Navigating Today’s Shared Security Responsibility Model in the Cloud
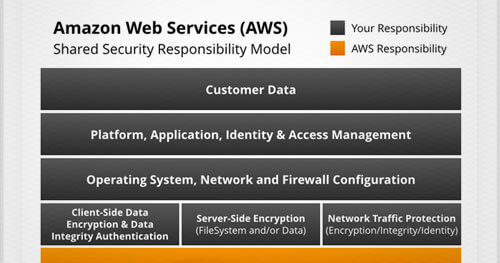
How do you protect the confidentiality, integrity, and availability of systems and data in your organization’s growing cloud environments? It starts by understanding your responsibility.
Addressing security in a public cloud environment is slightly different than in your on-premises data centers. When you move systems and data to the cloud, security responsibilities become shared between your organization and the cloud service provider. Infrastructure as a Service (IaaS) providers, such as Amazon Web Services (AWS), are responsible for securing the underlying infrastructure that supports the cloud, and you are responsible for anything you put on the cloud or connect to the cloud.
NIST Cybersecurity Framework vs. NIST Special Publication 800-53
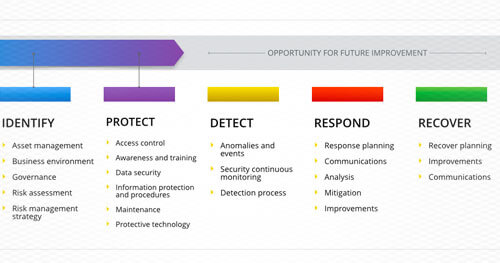
With the recent high-profile attacks on Sony and Anthem, it’s clear that cyber risks continue to grow and that organizations need to do more to strengthen their cybersecurity defenses. Security frameworks exist to guide the implementation and management of security controls, and they should be used by any organization looking to intelligently manage cyber risk. A security framework helps prevent a haphazard approach to information security, and reduces potential gaps in the organization’s security efforts. The ideal framework provides a complete guide to current information security best practices while leaving room for an organization to customize its implementation of controls to its unique needs and risk profile. Several existing and well-known cybersecurity frameworks include COBIT 5, ISO 27000, and NIST 800-53. Recently, a new framework has come into play: NIST’s “Framework for Improving Critical Infrastructure Cybersecurity.”
Cloud Security Best Practices for Amazon Web Services (AWS)

Over the last 18-months we have seen more and more of our clients turn to IaaS (Infrastructure-as-a-Service) providers to support their enterprise infrastructure needs. While there are obvious benefits to utilizing these types of services, such as reducing the complexity associated with managing an enterprise infrastructure, moving to the cloud can also introduce new security concerns. Most often these concerns arise as a result of misconfigured cloud instances.
CRITICAL: Bash “Shellshock” Vulnerability
On September 24, 2014, a vulnerability in Bash—now referred to as the ‘Shellshock’ bug—was publicly announced after its discovery last week by Stephane Chazelas. Security experts expect the Shellshock bug to have significant and widespread impact, potentially more devastating than Heartbleed.
Building the HashCat API in Ruby to Crack Passwords in the Cloud
Have you ever had an amazing idea for automating two or more pieces of technology and then realized one of them doesn’t have an API? I came across this problem more than once during the development of a couple of projects here at Praetorian. In this post, I’ll share some of the libraries and techniques I have used to build out APIs for CLI programs, such as HashCat and nmap. Hopefully, these techniques and libraries will be helpful to you when building out new web applications and frameworks.
Why You Should Add Joern to Your Source Code Audit Toolkit
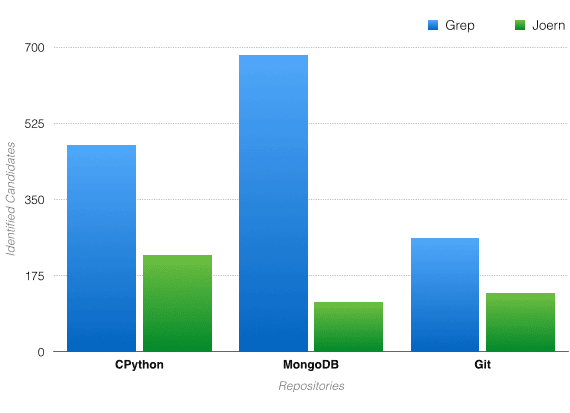
Joern is a static analysis tool for C / C++ code. It builds a graph that models syntax. The graphs are built out using Joern’s fuzzy parser. The fuzzy parser allows for Joern to parse code that is not necessarily in a working state (i.e., does not have to compile). Joern builds this graph with multiple useful properties that allow users to define meaningful traversals. These traversals can be used to identify potentially vulnerable code with a low false-positive rate.
Using Developer Debugging Tools to Pentest Mobile Applications
During a recent assessment, I was pentesting a hybrid mobile application that is a companion to a web application. The applications allow users to collaborate while creating new interactive digital content. Through the web interface, content creators are allowed to upload a wide range of files, including HTML files, and share the content with other individuals in their organization. Thus, any user with proper permissions is able to view and edit shared content.
Man-in-the-Middle TLS Protocol Downgrade Attack
A flaw was recently found in OpenSSL that allowed for an attacker to negotiate a lower version of TLS between the client and server (CVE-2014-3511). While this vulnerability was quickly patched, an attacker that has control of your traffic can still simulate this attack today. Let’s explore how this is possible through looking at man-in-the-middle attacks and how browsers handle SSL/TLS connections. In addition, we will see the implications of the attack on cryptographic security.
PHP-CGI Remote Command Execution Vulnerability Exploitation

During a recent penetration test, our team found a few web servers that were vulnerable to a PHP-CGI query string parameter vulnerability (CVE-2012-1823). This vulnerability allows an attacker to execute commands without authentication, under the privileges of the web server. The target environment had very strong egress controls in place. All outbound ports were blocked and only ports 80 and 443 were allowed inbound. This made it difficult to obtain an interactive shell. Therefore, we decided to build a proof of concept exploit script using cURL to execute commands and then take it to the next level by authoring a new Metasploit Module.
MAC Cryptographic Errors and Vulnerabilities in SSO Authentication
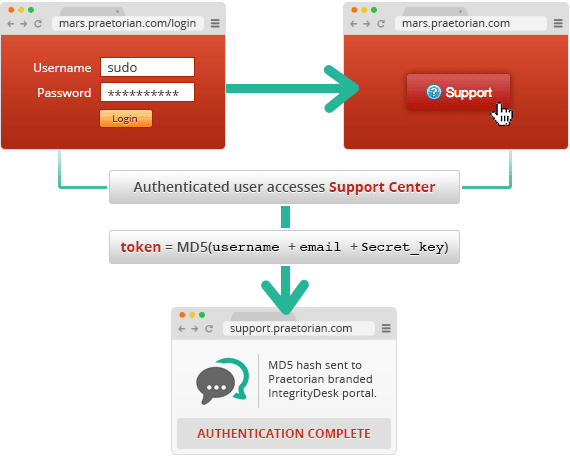
In-house crypto is often a goldmine of cryptographic errors and vulnerabilities. In this post, I’ll describe one of the glaring errors discovered in an online customer support and help desk solution we were considering for use in Praetorian’s cloud-based password cracking service, Project Mars. Hopefully, this can serve as a warning to anyone thinking about writing his or her own crypto libraries.