Signing and Encrypting with JSON Web Tokens
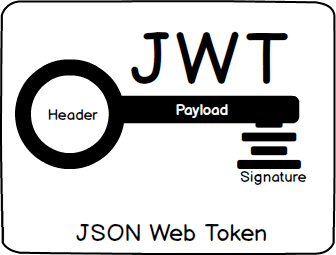
Cryptographic weaknesses often arise in applications when the core security concepts are misunderstood or misused by developers. For this reason, a thorough review of all cryptographic implementations can be a juicy target when designing an application or starting a security assessment. Often, cryptography is used in the context of communication (e.g. a key exchange or […]