Gladius: Automatic Responder Cracking
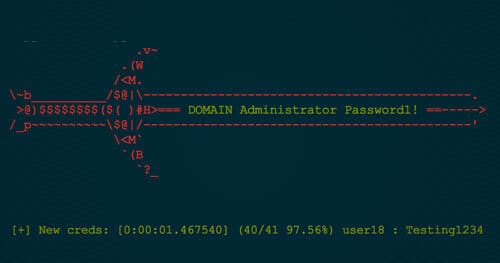
So there you are, performing your internal penetration test, using Responder to potentially grab hashed credentials and thinking "Responder is awesome… but manually cracking credentials isn’t fun." Well, welcome Gladius! Gladius happily listens for Responder hashes (and.. spoiler alert.. secretsdump.py and hashdump) and automatically passes them to hash cat. At its core, Gladius listens in target directories for file events and then performs computations based on the event. Let’s walk through the Responder workflow with Gladius.
Introducing MitM-VM & Trudy: A Dead Simple TCP Intercepting Proxy Tool Set
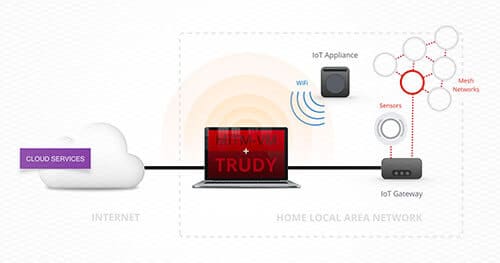
Positioning yourself as a man-in-the-middle (MitM) is a powerful situation to leverage during a security assessment. Unfortunately, in some situations, leveraging an active MitM position is difficult. There are existing proxies that try to alleviate these issues but they all seem to suffer from a flaw that makes using the tool undesirable. MitM-VM and Trudy are a complimentary set of tools that are designed to address several issues with existing proxies. Together they enable easy-to-setup and powerful man-in-the-middle positions. Why build these tools? Modifying custom binary protocols on the fly while sitting between an embedded device and a server is usually a slow process that involves sniffing legitimate traffic and then rebuilding packets programmatically. Trudy makes this process easy by enabling Burp-like features for generalized TCP traffic.
IPv6 Has Arrived — Is Your Security Infrastructure Prepared?
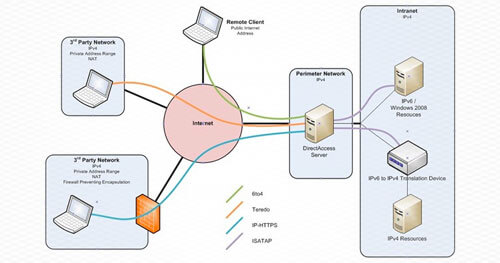
Just over 20 years ago, RFC 1883 – ‘Internet Protocol, Version 6 (IPv6) Specification’ – was published. Since then, exhaustion of the IPv4 address space, and a subsequent migration to IPv6 connectivity has been predicted, heralded, and warned against repeatedly. The seemingly endless stream of warnings and proddings over the past decade to “migrate or else…” have proved unfounded for most organizations. Understandably, this causes many organizations to dismiss or ignore recurring questions about IPv6 adoption, migration, and management plans.
The Reason My Lamp is Insecure

I suffer the struggle many others do. It’s a systemic issue that’s not really talked about much. The issue I’m talking about is the inconvenience of turning my lamp off and then proceeding to stumble around in the dark to get to my bed. I set out to solve this problem by automating my lamp with a Raspberry Pi, a relay, and a simple web application. Those who have worked with electronics before know this setup is not very technically challenging, but I wasn’t going for anything too fancy. My goal was to create a simple web application that could turn my lights on and off, which can be seen in the code below. This code also includes an alarm clock which operates by flashing my lights every morning at a preset time.
Getting Started with Damn Vulnerable Router Firmware (DVRF) v0.1
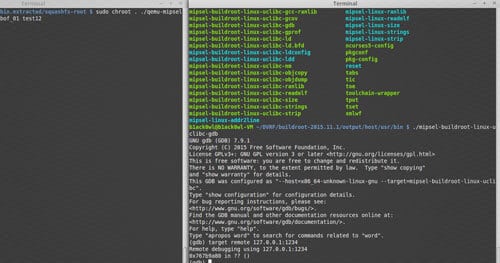
The goal of the DVRF project is to simulate a real-world environment to help people learn about other CPU architectures outside of the x86_64 space. The project will also help people get into discovering new things about hardware. As of now this DVRF firmware is tailored for the Linksys E1550 Device. If you do not have one don’t worry! Ready to get a jump start on learning aspects of embedded device hacking for exploit development? If so, this project is for you.
Javascript Sensor API and New Browser Features Raise Privacy Concerns
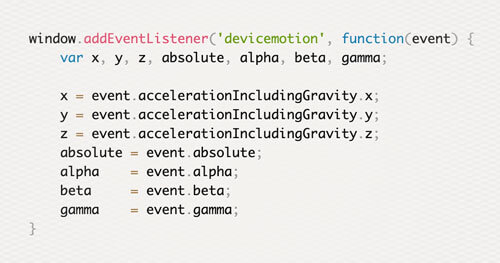
The W3 specs get updated and expand faster than most people can keep up with them. In 2015, many browsers began adding support for mobile sensors which do not prompt users for permission to access them. The new Javascript sensor API and browser features should start raising privacy concerns. These new features allow web applications to be more powerful and ultimately replace the role of many mobile apps. As both a developer and user, it’s important to stay aware of new features and to be mindful of what a website is capable of doing to your mobile device.
Engineer Spotlight: Cory Duplantis and the 2015 SANS Holiday Hack Write-up

As an engineer, solving puzzles is part of everyday life. Any new challenge, whether it be learning a new exploitation technique or seeing a new embedded architecture for the first time, is simply another puzzle that I can learn how to solve in time. It is that mindset of always being curious and wanting to explore and apply new concepts that is utilized everyday at Praetorian. This mindset is also my default when approaching capture the flag (CTF) puzzles such as the CounterHack HolidayHack from this past year. As an internal penetration tester at Praetorian, I don’t usually dabble in the web spaces frequently, so the web challenges from the HolidayHack were a great opportunity to brush off the old web knowledge and maybe add a new web technique to the ever growing bag o’ tricks.
Group Policy Preferences (GPP) Pwned
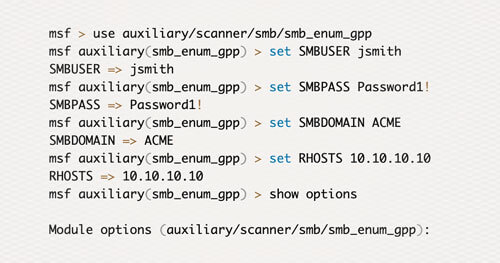
Over the past few months I’ve had a chance to clean up some code that we’ve used internally for penetration testing for some time now. This code was built to demonstrate the weaknesses of using Group Policy Preferences (GPP) to store and distribute local or domain credentials. We have found that many organizations store local admin, domain service, and even Domain Admin account credentials using GPP. The module that I submitted to the Metasploit Github repo provides the ability to enumerate GPP credentials as a domain user with access to the SMB share on the DC. Extracted credentials will be stored in the Metasploit creds tables.
Microsoft’s Local Administrator Password Solution (LAPS)
Hackers, incident responders, and penetration testers alike know that valid credential reuse is one of the most common real-world vulnerabilities in today’s networks. Valid credential reuse dominates as the top vulnerability in Verizon’s 2014/2015 Data Breach Investigations Reports Microsoft networks remain amongst the most vulnerable and exploited due to the way in which Active Directory is typically deployed: A base image is created with a standard local administrator password, which is duplicated on all workstations in the environment. When an attacker compromises any workstation, the local administrator password hash can be obtained and used to access every other workstation using the classic Active Directory exploit Pass-the-Hash (PtH). This methodology is described in detail in FireEye/Mandiant M-Trends 2015 case studies.
Statistics Will Crack Your Password
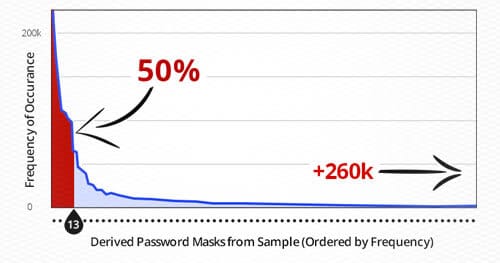
When hackers or penetration testers compromise a system and want access to clear text passwords from a database dump, they must first crack the password hashes that are stored. Many attackers approach this concept headfirst: They try any arbitrary password attack they feel like trying with little reasoning. This discussion will demonstrate some effective methodologies for password cracking and how statistical analysis of passwords can be used in conjunction with tools to create a time boxed approach to efficient and successful cracking.