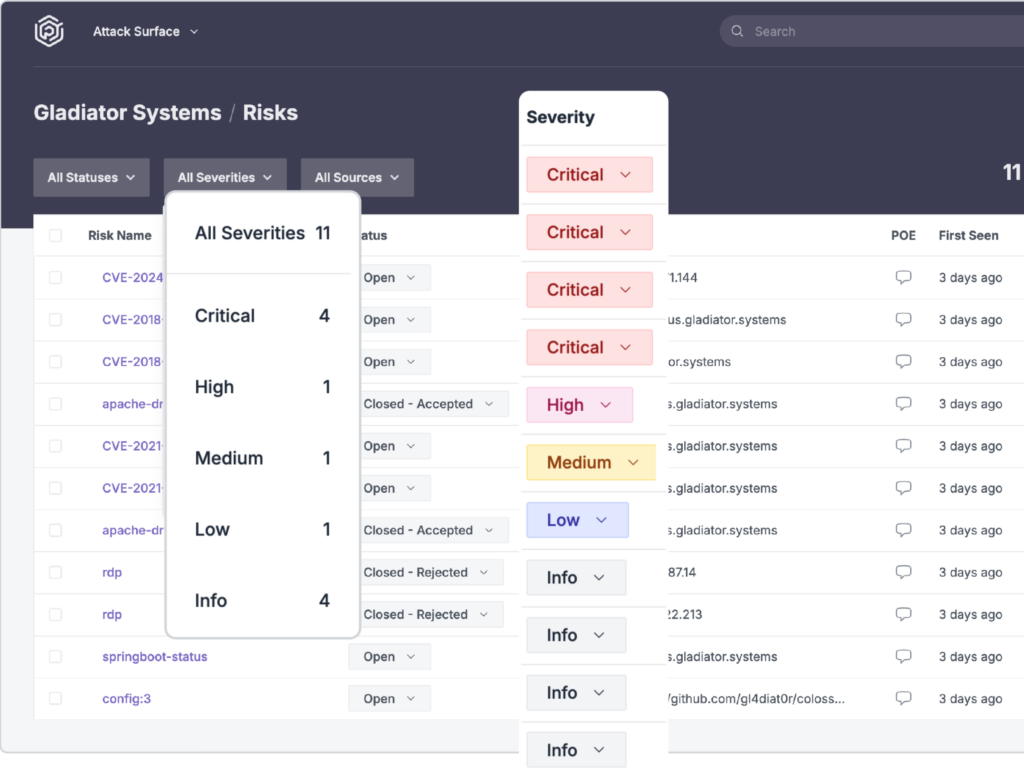
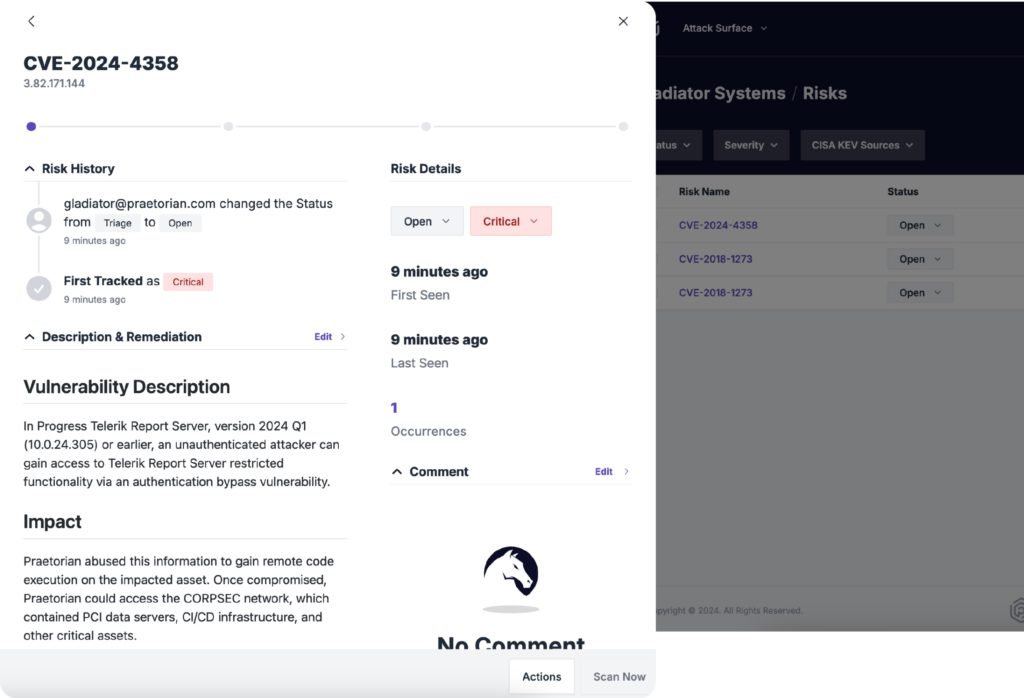
Continuous Threat Exposure Management Program
Praetorian’s Chariot platform is designed to embody the principles of a Continuous Threat Exposure Management (CTEM) program, by combining people, process, and technology.
Chariot incorporates attack surface management, vulnerability management, attack path mapping, breach and attack simulation, continuous penetration testing/red teaming, and exploit/threat intelligence into a single solution. These components, wrapped in a managed service, work in complete unison to provide unparalleled security coverage.
Proactive Security to Uncover Your Organizations Material Risk
Continuous Asset Mapping
Once we identify key risks, we map out the assets where this critical data is stored. This step is crucial for understanding the potential attack surface and identifying all possible entry points for attackers.
Continuous Attack Path Mapping
With a clear understanding of asset locations, we perform continuous attack path mapping to identify and visualize potential routes of compromise. This dynamic process helps us understand how an attacker could move laterally within the network to reach critical assets.
Discovery of Material Risk
We begin by analyzing a company's 10-K filing to identify material risks that could impact the business. This financial analysis helps us understand where the most critical data resides and what assets are most vital to the organization.
Continuous Demonstration of Compromise
To provide concrete evidence of vulnerabilities and their potential impact, we demonstrate possible compromises using breach and attack simulations. This step helps in illustrating the real-world implications of identified threats and justifies the need for immediate action.
Quantify Risks and Focus on Material Threats Rather than Attempting to Address Every Potential Issue
Each technology’s output serves as an input to the next, creating a seamless flow that zeroes in on the risks that truly matter.
Attack Surface Management
Vulnerability Management
Attack Path Mapping
Continuous Penetration Testing
Breach and Attack Simulation
Threat Intelligence
A Force Multiplier for Your Security Team
Praetorian's Offensive Experts Permanently Stand Side-by- Side with Our Customer's Defensive Teams
We Consolidate and Save Money
We consolidate attack surface management, vulnerability management, continuous penetration testing, breach simulation, and exploit intelligence into a single cost-effective platform.
We Include Security Experts
Our team of offensive security experts provides continuous support, aligning your security strategy with best practices and emerging threats.
We Are All Signal and No Noise
We prioritize only critical and validated risks, ensuring you focus your time and resources on what truly matters.
We Give Your Team The Ammo It Needs
As an external third party, we help you obtain the buy-in from the business to fix the risks we uncover through demonstration of impact and hard evidence.
We Got Compliance Covered
Our tech-enabled service meets annual penetration test requirements, ensuring compliance and adding value to your security efforts.
We Verify Mitigation
We ensure identified risks are remediated and provide third-party validation, supporting your IT teams every step of the way.