Multi-Core and Distributed Programming in Python
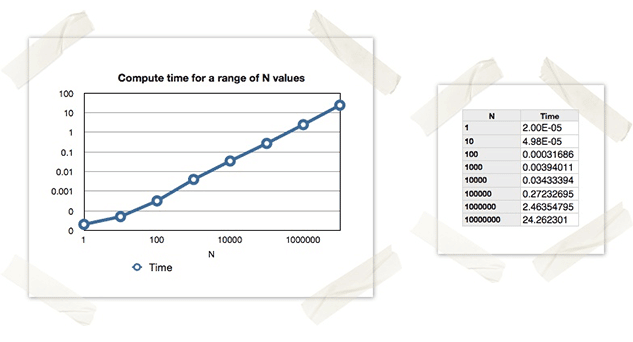
In the age of big data we often find ourselves facing CPU-intensive data processing tasks, therefore it is useful to understand how to harness all available CPU power to tackle a particular problem. Recently we came across a Python script which was CPU-intensive, but when the analyst viewed their overall CPU usage it was only showing ~25% utilization. This was because the script was only running in a single process, and therefore only fully utilizing a single core. For those of us with a few notches on our belts, this should seem fairly obvious, but I think it is a good exercise and teaching example to talk about the different methods of multi-core/multi-node programming in Python. This isn’t meant to be an all-encompassing tutorial on multi-core and distributed programming, but it should provide an overview of the available approaches in Python.
HTTP/HTTPS Bruteforcing Using a List of IPs and Hostnames with Metasploit
Today, I wrote some automation to make it easier to setup and perform HTTP bruteforcing using a list of IPs and hostnames with Metasploit. Metasploit has several auxiliary modules that make it easy to perform various types of bruteforce based attacks. For example, we can easy bruteforce all HTTP BASIC AUTH systems by using the http_login module.
Black Hat USA 2012 (Jabra Edition)

Hey everyone! This week the whole security industry will be in Las Vegas for BlackHat 2012, BSidesLV and Defcon. As I have done for the past few years, I will be teaching Pentesting with Perl at BlackHat. Pentesting with Perl is a course for anyone that has previously coded in nearly any language but wants to learn how to automate some of the common tasks that need to be performed during a pentest. The major change for this year is the course length, which was moved to two days based on feedback from students. The new schedule will make the class much more enjoyable since there will be more time for things like peer-programming, in-depth discussions of materials as well as code walks (by me and the students). People learn best by doing and that is exactly what this class is all about! Again, I’m really looking forward to seeing everyone in Las Vegas this week. I’m always available on Twitter (@Jabra). Feel free to ping me if you would like to meetup. Lastly, if you’re interest in our Puzzles, our next challenge is already underway. Come and find me if you want to try it out firsthand. See you in Vegas! – Jabra
Effectively Measuring Risk Associated with Vulnerabilities in Web Applications
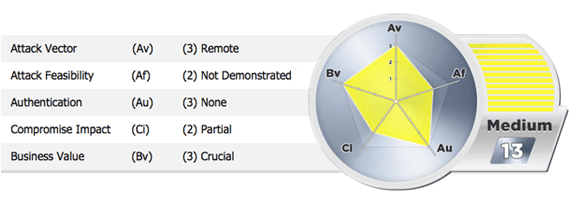
An objective risk rating framework enables our team to compare a standardized measurement of risk across an organization. It also allows our clients to prioritize steps needed in an action plan to mitigate, accept, or transfer organizational risk. Prioritization of vulnerability remediation should be organized objectively based on factors used in the risk rating framework, such as: ease of exploitation, severity of impact if exploited, and level of effort to remedy. If you are considering adopting a risk-rating framework, it is important to tailor a solution that best suits your organizational needs. The following risk rating scale was developed to satisfy the specific needs of our clients, and we hope it provides you with valuable guidance as you plan for the management of risk within your organization…