Long Live the Pwn Request: Hacking Microsoft GitHub Repositories and More
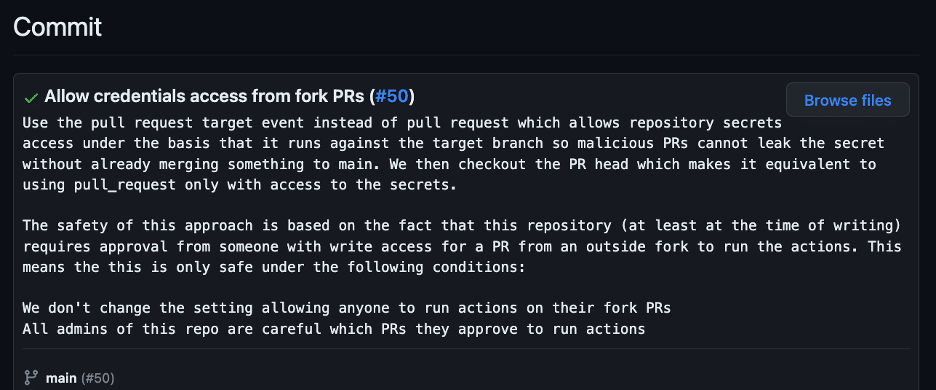
Software supply chain attacks have been increasing both in frequency and severity in recent months. In response to these attacks, the CISA has even released a cybersecurity information sheet (CSI) on how organizations can secure their CI/CD pipelines. The introduction to the CSI states: “(The) CSI explains how to integrate security best practices into typical […]