NECCDC Red Team: Quick DNS Command and Control (C2) Trojan

Recently, I had the opportunity to participate in the Northeast Cyber Collegiate Defense Competition (NECCDC) at the University of Maine. The competition was made up of 10 student groups (blue teams) from various colleges in the region that were tasked with protecting a mock network against a group of professional pentesters (the red team) who were trying to break in. This was my third year on the red team. Prior to the competition, I built several tools that would make life easier for the red team and enable us to differentiate between the qualities of the blue teams we were attacking. I am planning to release the code that I built for the competition over the next few months in a series of blog posts.
Advanced Threats: Driving Senior Leadership Awareness
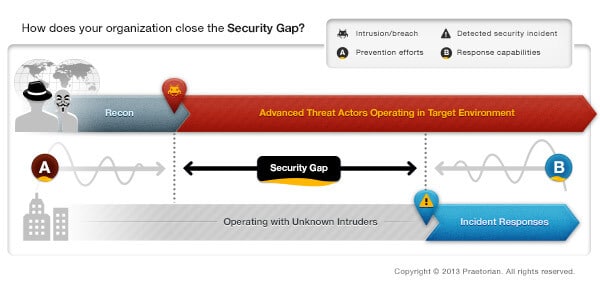
In today’s changing security environment, where advanced persistent threats (APT) are playing such a dramatic and notable role, it is the security organization’s responsibility to ensure that senior leadership understands and accepts risk associated with modern-day advanced threat actors. Regardless of your security maturity levels, you should at least be having the conversation about Advanced Threats. It is incumbent upon security leaders to drive this conversation within your organization in an effort to shift expectations away from thinking…
Introducing the New ROTA Tech Challenge
Hello everyone! I first want to introduce myself, my name is Anthony Marquez and I am the newest member of Praetorian’s technical team. I’m excited to join a group of such bright individuals and work with a company that values the promotion of thought leadership and realizes the importance of allowing their employees to take on interesting side projects. I hope to be contributing to several blog posts in the future. For my first post I wanted to talk about one of the first side projects that I recently completed here at Praetorian —ROTA.
Metasploit Integration for Password Auditor
Last week I introduced our new Password Auditor, an internal project I’m working on here at Praetorian. Today, I’m back with a followup screencast that demonstrates one of its major features — Metasploit integration! If you missed the previous screencast, I recommend watching it to get a sense of the tool’s basic functionality.
Password Auditing with Style
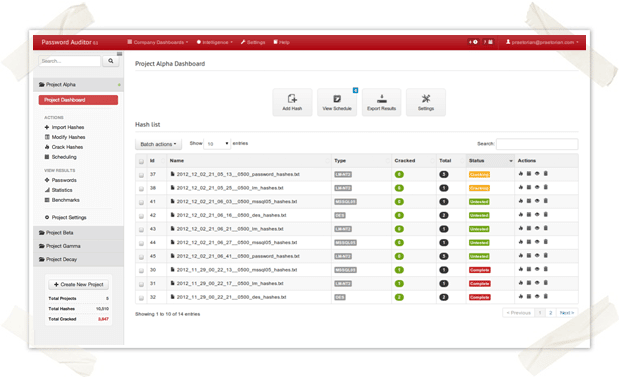
In my last post, I announced that our team has been developing an easy-to-use password cracking tool with advanced features. Our initial goal for the project was to create something that made password auditing easier for our services team. However, after several internal discussions we’ve decided to share our work with the security community in order to see if this tool has value beyond what we had initially envisioned. We’ve even talked about opening up a private, invite-only Beta to let others get some hands-on time with the tool. I encourage you to learn more about the tool and leave feedback/comments below (it may increase your chances of receiving an early invitation).
Easy to Use Password Cracking Tool with Advanced Features
Looking back over this past year, I have noticed a continuing theme among public security breaches. Similar to 2011, this year’s high profile security breaches often end in a public dump of confidential victim data. It is not uncommon for Hacktivist groups, such as Anonymous, to publically dump password hashes and other confidential data as a way of proving the breach occurred and as a way of embarrassing the victim.
Burp SQLmap plugin for Windows
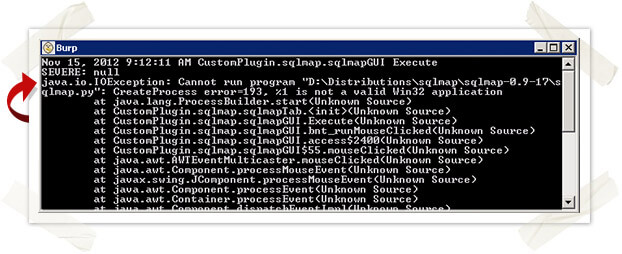
Burp Suite provides a very basic SDK known as Burp Extender. Burp Extender allows third parties to extend the features of an already powerful web application testing suite. In March of this year, Daniel Garcia (cr0hn) created a SQLmap plugin for Burp using the Burp Extender SDK. With Daniel’s SQLmap plugin, automated SQL injection discovery and exploitation is now seamless between two of our favorite web application pentesting tools.
Twitter’s Charlie Miller is Coming to Austin ISSA to Discuss iOS Security
Praetorian is excited to be a platinum sponsor for the upcoming ISSA Chapter Meeting on Wednesday, November 7 from 11:00am to 3:00pm at St. Edwards Professional Education Center. The event will feature the famous/infamous security researcher Charlie Miller.
Praetorian sponsors 2012 Boston Application Security Conference (BASC)

Praetorian is excited to sponsor and attend the upcoming 2012 Boston Application Security Conference (BASC). The Boston Application Security Conference (BASC) will be held Saturday, Oct. 13, from 10 a.m. – 6:30 p.m. at Microsoft’s New England Research & Development Center at One Memorial Drive, Cambridge. Admission to the BASC is free but registration is required for breakfast, lunch, and the evening social time.
The Honeynet Project Maps Real-Time Attacks From Around the World
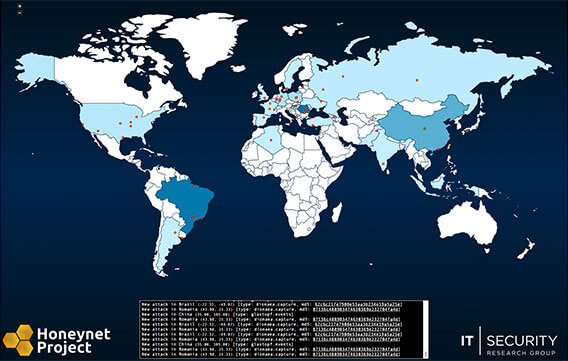
Members of The Honeynet Project’s Giraffe Chapter released a new real-time attack map earlier today. The map shows live attacks from locations around the world, provided by distributed honeypots operated by Honeynet Project chapters. Currently the map is in an alpha release stage, and additional data and input sources are planned for future releases. [Update 9/25/2012: Additional data feeds have been added]