Hob0Rules Released: Statistics Based Password Cracking Rules
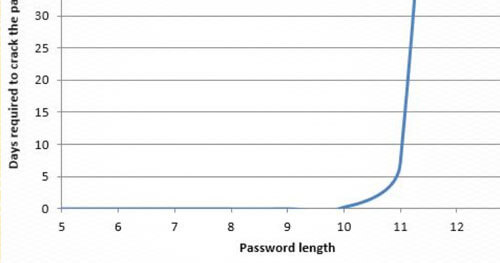
It’s now 2016 and people are still decisively using poor, predictable passwords. Employees around the world will soon be appeasing their mandatory 90-day password rotation by changing their password from ‘Winter2015’ to ‘Spring2016’. This happens in nearly every company – you would be surprised. Previously, I conducted password research to determine common traits of passwords, which was presented at various conferences. The password cracking rules that Praetorian utilizes for all hash cracking have now been released for Hashcat (described below) which are based on these findings. A quick compromise list of 64 of these rules have been released as hob064 and a more extensive ruleset has been released as d3adhob0 for public use. These rulesets were made to compete against their industry standard counterparts, Best64 and d3ad0ne. Both of the released rulesets have bypassed their counterpart in both time speed and number of hashes cracked and will continue to improve. The two sets of rules are living lists and change as the environment of passwords changes.