Editors note:
Normally, the Praetorian blog features content pertaining to cybersecurity insights, tools, and techniques. We are proud of the work we do and pleased to share best practices and innovation with our extended community.
But what makes Praetorian special isn’t just our expertise.
We believe that employees care about working in an environment where employees can be themselves, and have a positive impact on society. While work cultures are unique to every organization, the enabler of any thriving culture is the extent to which employees – even the most junior – feel empowered to be engaged, feel valued, and be heard.
At Praetorian, we are committed to and united by our core values. Wondering whether our values are surviving a pandemic where all employees are working remotely, we’ve been looking for evidence in our new hires. Here’s what some of our interns from this past summer had to say.
Interning at Praetorian
By Vineeth Voruganti (Georgia Institute of Technology, Class of 2022)
Interning as a student at a tech company has always been something that is hit-or-miss. Sometimes you are hired and given next to no work to do. So you spend all of your time checking your email and waiting for something to happen. Other times, you’re hired to do menial labor that no full-time employee wants to do.
An internship at Praetorian is not one of those experiences.
After working for several different companies ranging from giant corporations to startups with less than ten employees, I can confidently say that there are few experiences as valuable as my internship with Praetorian.
From day one, you are treated like a regular employee. There is practically no distinction between you and an engineer onboarding full-time. You don’t have restrictions on what part of the office you can access or wear a color-coded lanyard to signify that you’re an intern. There were several occasions throughout the summer when it was assumed that I was a junior engineer, and I had to clarify that I was an intern. However, the comparison to a full-time employee doesn’t stop there; you are treated like a full time engineer and get to work alongside the most senior engineers at Praetorian to learn and contribute to projects. These projects are the same as ones that any regular employee would be assigned. You don’t spend the entire summer working on a tiny widget that may have a vague, indirect impact on the company, but most likely will be discarded after you leave. Rather, you are put on real security assessments on the same cadence as any other security engineer. Every week you can directly see how the work you are doing is impacting both the company and its clients. On every engagement, from start to finish, I was able to play an important role and interface directly with the customer to drive the conversation forward. Praetorian operates with the philosophy that interns should be able to provide value to the company just as much as the company provides value to them. Many other companies that I have worked for have made similar claims, but I have never seen one that is so honest and strives to actually stand by that vision.
Being treated like a real employee may not be ideal if the company is just trying to use you for cheap labor, but Praetorian prevents this by having an intense culture of mentorship and transparency. If there is ever a time where you feel out of your depth, you can easily reach out through multiple channels and get support and mentorship from more seasoned engineers, or just bounce your ideas off of someone else for a sanity check. Throughout my internship, I was never once turned away when asking for help, and often received help from multiple sources at once. The mentorship works on top of the company policy of “default to open”, which makes all of the actions of the organization transparent to the employees. This policy made it such that there was never any confusion about why I was doing a task or if it actually made any impact. I had a clear overview of how all the different parts of the company operated and what direction we were all striving toward. The transparency and support structure in place were invaluable assets to help me acclimate to the work at Praetorian.
Praetorian is one of those rare companies where you can work and not feel frustrated with how everything is organized. Praetorian is a stark contrast to my experience with giant corporations that can be bogged down by endless hoops of bureaucracy that one needs to navigate before getting anything done. On the other hand, Praetorian is also not a small startup with no infrastructure or direction on how to get anything done. They have somehow created a great culture that strikes a balance between fast-paced engineering and staying organized. In my previous positions at other companies, I would occasionally doubt that the company would be able to last, or I’d worry about its future, but I have never once been skeptical about the success and growth while at Praetorian. I would highly recommend Praetorian both to students looking to intern or to anyone looking for a great company to call home.
Reinventing the Summer Internship During COVID-19
By Steve Knabe (University of Texas at Austin, class of 2021)
How can a fun and fulfilling internship be reproduced during a global pandemic? My last internship at Praetorian was filled with countless insightful and valuable in-person experiences. There are very few workplaces where you can gain a plethora of technical knowledge and laugh so hard you cry in a single day. Staff engineers were always available for questions throughout the day and, on game nights, formed the world’s most hilarious comedy club. With the inability to interact in-person, I wanted to devise a plan to replicate last year’s fantastic experience for my fellow interns. Initially, I considered having the interns take turns giving lectures on topics they were passionate about. Lectures are a great way to share knowledge; however, they are mostly unidirectional and struggle to provide a fun, competitive, and engaging experience. On the other hand, doing Capture The Flag (CTF) problems together would be a fun and competitive way to develop personal connections with the other interns; however, we would have to coordinate being online at the same time to solve problems together. Why not have the best of both worlds? An asynchronous internal CTF amongst the interns!
Our northern star for the idea spurred from the ultimate goal of obtaining our OSCPs. Almost every new full-time security engineer at Praetorian obtains their Offensive Security Certified Professional (OSCP) certification within a few months. The OSCP is a reputable exam known for making people “try harder.” Completing the rigorous assessment takes an equal amount of technical skills and perseverance. For any prospective Praetorian engineer, the OSCP is an important focal point; therefore, the 8 of us decided to center our 3 month CTF around it. To create problems that paralleled the exam’s content, we would need an easy way to transport problems of any type, like buffer overflow and privilege escalation. Using Docker, we could transport virtually any problem in a container while learning about relevant and popular virtualization technology. To provide the idea with some structure, we devised the following specifications for our internal CTF: At the start of each week, the current week’s topic and the prior week’s solutions were released. During the week, any intern could release challenges as Docker images for others to try. When someone solved a challenge, they would contact the creator with the flag that they obtained and the steps they took to solve the challenge. Finally, during our weekly team meeting, each creator would walk through the solution for their challenge from the previous week. This structure allowed us to solve CTF-style problems while starting a technical and informal dialog between interns.
Everyone was very excited to create tough problems for their fellow interns to solve. We were constantly bantering about who would have the hardest challenge, laughing about our struggles, and boasting about our latest solutions to each other’s problems. This hilarity spawned from the hand-crafted technical challenges we had deviously made for each other. I asked some of the creators to share the write-up for their favorite challenge.
James Austgen (University of Illinois at Urbana-Champaign, Class of 2022)
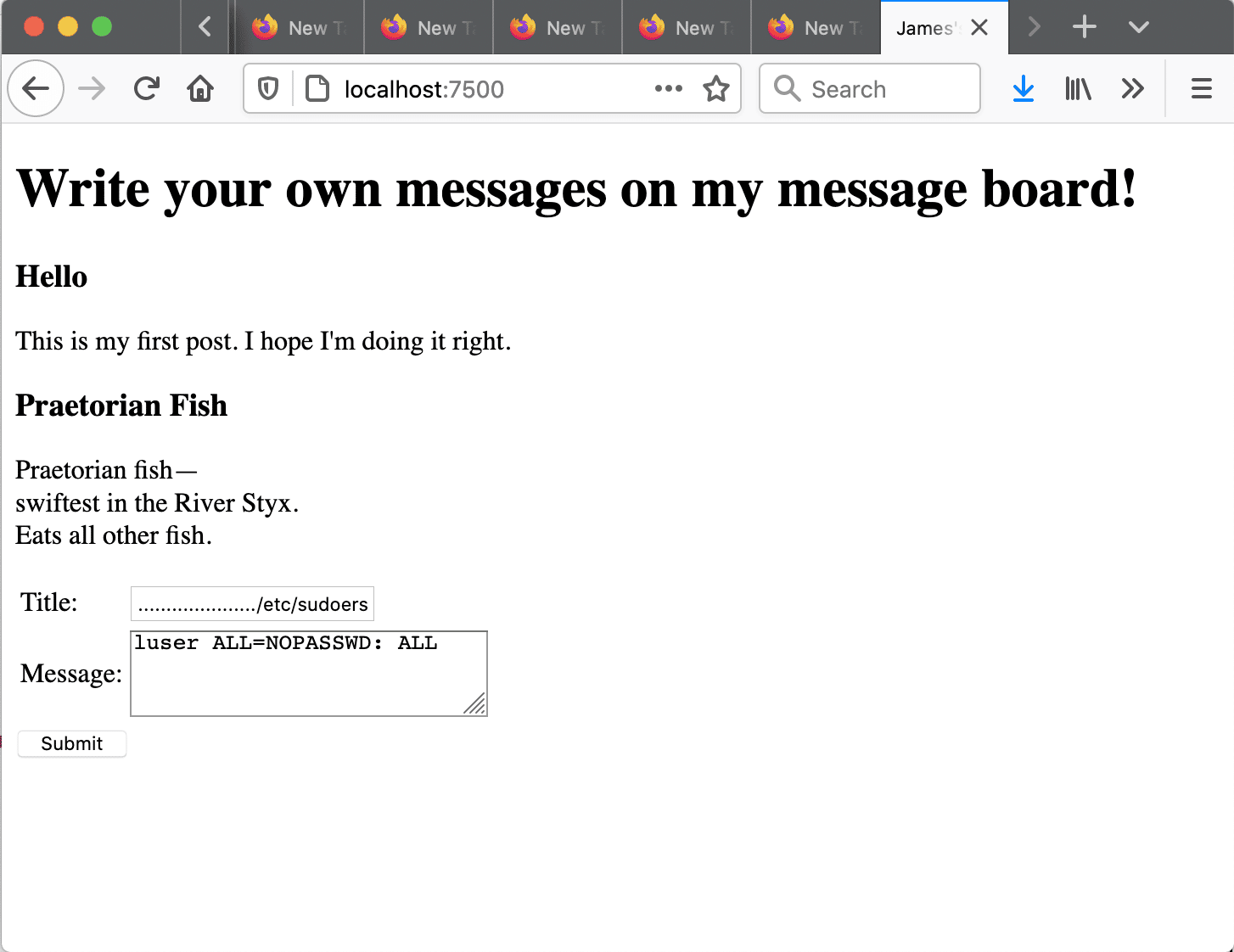
“I created a Docker image that runs a message board service that is vulnerable to privilege escalation. The service operates by saving messages to different files based on the message title. Inspection of the service’s source code, which is readable by the low-privilege user, reveals that the service tries to mitigate arbitrary file writes to other directories by replacing all occurrences of ‘..’ with ‘.’ ten times in the filename when it creates message files. However, the user can bypass this safeguard by including a string of 1,025 periods in a row, which would evaluate to ‘..’ and allow the message file to be written in other directories. Because the web service was running as root, the interns found that they could overwrite either /etc/sudoers or /etc/passwd to escalate privileges and get root access of the machine.”
Garret Kern (Brown University, Class of 2021)
“I wrote a CTF challenge focused around file permissions for a week with a privilege escalation theme. The challenge contained two parts: (1) enumerating a file on the file system to discover the vulnerable binary and (2) exploiting the setuid bit to gain root access. An initial clue on the desktop hinted that there was an insecure binary stored in the /secure_storage folder. However, within secure_storage the user did not have permission to list files. The trick was realizing the permissions were set up so that even though the user could not run ls, they could still cd into folders within /secure_storage. The execute bit on a directory allows cd to be run, even if the read bit is off, which prevents ls from being run. The initial clue hinted that folders within were a series of four numbers, so running “for i in `seq 1111 9999`; do cd $i 2>/dev/null; done” found the folder 1235, which contained a binary with the setuid bit. Running strings on the binary revealed the binary was calling “ls” with a relative path, instead of a more secure absolute path. By creating a file called “ls” which spawns a shell, and adding it to the PATH environment variable, the user could cause this malicious file to be run by the binary instead of the intended, default ls binary. The binary was running with root privileges because of the setuid bit, so when the malicious file was run it spawned a shell as root, giving the user full control of the container.”
Matthew Pabst (University of Texas at Austin, class of 2021)
“My problem incorporates a couple of concepts into a single container, including using the Shellshock vulnerability to trigger code execution and privilege escalation through the sticky bit of Unix-style permissions. The objective of the challenge is to find and print the flag, which resides in a file named “flag.txt” somewhere in the file system. Checking the logged-in user’s home directory reveals the “giveflag” binary, which cannot be run by the current user. Inspecting the permissions of the binary reveals that the binary is owned by root and the sticky bit is set, meaning the program will run as the root user. Additionally, the binary belongs to the group “www-data”, the default user for Apache web servers. Progressing further in the challenge requires identifying a local web server, whose default page links to “/cgi-bin/shocking.sh”. CGI scripts are generally stored in “/usr/lib/cgi-bin”, and inspecting this directory reveals the contents of the script. The script appears to use an older version of bash: version 4.3. A quick Google indicates that this version of Bash was vulnerable to the Shellshock vulnerability, which allows the contents of specially crafted environment variables to execute code. When the Apache webserver runs CGI scripts, it sets environment variables such as “HTTP_USER_AGENT” based on the headers of web requests. As a result, an attacker could craft a malicious “User-Agent” header that would execute code as the “www-data” user. Here is an example of using curl to send a malicious payload that will execute the “giveflag” binary, which will dump the flag: curl -A “() { echo hello; }; echo; /home/shelly/giveflag” http://127.0.0.1/cgi-bin/shocking.sh”
During this pandemic, developing the same level of personal relationships I made last year has been incredibly challenging; however, our internal CTF has helped us connect, challenge, and understand each other. Praetorian’s game nights, internal CTF, and internal educational meetings, like our vulnerability show and tell, help to connect a remote workforce and recreate last year’s amazing experience. Ultimately, our internal CTF has both facilitated this connection and taught me about deployment, virtualization, and common vulnerabilities.
Conclusion
Our summer interns returned to a very different University experience than they found a year ago. No nation, no business, no person has escaped the impact of COVID-19, and the pandemic is certain to have long-lasting effects for everyone. At Praetorian, we continue to work remotely, to serve our customers the best we can, and grapple with the next normal. We are encouraged from these stories from our interns – an indication that a strong company culture can and will transcend these challenging times.