Framework Selection: How to Architect a Systematic Security Program – Part 1
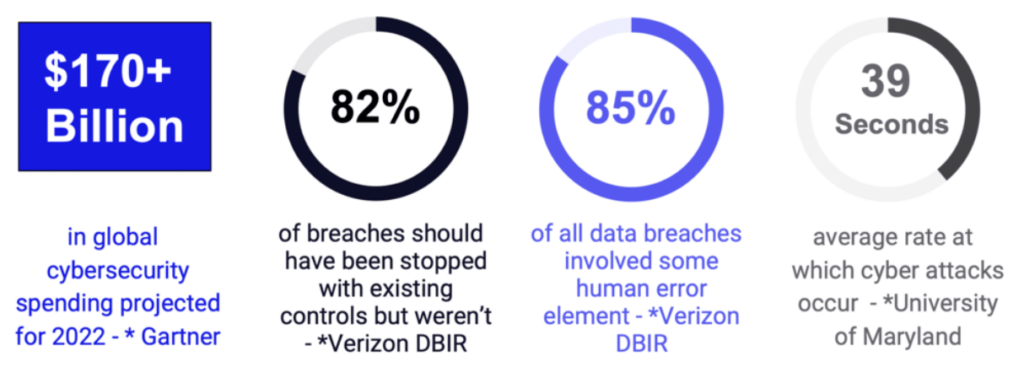
A need for public trust in information systems has driven continuous technological advances and new regulatory requirements, which have in turn made the global cyber threat landscape more complex and connected (see figure 1). As Boards of Directors, regulators, and the public become more aware of this interplay, organizations will need to evolve to address […]