Overview
Nowadays, the convenience of streaming applications on our mobile and web applications has become an integral part of our entertainment experience. However, this experience can come at a cost if we overlook the security of these applications. In this blog post, we will delve deeper into a critical account takeover vulnerability discovered by our team while assessing a streaming platform. During the assessment, we found that the streaming application utilized a weak email-based login workflow, allowing us to take over any account on the platform. This incident underscores the prevalence of ’Insecure Authentication’, a common issue highlighted in OWASP’s Top 10 Mobile and Web.
Identifying the login workflow and exploiting the weakness
The web and the mobile application used identical login workflow, which includes the following three steps:
- The user types in the registered email address on the web or the mobile app.
- The server verifies the registered email and sends the login link to the email provided.
- The user clicks on the link and accesses the streaming services.
While accessing the application, our team discovered a flaw in the workflow that allowed us to take over any account.
In the first step, when the user enters the registered email, a login challenge is generated locally in the client-side application instead of the server. On further investigation, we discovered that there is no correlation between the login challenge and the email address.
In the second step, we discovered that after verifying the email, the client side sent a request to the server containing the login challenge and the email address, and the server sent the login link to the email address.
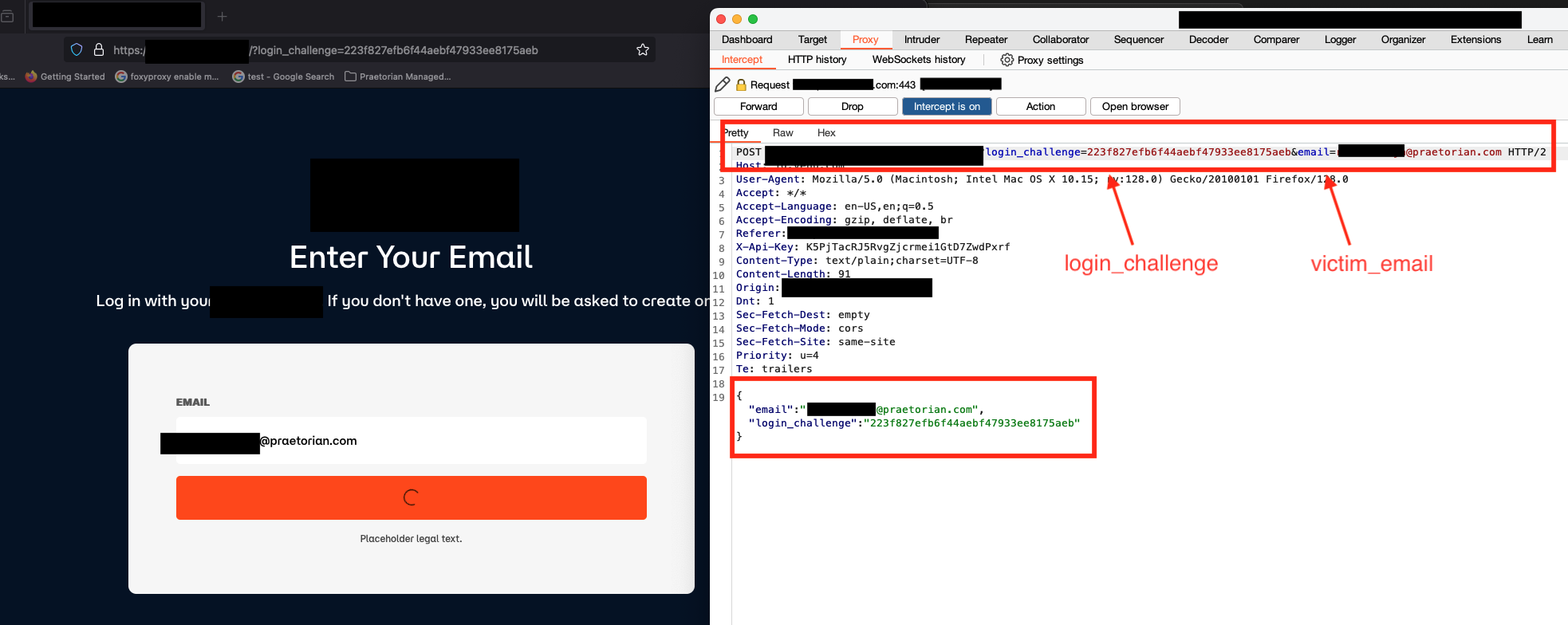
So, we chained the two vulnerabilities together. Since there was no correlation between the login challenge and email address, we manipulated the victim’s genuine email address to an attacker controlled email address, hence acquiring the login link and the unauthorized access to the victim’s account. Refer Figures 1-4
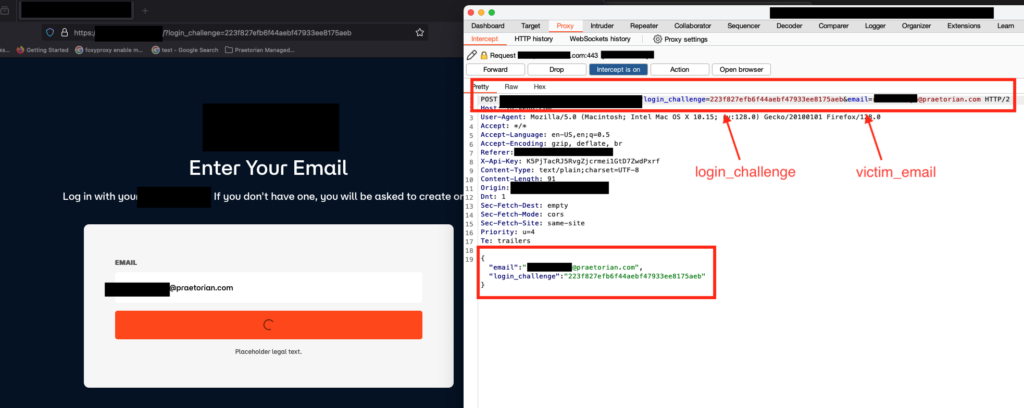
Figure 1: The attacker intercepted the benign Request with login challenge and victim email
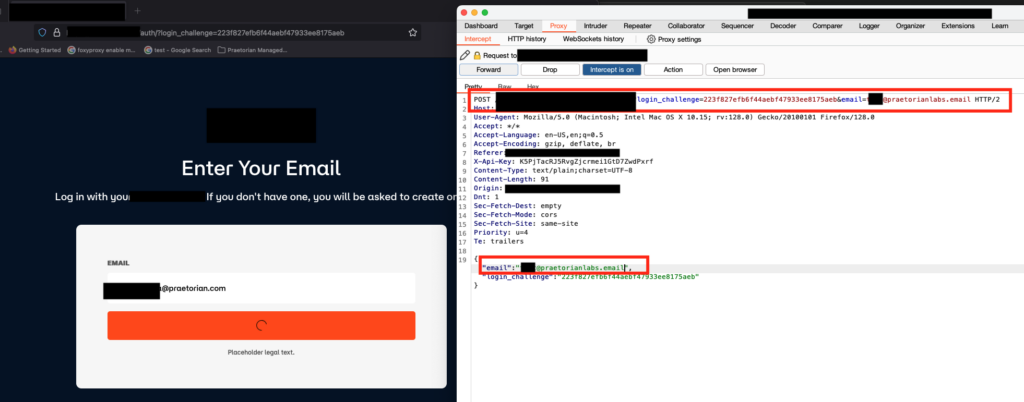
Figure 2: The attacker modified the request with login challenge and attacker email
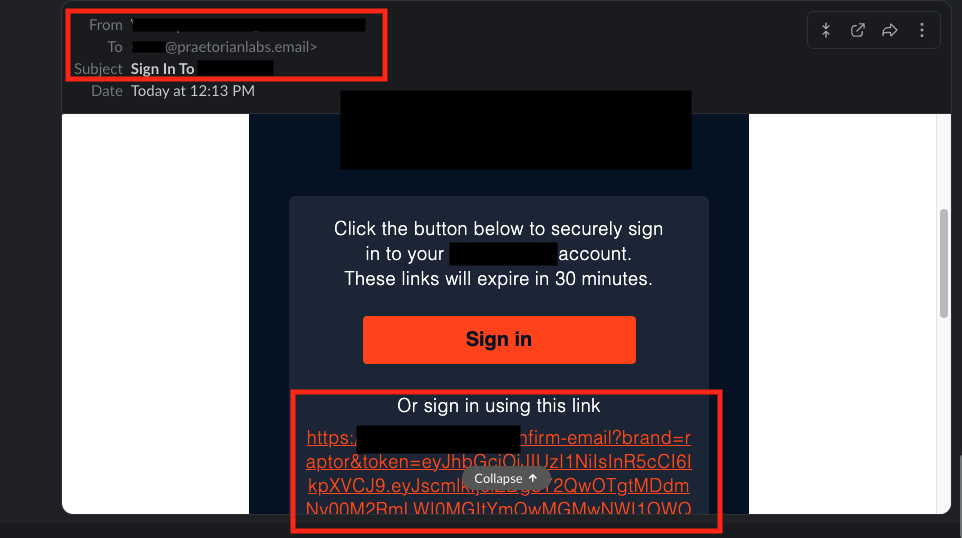
Figure 3: The attacker received the email with the login link
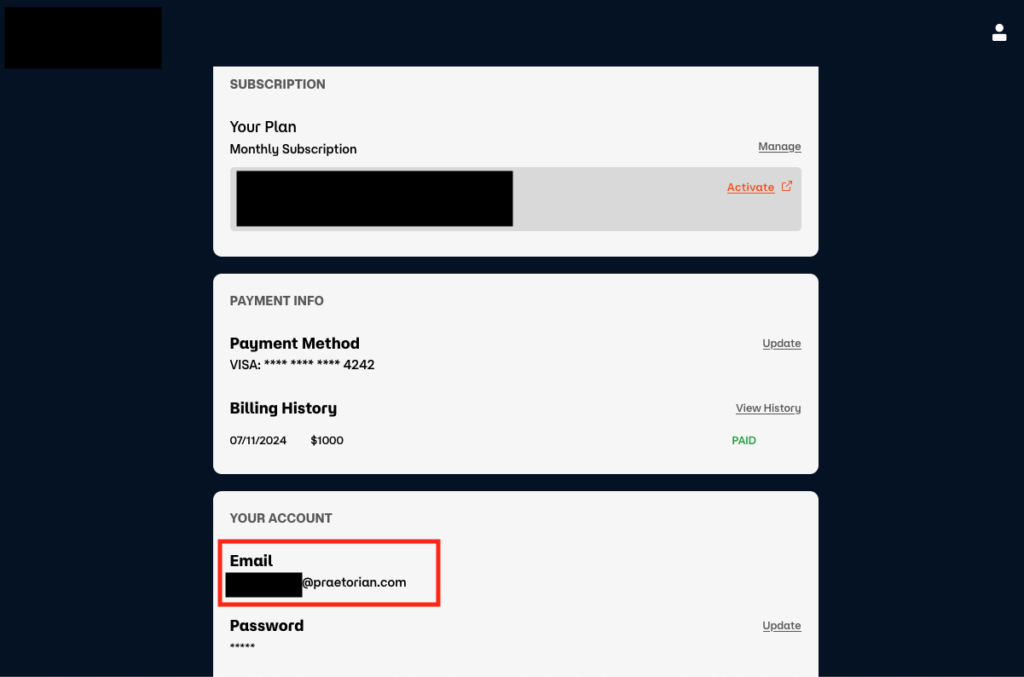
Figure 4: Successfully took over the victim account
Recommendations
Praetorian recommends the following actions to mitigate these vulnerabilities:
- Server Side token generation: The developers should ensure that the login challenge should be generated on the server-side and must be tightly coupled to the user’s email address.
- Email verification: The developers should implement backend logic to send the email containing the login link only to the registered email address. This will eliminate the scope of email redirection.
Conclusion
The account takeover vulnerability in the streaming application reminds us of the importance of secure authentication mechanisms. Throughout the blog, we explored how the weak login workflow allowed us to exploit the broken authentication, gaining access to unauthorized accounts.
The impact of vulnerabilities such as these on a business can be profound. Attackers’ ability to take over accounts can result in substantial financial losses, as unauthorized access to premium content devalues the service, reduces revenue, and undermines the business model. Moreover, the vulnerability exposes users’ private, sensitive information, including personal information and payment data.
By addressing these issues and implementing robust authentication protocols, developers can significantly reduce the prevalence of vulnerabilities arising through broken authentication. As highlighted by its presence in OWASP’s Top 10, insecure authentication is a pervasive threat that demands vigilant attention and proactive measures to ensure the safety of users in the digital realm.