Introducing Konstellation, for Kubernetes RBAC Analysis
Praetorian is excited to announce the upcoming release of Konstellation, a new open-source tool that simplifies Kubernetes role-based access control (RBAC) data collection and security analysis. Join us August 10, 2023, at Black Hat Arsenal 2023 for a deeper dive on exactly what this tool can do for you. Kubernetes RBAC is a powerful tool […]
The Power of Chariot Managed Service
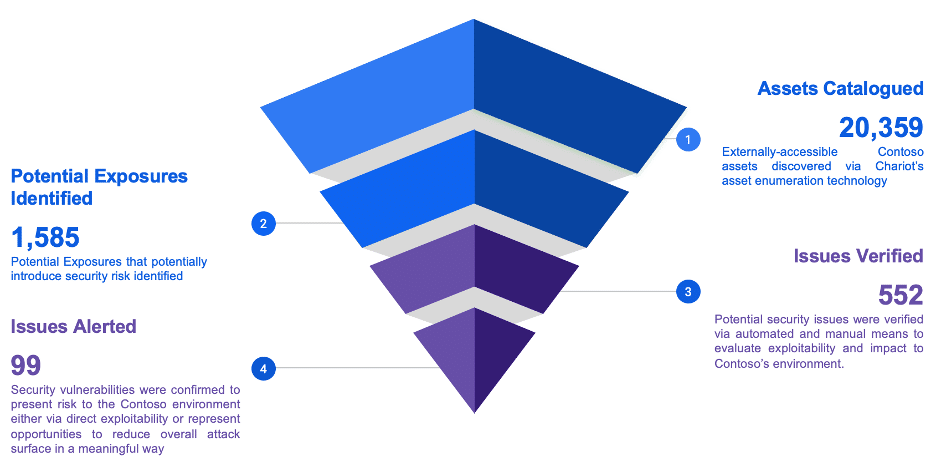
The landscape of cybersecurity is one of constant, rapid change, challenging organizations to keep pace with emerging threats. Organizations search for a tool or product that holistically enhances their cybersecurity program and gives them peace of mind – a silver bullet. Unfortunately, no single vendor offers silver bullets. With budgets tightening, cybersecurity leaders may face […]
Announcing Gato Version 1.5!

On January 21, 2023 at ShmooCon 2023, Praetorian open-sourced Gato (Github Attack Toolkit), a first of its kind tool that focuses on abusing offensive TTPs targeting self-hosted GitHub Actions Runners. Since then, Praetorian and other offensive security practitioners across the information security community have leveraged Gato for so much more than just self-hosted runner attacks. […]
fwd:cloudsec 2023: Top Four Themes in Cloud Security for 2023

At Praetorian, we pride ourselves on our extensive expertise in cloud security and our commitment to staying at the forefront of the ever-evolving landscape. We consequently were excited to attend the highly anticipated fwd:cloudsec 2023 conference held on June 12–13, in Anaheim, CA. This non-profit conference brings together cloud security professionals, researchers, and practitioners from […]
Improving Performance and Scalability: Updates and Lessons from Inspector, Our End-to-End Testing Solution
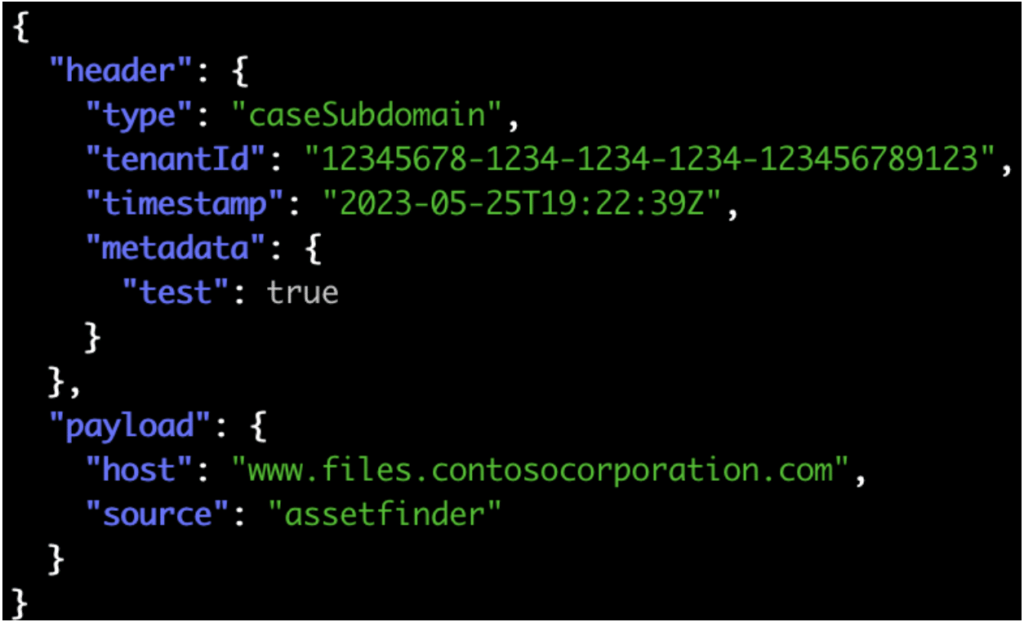
Overview In a previous article titled Inspector or: How I Learned to Stop Worrying and Love Testing in Prod, we discussed our end-to-end testing solution, Inspector, which we leverage to perform continuous testing of our external attack surface enumeration scanning system. Here, we discuss some of the recent modifications and updates we made to Inspector […]
MOVEit! An Overview of CVE-2023-34362
On May 31st, 2023, Progress disclosed a serious vulnerability in its MOVEit Transfer software. The vulnerability is remotely exploitable, does not require authentication, and impacts versions of the software that are 2023.0.1 (15.0.1) or earlier. We are aware of multiple reports of active exploitation of this vulnerability in the wild, and attackers are already mobilizing […]
Content Discovery: Understanding Your Web Attack Surface
Attack Surface Management (ASM) tools find quite a lot of vulnerabilities on the Web. This really isn’t surprising, given that HTTP/S is by far the most common and broadest of all the services comprising the Internet. In fact, Web-based issues represent the majority of the findings about which our Managed Service Providers (MSPs) inform our […]
In Brief: Chariot Alignment with FDA Section 524B.1

Chariot is more than a product; it’s a partnership that combines automated monitoring and human analysis to identify externally-accessible security risks. In light of the FDA’s latest requirements for in-market device security (summarized in Section 524B), Praetorian’s customers are having success leveraging the Chariot Managed Service as a cost-effective and scalable approach to satisfying Section […]
Measuring People, Process, and Technology Effectiveness with NIST CSF 2.0
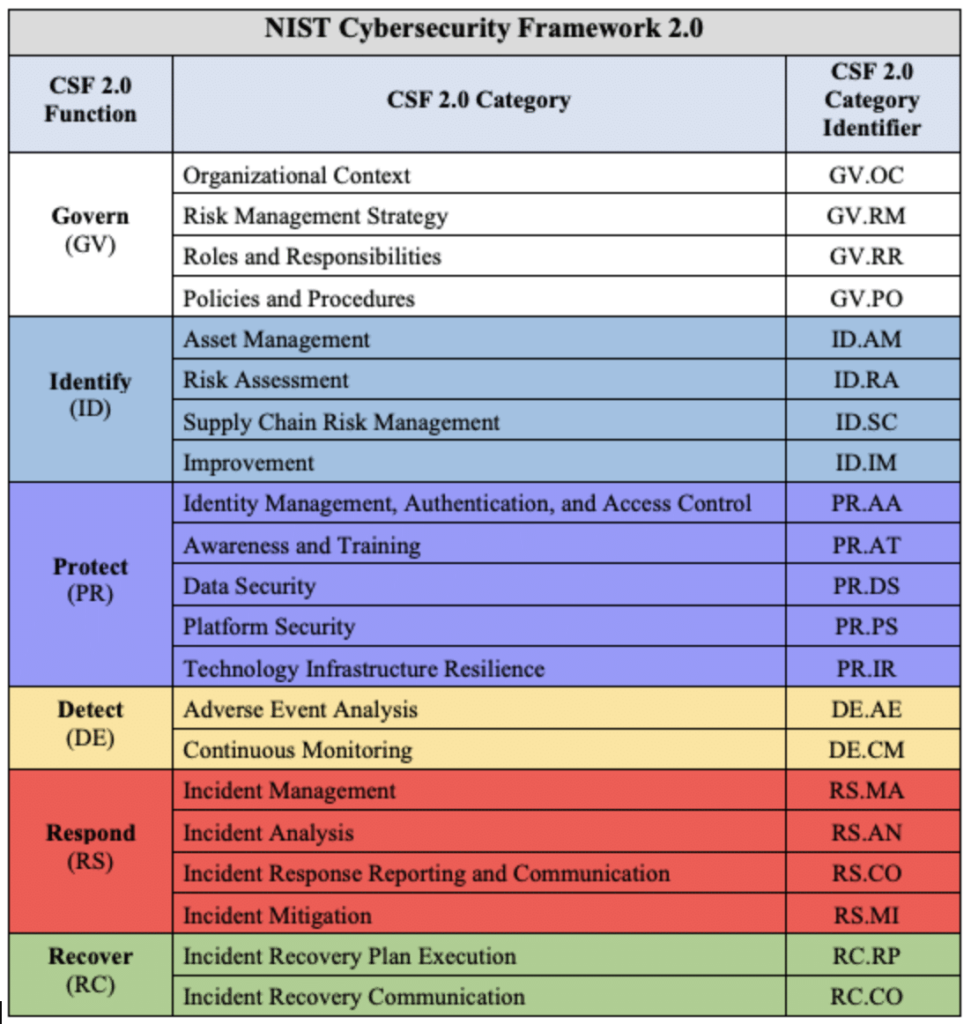
The National Institute of Standards and Technology (NIST) recently released the latest draft of the Cybersecurity Framework (CSF) 2.0, incorporating numerous updates and improvements over its predecessor. Among these changes, the addition of the Governance function has generated significant buzz within the cybersecurity community. We also are particularly excited about the modification of subcategories in […]
Cyber Cartography: Mapping a Target
As Phil Venables has said, “at some level, cyber defense is a battle over whether the attacker or defender has better visibility of the target. Action is key, yes, but without good ‘cyber cartography’ it can be hard to act in the right way.” An attacker’s first step is enumeration, or identifying what looks hackable. […]