Introduction
“You want someone to check whether you’re vulnerable – all the bloody time.”
We spend a lot of time talking with our customers. We loved this quote for how directly it strikes at a sentiment we’ve heard across our base for several years now.
Reactive security is reaching maturity, as evidenced by the number of multi-billion dollar companies in IR, EDR, NDR, AV, and similar markets.
But by definition, attackers will always be one step ahead. Modern organizations need a proactive complement that eliminates risks before attackers can. Unfortunately, proactive solutions are far less mature.
It’s 2024. Your already overburdened team doesn’t need another dashboard, new data, or more tools.
You need somebody or something to wade through the quagmire of vulnerabilities and pinpoint the risks an attacker can use to compromise your business.
Of the 50,000 things you can focus on, what are the 5 things you must focus on?
Continuous Threat Exposure Management (CTEM, pronounced “see-tehm”) is a framework that answers this question. CTEM is a five-step cycle that moves organizations beyond compliance and traditional vulnerability management to continuously discover and address material risks. Rather than promoting a new alphabet-soup toolkit, CTEM improves efficiency between existing processes.
Note: Security practitioners analyze many issues: vulnerabilities, weaknesses, misconfigurations, alerts, etc. Here, we refer to them all as “vulnerabilities”.
This article provides a brief introduction to understanding and implementing CTEM. While not a comprehensive guide, it is a good starting point for practitioners with vulnerability management programs that need reform.
Why CTEM?
CTEM is best defined by the problems it solves. Reviewing the state of vulnerability management serves as a helpful starting point for the rest of this eBook, but if you already agree that traditional vulnerability programs are broken, feel free to skip this section.
Enterprises continuously grow in size and complexity. Increased cloud presence and faster development cycles ensure attack surfaces constantly change, exposing new vulnerabilities daily.
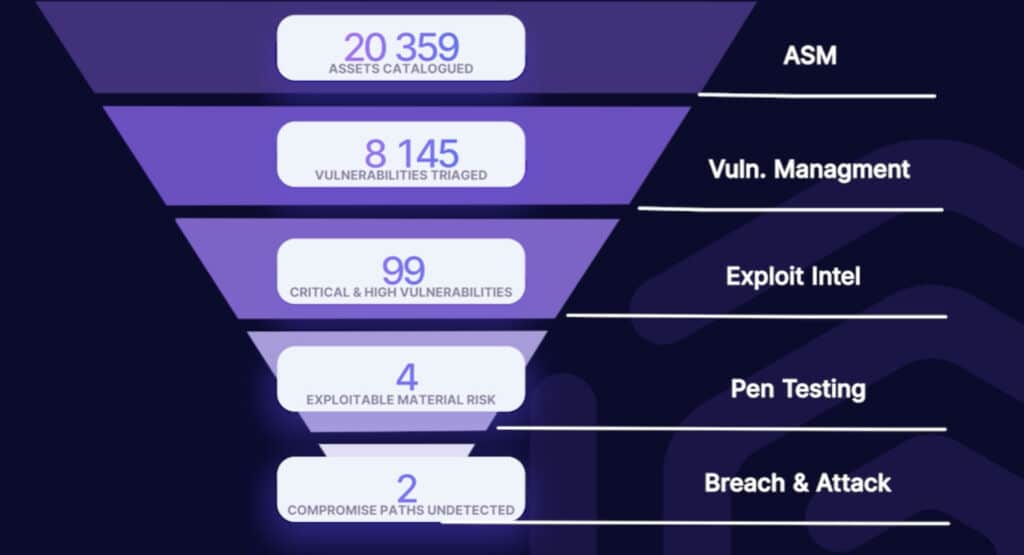
Traditional vulnerability management tried to scale by boiling oceans, generating more vulnerabilities than teams could handle. While most of this is noise, it’s unclear how to separate noise from signal, resulting in considerable wasted time and budget.
Believe it or not, too much data is a good problem. The root issue is isolated datasets, collected by tools that address narrow tasks. No individual dataset directly finds material risks, and after running an enterprise security solution, you’ve probably wondered “Now what?”
From a CTEM perspective, these datasets are inputs. They do not help you find risks in isolation, but if effectively tied together, material risks become clear.
What is CTEM?
CTEM is a risk management framework created by Gartner to describe the emerging continuous security market.
CTEM succeeds where traditional vulnerability management failed for several reasons:
- It prioritizes vulnerabilities with factors beyond CVSS, such as asset context
- It engages stakeholders across the organization early to facilitate later remediation
- It tests continuously to find risks as soon as they appear
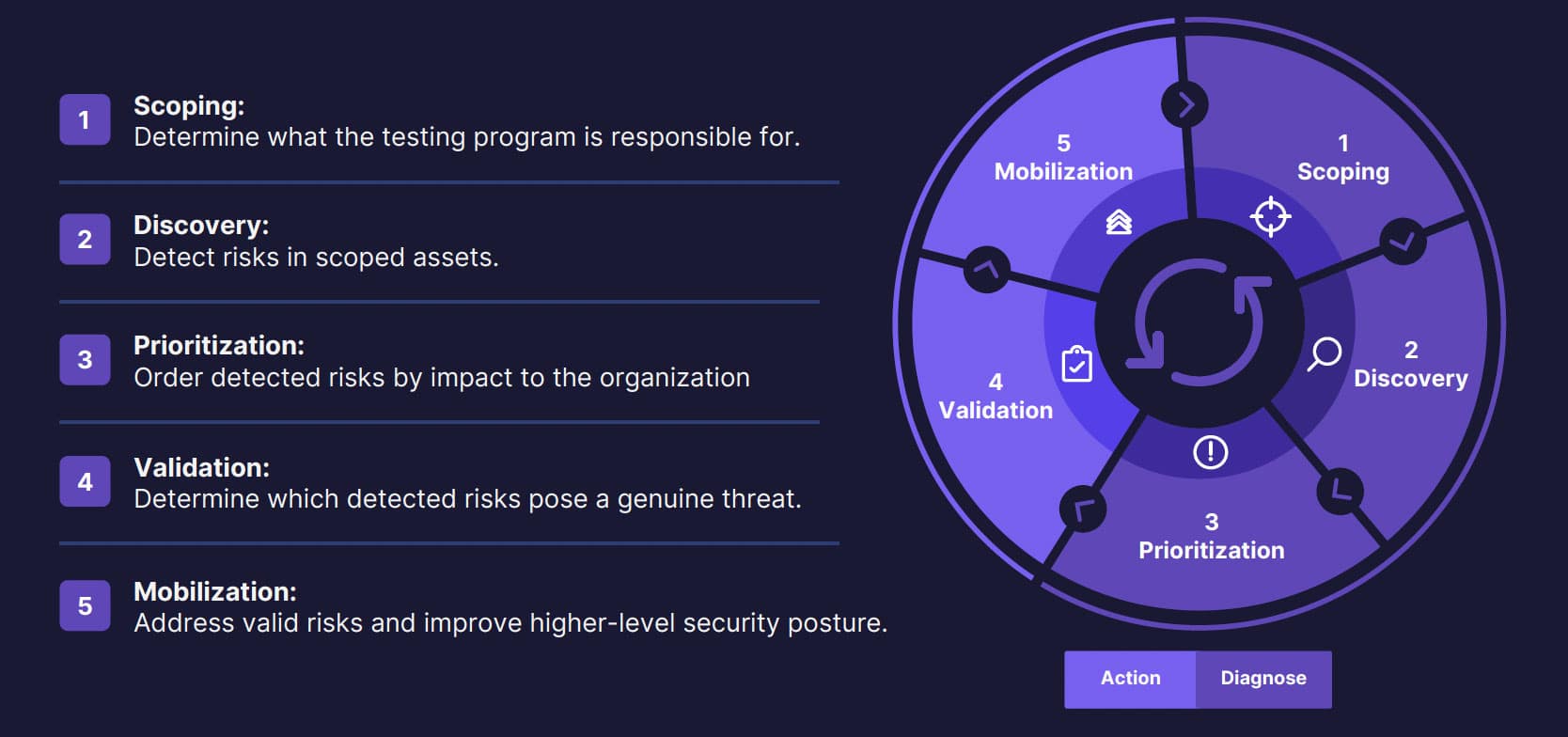
CTEM consists of five steps, working in tandem.
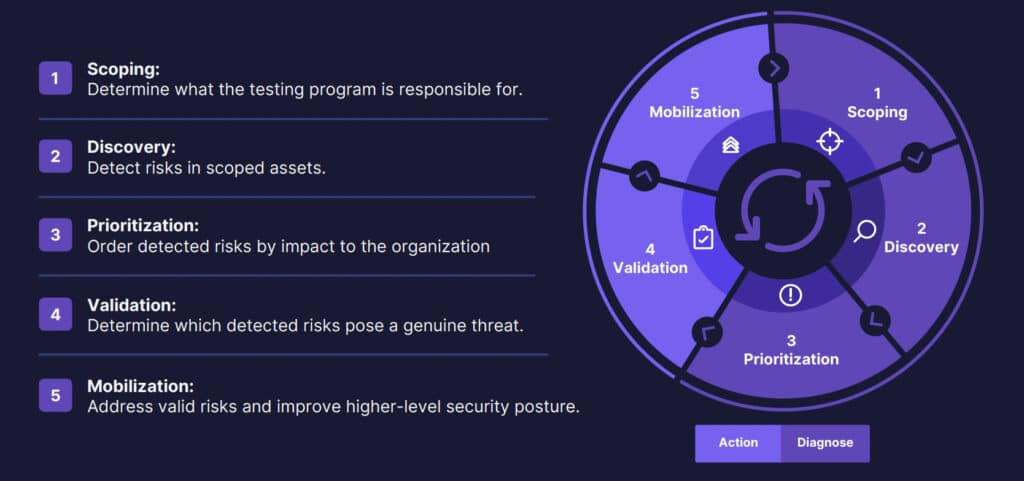
For the next few moments, let’s take a closer look at each of the five stages to gain a better understanding of what each phase means to the CTEM process and how they can be implemented within your CTEM process.
Scoping
The first phase of the Continuous Threat Exposure Management (CTEM) framework is scoping. The goal within this phase is to determine an organization’s most critical assets while measuring against business priorities and the potential impact of a breach.
Unlike traditional vulnerability management, CTEM takes a holistic approach from the perspective of an attacker. By viewing an environment from this vantage point, Security teams can work with leaders throughout the organization to creatively consider all potential entry points such as cloud infrastructure, code repositories, and integrated 3rd party supply chain networks which all pose significant risk to an organization.
CTEM uses business objectives to scope security testing. At a high level, this includes:
- Engaging stakeholders across your organization to understand core business objectives
- Engaging IT to map business objectives to cyber assets
- Ranking all assets in order of importance to your business
- Selecting the top subset your security team has resources to support
Note: It’s OK if step 4 leaves you with an uncomfortably short list. Your program will become more efficient as it matures. Start with the most important assets, and gradually expand.
Discovery
The second step of the CTEM framework is the discovery phase. The primary goal of this phase is to map scoped assets to live systems and thoroughly scan these systems for vulnerabilities. While many security teams are already familiar with robust discovery processes, CTEM elevates the level of comprehensiveness and frequency.
The process typically unfolds in three key steps:
- First, all scoped assets and environments undergo scanning for live systems, often utilizing port scanning and Attack Surface Management (ASM) tools.
- Next, the identified systems are scanned for vulnerabilities using a combination of automated vulnerability scanners and manual penetration testing techniques.
- Finally, all asset and vulnerability data is meticulously collected and stored in a centralized database for further analysis.
What sets CTEM’s discovery apart from traditional vulnerability programs is its frequency. In the CTEM framework, both automated and manual testing runs continuously, 24/7. This constant awareness and visibility ensure that new vulnerabilities are identified almost as soon as they appear, providing a real-time view of the organization’s security posture.
However, this intensity of discovery raises a valid concern: How can security teams manage this constant flood of data without becoming overwhelmed? To answer this, we must look at the subsequent phases of CTEM, particularly phase three, Prioritization.
Prioritization
The third step of a CTEM program is Prioritization. At this point, the program is focused on highlighting vulnerabilities likely to pose a material risk. Acknowledging the reality that it’s impossible to fix everything, CTEM aligns resources to the most critical vulnerabilities.
To achieve this, organizations must design a risk-rating schema that incorporates scores for severity (CVSS), exploitability (EPSS), and business context (e.g., asset function).
It can also consider additional factors such as:
- Mitigating controls
- Business impact
- Importance in other attack paths
- Remediation cost
- Vulnerability age
The goal is to automate the prioritization of each vulnerability before dedicating manual effort. We’ve seen organizations use everything from simple formulas to machine learning. Fine-tuning the schema is difficult, so expect considerable experimentation.
Leverage offensive experts here (pen testers, red teamers, etc.). Your schema approximates each vulnerability’s usefulness to an attacker, while offensive engineers often have critical insights that defenders do not.
Offensive experts should periodically review your vulnerability queue. Manual review is a great opportunity to test your schema and collect misprioritizations to inform continuous improvements.
By targeting an approach in this way, security teams begin to optimize resource allocation, allowing them to focus their efforts on the most critical material issues first. The outcome is a more efficient and effective vulnerability management process that aligns closely with real-world threat landscapes and business priorities.
Validation
The primary goal of the Validation phase is triaging all vulnerabilities by priority. While this phase shares similarities with a traditional validation process, it introduces significant enhancements for gained effectiveness and efficiency.
The validation process involves:
- Researching each vulnerability
- Attempting to detect or reproduce it within the organization’s environment
- Accept or reject the vulnerability based on the results
CTEM provides significant improvement in this process because the analysts now work through a prioritized queue of vulnerabilities, ensuring that the most critical issues are addressed first.
This prioritized approach is particularly valuable when organizations employ machine learning models for their prioritization schema. In such cases, the analysts’ responses during the validation phase become an invaluable source of training data, continuously refining, and improving the model’s accuracy.
Additionally, CTEM validation moves beyond periodic scan cadences to implement continuous testing and validation of defensive controls, configurations, and processes. This ongoing assessment ensures that the organization’s security posture remains robust in the face of evolving threats.
The validation phase in CTEM combines automated tools with manual techniques, including Breach and Attack Simulation (BAS) and penetration testing, to simulate real-world attack scenarios. This comprehensive approach provides tangible evidence of the organization’s security strengths and weaknesses, bridging the gap between theoretical risk assessment and practical security implementation.
Mobilization
The fifth and final phase of CTEM, Mobilization, is when the rubber meets the road and strategic planning moves to concrete action with the primary goal of addressing identified vulnerabilities. This stage significantly differentiates CTEM from legacy vulnerability management approaches by emphasizing the critical importance of actually mitigating risks, rather than merely identifying them.
In this phase, security teams focus on three key components:
- Planning detailed remediation steps
- Effectively communicating these steps along with Service Level Agreements (SLAs) and retesting processes to IT and DevOps teams
- Collecting data for higher-level analyses.
The effectiveness of Mobilization is greatly enhanced when IT counterparts are engaged from the initial scoping phase, fostering a sense of shared responsibility, and facilitating smoother remediation processes later on.
Mobilization should place significant emphasis on data collection. Building a comprehensive historical risk database is essential for measuring changes in the organization’s security posture over time and quantifying the return on investment (ROI) of various security initiatives. This data-driven approach enables organizations to make informed decisions about resource allocation and future security strategies.
What Are Analysts Saying About CTEM?
Analysts believe the security industry is moving toward a continuous model that focuses on high-impact risks.
Perhaps the most bullish perspective comes from Gartner:
“By 2026, organizations that prioritize their security investments based on a continuous exposure management program will be 3x less likely to suffer a breach.” 1
Gartner also labeled CTEM as “transformational” in its 2024 Security Operations Hype Cycle.2
The transformational benefit is in improved prioritization. Security teams cannot fix everything. Rather than boiling oceans, teams must focus their efforts on the areas of highest return. Forrester considers prioritization a core part of exposure management:
“Exposure management is a platform that consolidates vulnerabilities and exposures with an organizational perspective, maps them on an attack path, and identifies choke points for remediation teams to prioritize.” 3
CTEM also avoids data overload by connecting disparate solutions. Isolated point products – like ASM, VM, or BAS – do not reliably find material risks. As discussed in the 2024 Forrester Wave:
Attack Surface Management Solutions, each solution provides just one piece of a larger puzzle, requiring connective tissue.CTEM is that connective tissue.
A Look at Today’s CTEM Landscape
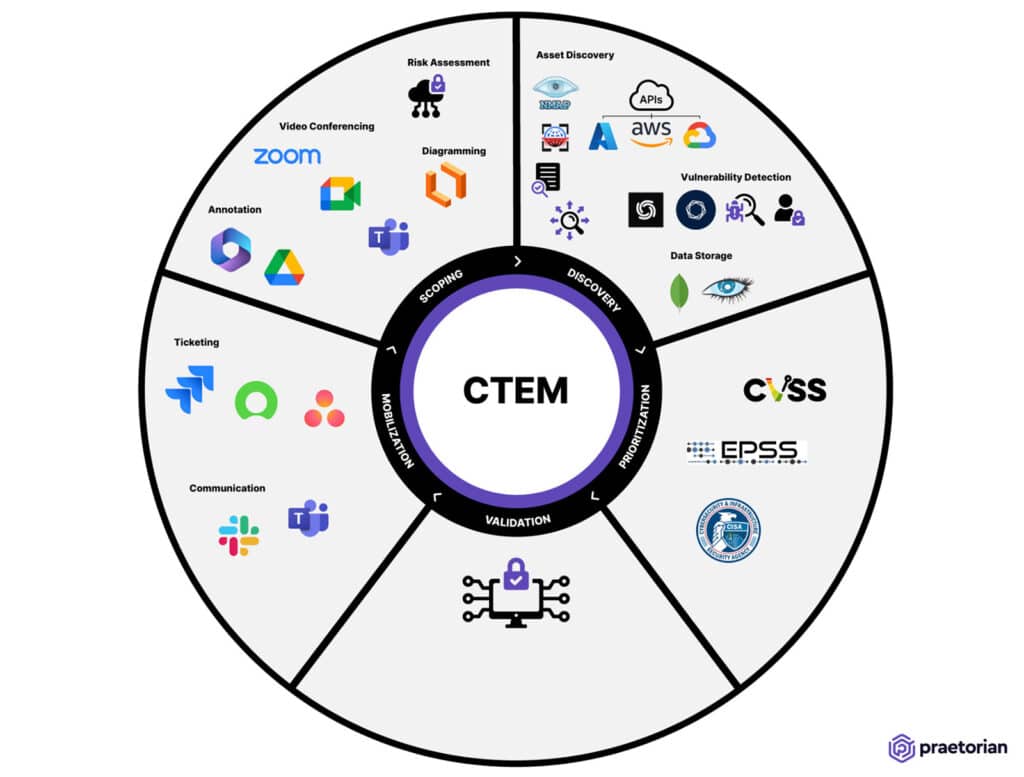
Because of CTEM’s emphasis on business context and internal stakeholders, it is impossible to fully outsource. Still, organizations can leverage vendors to cover significant portions of CTEM, including most or all technology solutions.
The chart above provides an introduction to implementing CTEM by listing relevant tools, vendors, and processes for each step. We will also briefly discuss vendors who provide turnkey platforms that cover multiple CTEM steps.
Purchasing From a Vendor
Some practitioners may not have sufficient time or staff to implement CTEM internally. In these situations, leverage vendors who support multiple CTEM steps.
Praetorian
Solution Name: Chariot
CTEM Categories: Discovery, Prioritization, Validation (* human-reviewed)
Solution Description:
Praetorian believes organizations need outcomes, not tools. Chariot is a managed service platform that allows customers to augment their security teams with Praetorian’s expert staff. The platform uses multiple offensive point products (ASM, BAS, VM, and more) and integrations with third-party platforms to centralize customer security data into one location. The Chariot team then uses its offensive expertise to triage the data, conduct continuous penetration testing, and ultimately show organizations where they are at risk.
Pentera
Solution Name: Pentera Platform
CTEM Categories: Discovery, Prioritization, Validation (* automated)
Solution Description:
The Pentera Platform is an Adversarial Exposure Validation (formerly Breach and Attack Simulation) platform. Users input their assets’ IP ranges, and Pentera launches a continuous suite of adversary procedures. When a chain of successful procedures reaches a critical asset or goal, Pentera notifies your security team. Pentera visualizes successful procedures as an attack path and provides remediation advice that targets the root cause of the attack path.
Rapid7
Solution Name: Exposure Command
CTEM Categories: Discovery, Prioritization
Solution Description:
Exposure Command combines Attack Surface Management and Vulnerability Management into one platform. It uses automated discovery capabilities and integrations with third-party solutions to collect and centralize your security data across external, internal, and cloud environments. Users overlay assets with business context, and Exposure Command uses this contextual data, alongside CISA KEV and other intelligence feeds, to prioritize risks for remediation.
XM Cyber
Solution Name: XM Cyber Platform
CTEM Categories: Discovery, Prioritization
Solution Description:
XM Cyber uses native discovery capabilities and third-party integrations to identify vulnerabilities in your environment. XM Cyber works against environments in on-premise networks and all three main cloud providers (AWS, Azure, GCP). XM Cyber organizes vulnerabilities into attack paths and overlays these paths onto a single graph to identify vulnerabilities that enable multiple paths. It uses these intersections, alongside vulnerability severity and business context, to prioritize remediations.
Conclusion
It’s widely accepted that traditional vulnerability management has not adapted to the challenges of modern enterprises.
But cybersecurity has a lot to look forward to. Vendors are listening to their customers to provide increasingly effective solutions at affordable price points. Defensive capabilities are improving every day. Inch by inch, we move closer to a future without compromise.
We believe Continuous Threat Exposure Management is a critical part of that future. Attackers are constantly on the prowl for exploitable risks, but with CTEM, your security program will be just as diligent.
1 How to Manage Cybersecurity Threats, Not Episodes
2 Gartner Hype Cycle for Security Operations, 2024
3 Exposure Management Looks To Usurp Vulnerability Management, But Is The New Emperor Wearing Any Clothes?