Active Directory Visualization for Blue Teams and Threat Hunters
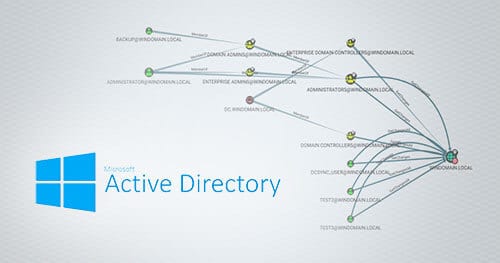
As a network defender, it can be easy to attribute a certain degree of omnipotence to attackers. Advanced threats have an uncanny knack for figuring out how to move through an environment without regards for passwords, roles, permissions, or what “should” be possible.