Back to the 90s: Fujitsu “IP series” Real-time Video Transmission Gear Hard Coded Credentials
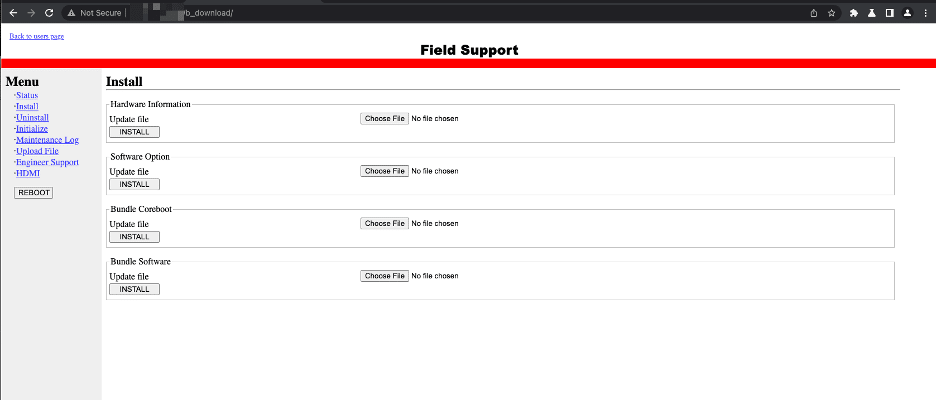
Overview In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities that are likely to impact the security of leading organizations. Exposed embedded devices are a particular area of concern because they typically do not have host-based security controls such as EDR or Antivirus, but still […]