Technical Advisory: Vulnerabilities Identified within ListServ

Overview In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities that are likely to impact the security of leading organizations. Our ultimate goal when performing our research is to identify unauthenticated remote code execution vulnerabilities which could be reliably exploited across a wide variety of […]
Long Live the Pwn Request: Hacking Microsoft GitHub Repositories and More
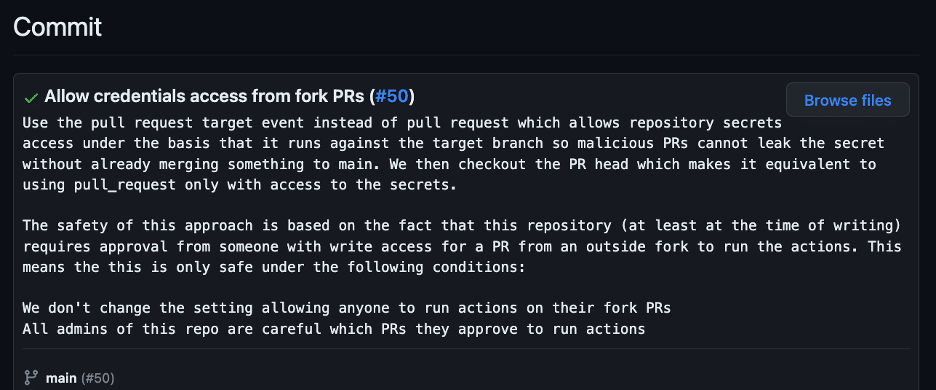
Software supply chain attacks have been increasing both in frequency and severity in recent months. In response to these attacks, the CISA has even released a cybersecurity information sheet (CSI) on how organizations can secure their CI/CD pipelines. The introduction to the CSI states: “(The) CSI explains how to integrate security best practices into typical […]
DoubleQlik: Bypassing the Fix for CVE-2023-41265 to Achieve Unauthenticated Remote Code Execution
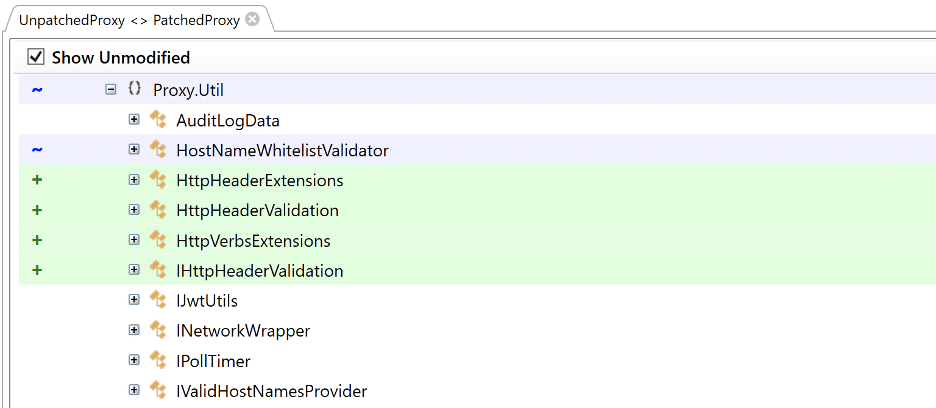
Overview On August 29th, 2023, Qlik issued a patch for two vulnerabilities we identified in Qlik Sense Enterprise, CVE-2023-41265 and CVE-2023-41266. These vulnerabilities allowed for unauthenticated remote code execution via path traversal and HTTP request tunneling. As part of our standard operating procedure, we performed a diff of the issued patch to identify potential bypasses […]
Helpdesk Telephone Attack: How to Close Process and Technology Gaps
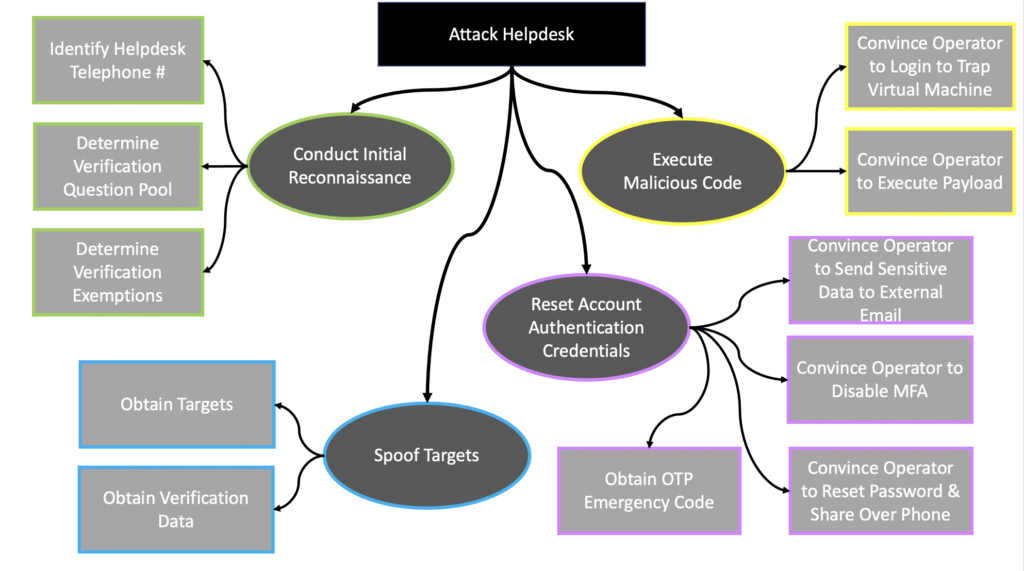
Introduction As we have witnessed in recent weeks with the MGM and Caesars Entertainment breaches, helpdesks are prime attack surfaces that are seeing a surge in exploitation. Although much of the press surrounding these most recent events alludes to helpdesk operators’ roles in the exploits, this type of vulnerability actually is a technology and process […]
Advisory: Qlik Original Fix for CVE 2023-41265 Vulnerable to RCE
Overview On August 29th, 2023 Qlik issued a patch for two vulnerabilities we identified in Qlik Sense Enterprise, CVE-2023-41265 and CVE-2023-41266. These vulnerabilities allowed for unauthenticated remote code execution via path traversal and HTTP request tunneling. As part of our standard operating procedure, we performed a diff of the issued patch to identify potential bypasses […]
Back to the 90s: Fujitsu “IP series” Real-time Video Transmission Gear Hard Coded Credentials
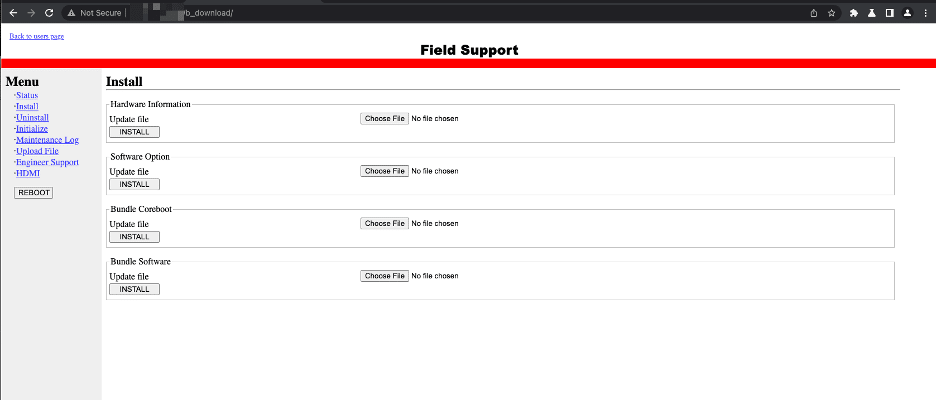
Overview In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities that are likely to impact the security of leading organizations. Exposed embedded devices are a particular area of concern because they typically do not have host-based security controls such as EDR or Antivirus, but still […]
ZeroQlik: Achieving Unauthenticated Remote Code Execution via HTTP Request Tunneling and Path Traversal
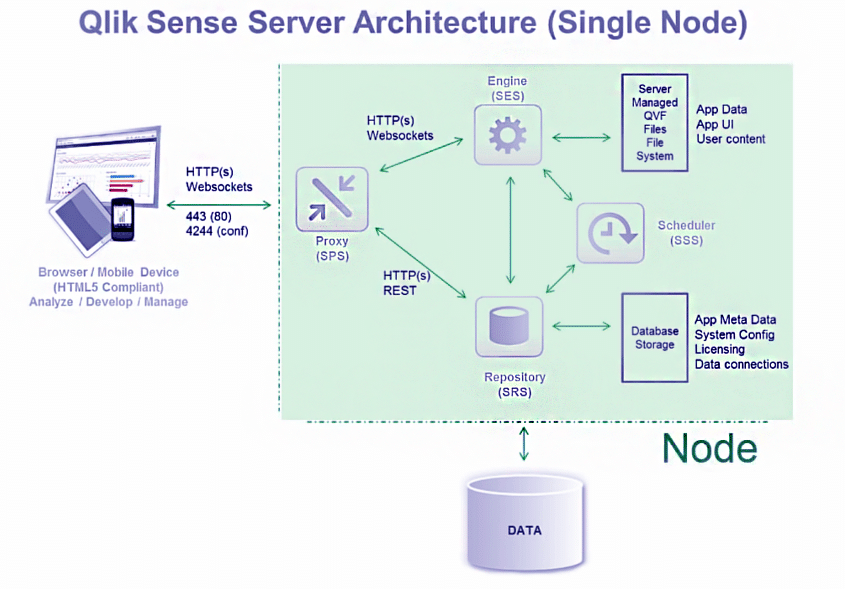
Overview In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities that are likely to impact the security of leading organizations. Recently, we decided to take a look at Qlik Sense Enterprise, a data analytics solution similar to Tableau. The recent exploitation of vulnerabilities in the […]
Advisory: Qlik Sense Enterprise for Windows Remote Code Execution Vulnerabilities
Advisory: Qlik Sense Enterprise Remote Code Execution In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities in applications that are likely to impact the security of leading organizations. Recently, we discovered two vulnerabilities which can be chained together to achieve unauthenticated remote code execution on […]
Announcing Nosey Parker Update to v0.14.0

Last week we published a new release of Nosey Parker, our fast and low-noise secrets detector. The v0.14.0 release adds significant features that make it easier for a human to review findings, and a number of smaller features and changes that improve signal-to-noise. The full release notes are available here. Release highlights File names and […]
Konstellation: A Tool for RBACpacking in Kubernetes
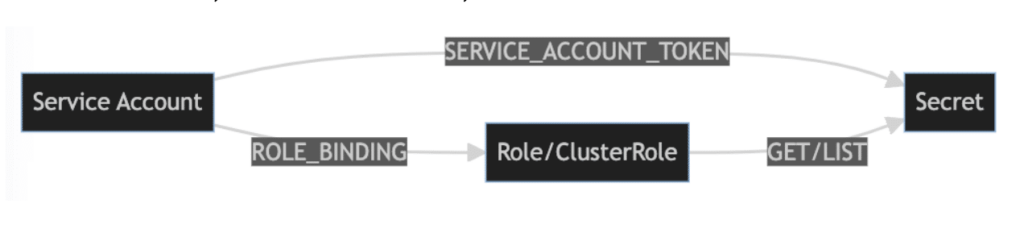
The author presented this paper and corresponding tool at Black Hat: Arsenal 2023 on August 10, 2023. For a more general overview of Konstellation and its capabilities vis a vis Kubernetes RBAC, please see our earlier companion post. Kubernetes Role-Based Access Control (RBAC) is a mechanism for controlling access to resources in a Kubernetes cluster. […]