Gladius: Automatic Responder Cracking
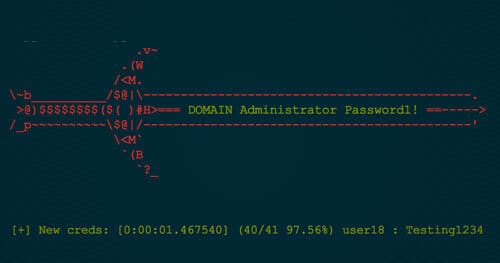
So there you are, performing your internal penetration test, using Responder to potentially grab hashed credentials and thinking "Responder is awesome… but manually cracking credentials isn’t fun." Well, welcome Gladius! Gladius happily listens for Responder hashes (and.. spoiler alert.. secretsdump.py and hashdump) and automatically passes them to hash cat. At its core, Gladius listens in target directories for file events and then performs computations based on the event. Let’s walk through the Responder workflow with Gladius.