In the world of wireless communications, security vulnerabilities in implemented protocols can
remain hidden behind layers of complexity. What appears secure due to the intricate nature of
RF communications may harbor fundamental weaknesses. Let’s dive into a fascinating case
that reveals how a seemingly minor cryptographic weakness in frequency hopping algorithms
can compromise an entire wireless communication stream.
Understanding Frequency Hopping
Before we dive into the vulnerability, let’s understand what frequency hopping is and why it’s
important.
Frequency hopping spread spectrum (FHSS) is a method of transmitting radio signals by rapidly
switching between different frequency channels according to a predetermined or calculated
sequence known to both the transmitter and receiver. Think of it like two people having a
conversation where they constantly switch between different languages, but both know
precisely when to switch and which language to use next.
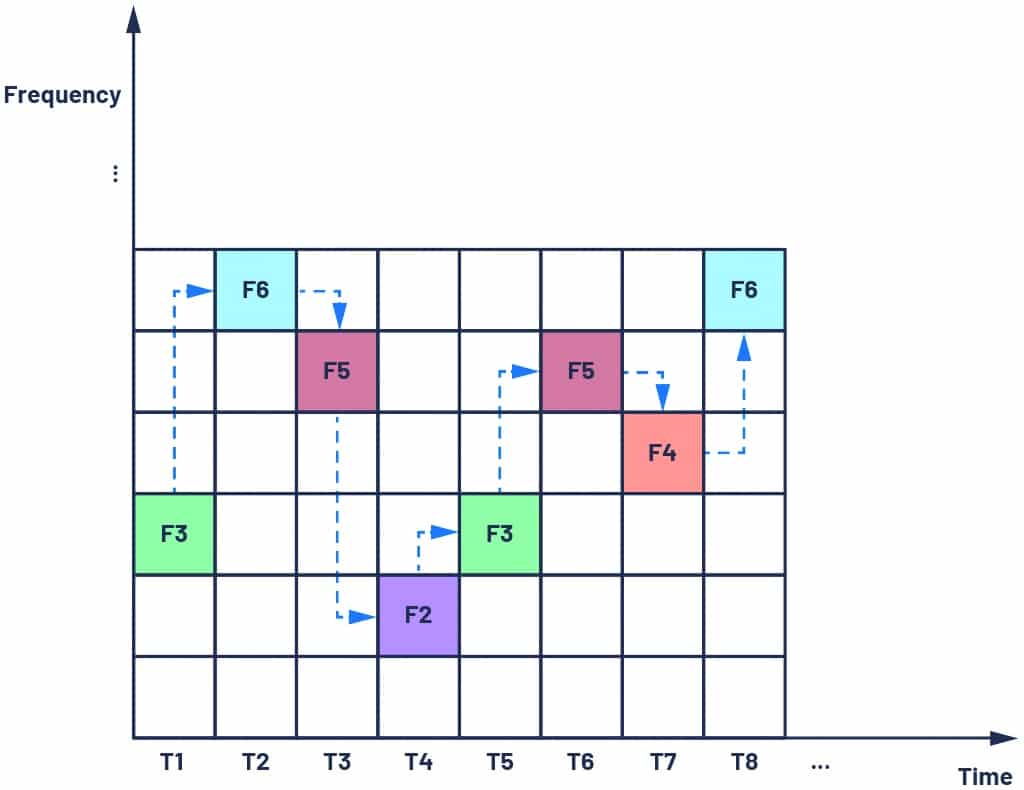
frequencies over time. *Original Source: https://www.mpdigest.com/2022/05/27/the-next-gen-software-defined-radio-sdr-transceiver-delivers-big-advances-in-frequency-hopping-fh/
The technique was famously co-invented by actress Hedy Lamarr and composer George
Antheil during World War II. They utilized a piano roll as a mechanism to switch between 88
frequencies as a way to prevent radio-guided torpedoes from being jammed. Today, frequency
hopping serves several crucial purposes:
- Interference Resistance: By constantly changing frequencies, devices can avoid consistent interference on any single channel.
- Coexistence: Allows multiple devices to share the same frequency band with minimal interference.
- Channel Diversity: The continuous changing of frequencies adds complexity to signal interception, though this alone should not be relied upon for security.
The Setup: RF Devices in the Wild
Praetorian discovered this vulnerability in a device that used Nordic Semiconductor’s Enhanced
ShockBurst protocol for communication in the 2.4 GHz frequency band. The device also
implemented a custom packet protocol, which is encapsulated and transmitted over RF using
Enhanced ShockBurst. The custom packet protocol, not the Enhanced ShockBurst protocol,
implements frequency hopping, led by the transmitting device and followed by the receiving
device.
An example of the payload structure is shown below:
| PACKET_HEADER | DATA | CHECKSUM | PRNG | PACKET_END |
Breaking Down the Device Frequency Hopping Process
The frequency hopping process, designed and implemented by the device manufacturer,
follows a simple sequence. The process steps, with modified or redacted functions, are as follows:
- The transmitting device starts with a partially random PRNG value. 8 bits out of 17 are a
fixed value at initialization. - It increments this value using a non-random function and uses it to determine the next
channel:PRNG = next(PRNG) - The current PRNG value is transmitted along with the data.
- The receiving device uses this value to calculate which channel to listen on next:
Channel = PRNG[1] & 0xAB | PRNG[0] & 0xCD - Both devices switch to the new frequency.
- The process repeats from steps 2 to 5.
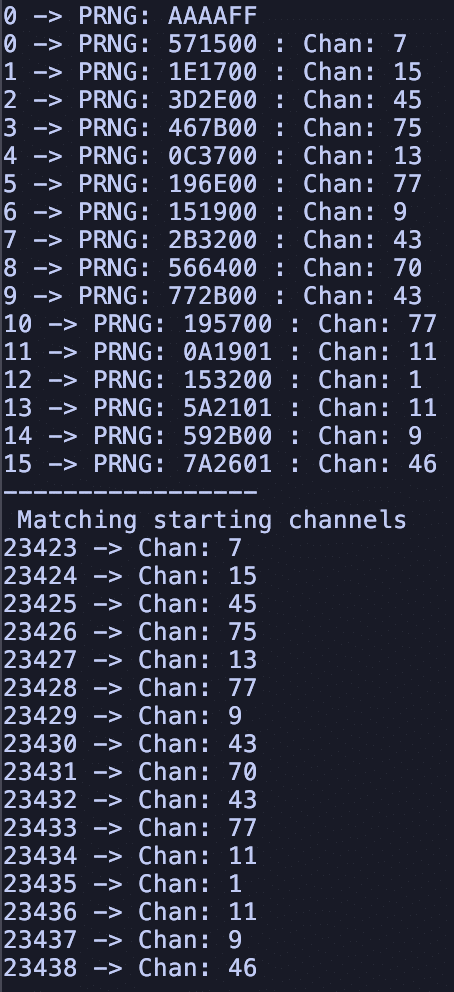
With a test program, we can follow this process to simulate the frequency hopping channels
selected:
The Vulnerability: Predictability in Randomness
The core issues lie in how these devices generated their frequency hopping patterns and the
receiving device’s inherent trust of packets received. This system has several weaknesses:
- The device’s initial PRNG values contained only 9 bits of randomness.
- The device incremented values using a predictable and repeatable function.
- The receiving device accepted values without verifying the authenticity of the transmitter.
- The pattern repeated after 23,423 iterations, leading to observable patterns by adversaries.
To explain simply, an attacker could map all 512 possible combinations (2^9 bits) of initial
PRNG values and their repeating patterns. After capturing a subset of RF data, the attacker
could then determine the complete frequency hopping sequence to predict and track the
transmitter.
Why This Matters
After collecting sufficient samples of the frequency hopping pattern, an attacker gains the ability
to predict the exact sequence of channels that devices used for communication. This
predictability removed the primary benefit of frequency hopping by converting a complex,
random pattern into a deterministic sequence.
Armed with this knowledge, a malicious actor could systematically track transmissions across
different frequencies and intercept sensitive data protected by the frequency hopping
mechanism. Even more concerning is the potential for active attacks: an attacker could inject
false data packets into the communication stream to redirect receiving devices to attacker-
controlled frequencies, effectively hijacking the communication channel.
This vulnerability transformed a seemingly secure frequency hopping communication system
into something akin to a simple, fixed-frequency transmission that an attacker could track and
manipulate. The system’s reliance on a predictable PRNG sequence created a fundamental
weakness that undermines its security model, regardless of any other security measures that
might be in place.
The Fix: Modern Cryptographic Approaches
Modern security practices recommend a more robust approach to frequency hopping that combines temporal elements with proper cryptographic principles. At its core, the ideal solution uses both a shared secret key and synchronized time to determine channel selection. Developers can implement this by passing current time and a pre-shared key through a cryptographic hash function to generate the next channel in the sequence.
While this approach significantly improves security, it does introduce additional complexity. Time synchronization between devices becomes critical – both transmitter and receiver must maintain closely aligned time references to calculate the same channel sequence. This requires careful consideration of:
- Initial time synchronization during device pairing.
- Handling clock drift between devices.
- Recovery mechanisms when synchronization is lost.
- Tolerances for slight timing mismatches.
Additional security measures should also be implemented to create a comprehensive security solution:
- Secure key exchange mechanisms during device initialization.
- Proper encryption or signing of transmitted data.
- Protection against replay attacks through time-based verification.
- Regular rotation of cryptographic keys.
The added complexity of time synchronization is a worthwhile trade-off for the security benefits gained. This approach transforms the frequency hopping sequence from a predictable pattern into one that requires knowledge of the secret key and the current time to determine the next channel.
Lessons Learned
This case study highlights several important security principles:
- Randomness in security systems must be cryptographically secure.
- Simple patterns, even when obscured, can be broken with enough observation.
- Connected device security requires thorough review and testing.
- Proper cryptographic practices are essential, even in seemingly simple applications.
Conclusion
This vulnerability serves as a reminder that security through obscurity is not security at all. When implementing wireless protocols, even seemingly complex mechanisms like frequency hopping must be built on solid cryptographic foundations. The case demonstrates how a slight weakness in random number generation can cascade into a complete communication stream compromise.
For manufacturers and developers of wireless devices, this underscores the critical importance of security reviews, proper cryptographic implementations, and the need to treat every aspect of the communication chain as a potential attack surface. As our world becomes increasingly wireless, the lessons learned from such vulnerabilities become ever more valuable. When implementing wireless security features, remember: cryptographic randomness matters, trust must be earned through verification, and simple patterns will eventually be broken.
Share via: