What is Threat Modeling, and Why it’s Important

What is Threat Modeling, why it’s valuable to organizations, and when it should be used?
10 Cybersecurity Technical Priorities for Telework
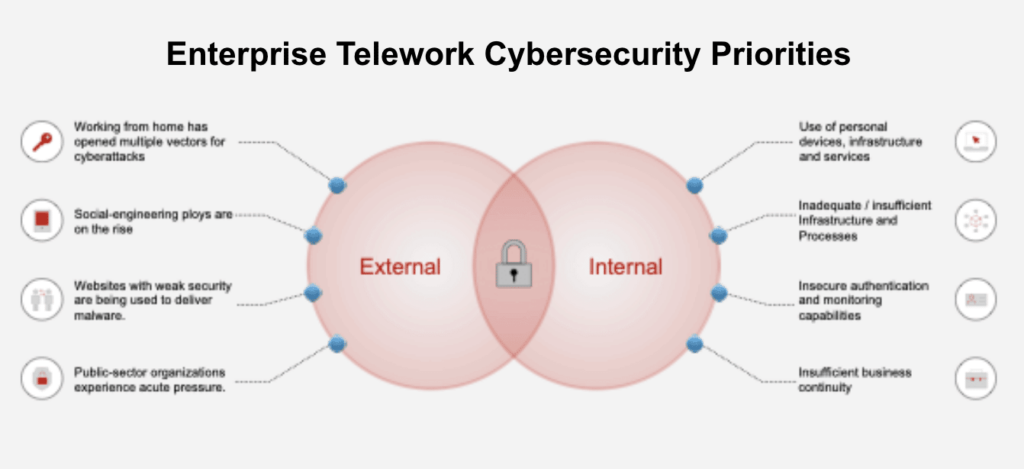
As Telework becomes a new normal, cybersecurity professionals must consider the greater attack surface. This article suggests the top focus areas for consideration.
Evaluating SAST Tools
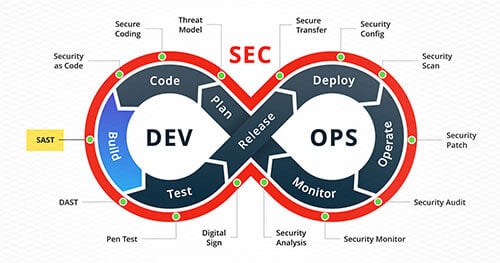
In this article, we aim to provide guidance for organizations that have decided to integrate a SAST tool into their CI/CD pipeline and outline important things to consider before acquiring one.
Extending LLVM for Code Obfuscation (2 of 2)
In part one, we covered setting up a development environment for working with LLVM and developed a simple pass that inserted junk code into binaries during compilation to hinder signature-based detection and manual reverse engineering efforts. In this article, we develop a more complex pass that automatically encrypts string literals during the compilation process by […]
Extending LLVM for Code Obfuscation (1 of 2)
Part one of this article covers the necessary background on LLVM, setting up a development environment, and developing an LLVM pass for junk code insertion in an attempt to generate unique polymorphic binaries.
Lessons from ATT&CKcon 2.0 and SANS Purple Team Summit

In this post, I’ll be going over how I draw value from conferences and the lessons learned, as well as planned projects Praetorian has going into the end of 2019 and start of 2020.
Bypassing Google’s Santa Application Whitelisting on macOS (Part 2 of 2)
This article will examine an example flat PKG installer and demonstrate how to technically abuse Google’s Santa application whitelisting.
Bypassing Google’s Santa Application Whitelisting on macOS (Part 1 of 2)
In this blog post, we’ll describe how we developed social engineering payloads for macOS which can be used to bypass Santa’s application whitelisting.
Implementing Application Whitelisting with Google Santa and Upvote (Part 2 of 2)

In part 2 of this series, we will provide technical guidance on how you can deploy Google Santa and Upvote in your organization.
Implementing Application Whitelisting with Google Santa and Upvote (Part 1 of 2)
In this post, we are going to take a real-life example of implementing application whitelisting inside of Praetorian and the challenges that were overcome.