We are pleased to release Nosey Parker Explorer under the Apache 2.0 license.
Nosey Parker Explorer is an interactive review tool for findings from Nosey Parker, the secrets detector we’ve been developing and using in offensive security engagements since 2022. It allows us to quickly triage thousands of findings, identifying ones of possible material business impact. It’s been instrumental in reaching objectives on Red Team engagements against multiple Fortune 100 companies.
The Problem
Nosey Parker itself performs well, making scanning terabyte-scale inputs on a laptop feasible. Through our experience, we’ve found that when scanning at such a large scale, even a tool that gives only a few false positives produces a huge volume of findings to review.
Although it is possible to sift through this as a static report (like from `noseyparker report`), this becomes unwieldy when dealing with more than a few dozen findings. Interactive filtering and the ability to focus on particular types of findings provide an enormous lift for operators; that’s what Nosey Parker Explorer provides.
Features
Nosey Parker Explorer is a terminal user interface (TUI) application built using the excellent Textual framework for Python. It needs no backend server deployment, and can even run with full functionality across SSH sessions to systems that don’t have any window manager available. It works natively with a datastore produced by scanning for secrets with Nosey Parker.
Three main panes
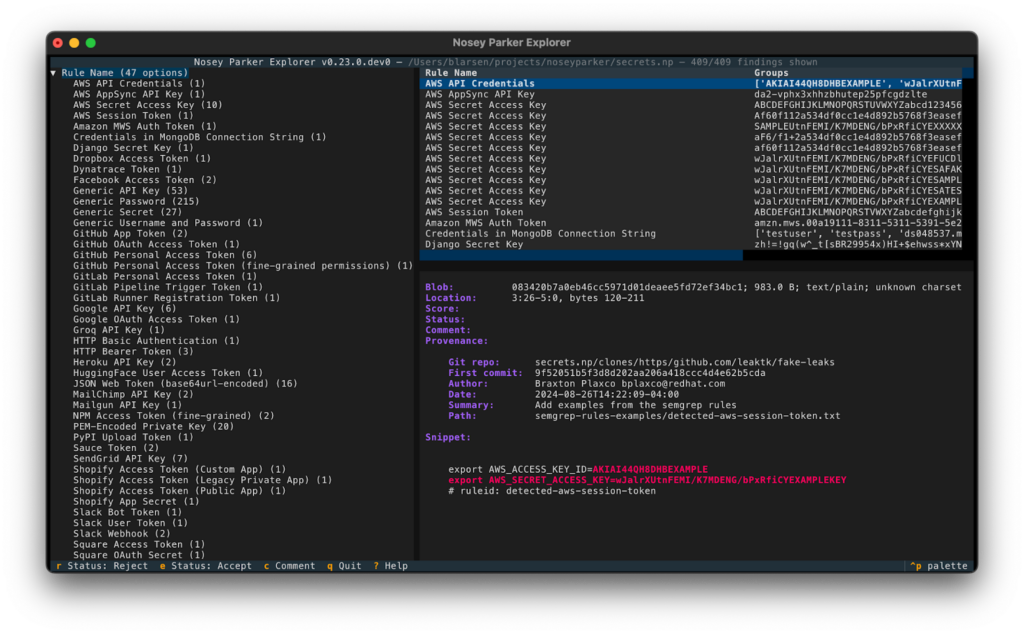
Its main screen has three panes: a filters pane on the left, a findings pane on top, and a findings details pane on the bottom. When focusing on a particular finding, up to 10 occurrences of it are shown in the details window.
Faceted search to rapidly focus on particular types of findings
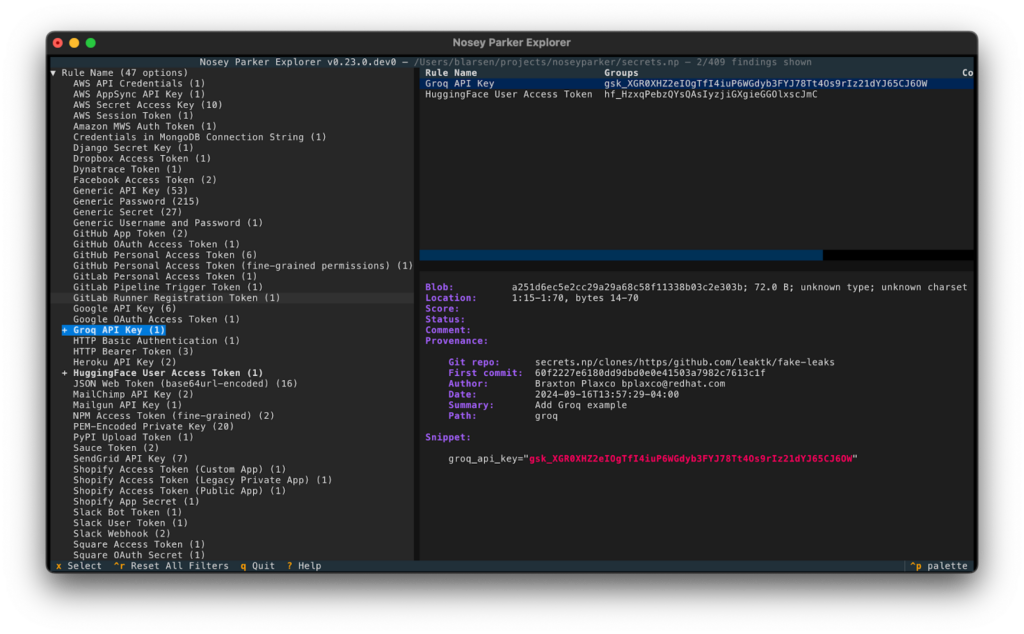
The filters pane provides a faceted search of the results, similar to what’s provided in online shopping sites. You can use this to focus on, for example, `Hugging Face User Access Token` and `OpenAI API Key` findings that appear in JSON or Markdown files. Its visibility can be toggled by pressing `F7`.
Full source file view
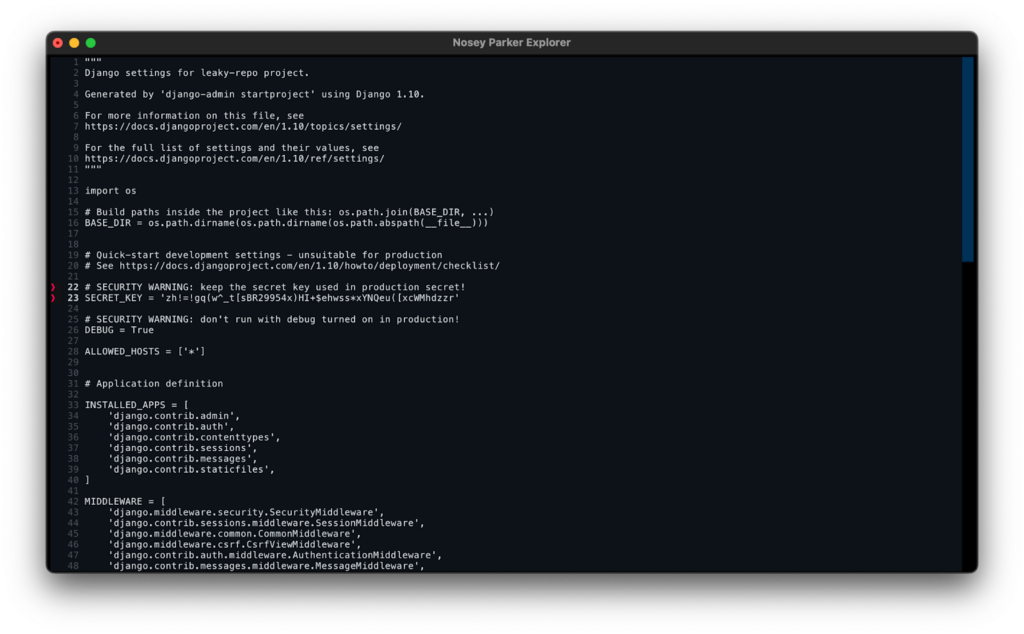
The full source for a match can be viewed by pressing `o` when a match is selected in the details pane. This is helpful when additional context beyond the match snippet is required to make a triage decision.
Status annotation and commenting

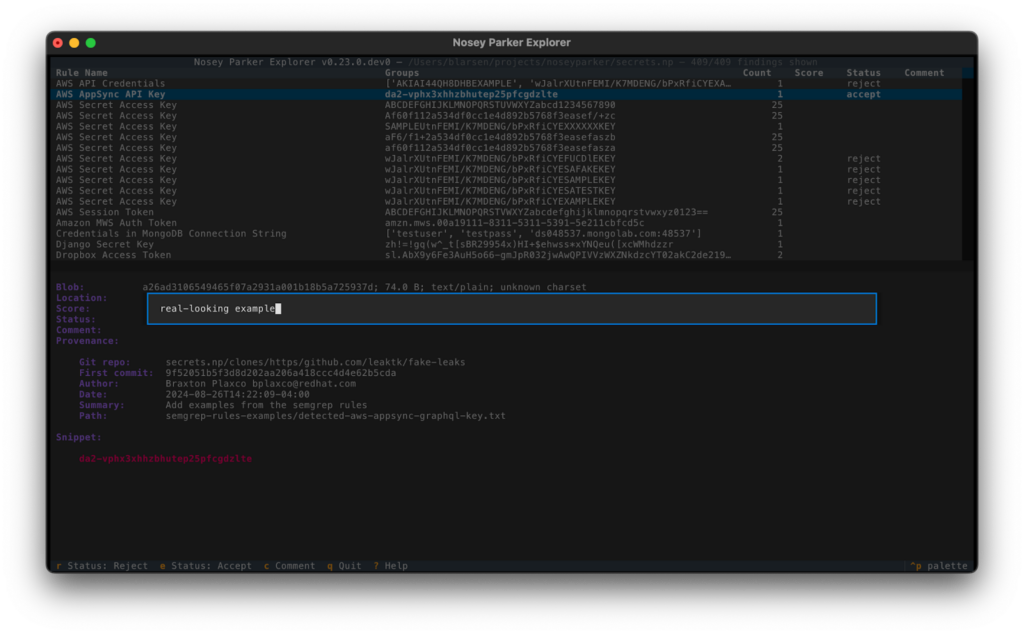
In the findings pane, you can assign a status to a finding (either `accept` or `reject`). You can also assign freeform comments. Any status or comment you assign will be saved to the Nosey Parker datastore that is opened.
Nosey Parker’s own `report` command understands these annotations; it can produce a static report of findings with a particular status using its `–finding-status={accept,reject,mixed,null}` option. This means you can assign status labels with Nosey Parker Explorer and then produce a static report of just the findings you’ve accepted.
Integrated help

Integrated help can be accessed by pressing `?`.
Scalability
Like Nosey Parker itself, Nosey Parker Explorer is designed for scalability. It is regularly used at Praetorian with datastores containing hundreds of thousands of findings and millions of matches.
Next steps
Nosey Parker Explorer is available on GitHub under the Apache 2.0 license:
https://github.com/praetorian-inc/noseyparkerexplorer
We’ve used it in hundreds of offensive security engagements at Praetorian, and so it is relatively mature software. However, it was originally implemented as a quick prototype, which turned out to be far too useful. If you run into bugs or have UX suggestions, please open an issue or start a discussion!
