Safely Conduct Security Assessments of Industrial Control System (ICS) Environments

Our current standard of living is made possible due to the massive scale of critical infrastructure that supports our needs as a society. Electricity, Oil, Gas, Water, and Security are a few of the well-known industries whose infrastructure is managed by Industrial Control Systems (ICS). Few systems have the potential for catastrophic consequences from a security incident as is possible with an ICS breach.
Running a .NET Assembly in Memory with Meterpreter
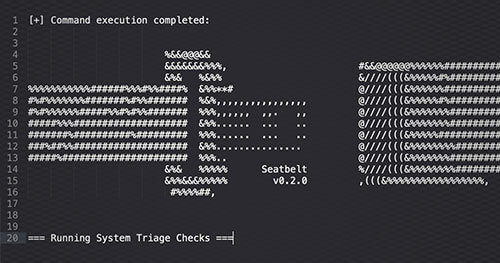
In this blog post I will discuss leveraging Meterpreter’s powershell module to execute .NET assemblies in-memory. Metasploit and Meterpreter are effective and useful tools, but occasionally one encounters a situation where they lack features. Cobalt Strike (a different Command and Control framework) contains an execute-assembly command providing in-memory .NET execution for situations where it lacks built in commands. Meterpreter contains the features required to perform the same behavior, albeit slightly less polished.
Active Directory Visualization for Blue Teams and Threat Hunters
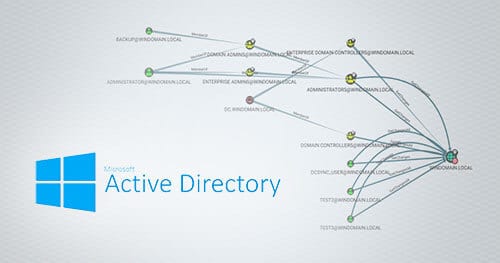
As a network defender, it can be easy to attribute a certain degree of omnipotence to attackers. Advanced threats have an uncanny knack for figuring out how to move through an environment without regards for passwords, roles, permissions, or what “should” be possible.
Benchmarking Enterprise Cybersecurity Programs with NIST CSF
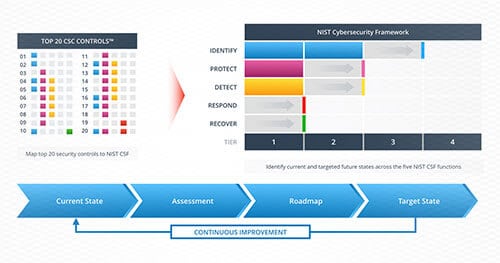
Benchmarking enterprise cybersecurity programs with NIST Cybersecurity Framework (CSF) helps organizations strengthen their security posture.
Signed Binaries Proxy Execution – T1218
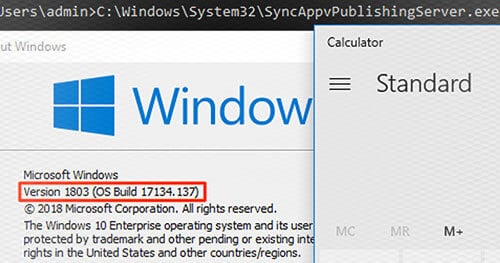
The MITRE ATTACK April release included is a new TTP known as ‘Signed Binaries Proxy Execution’ which is T1218. This TTP is based on an attacker using signed binaries to perform malicious activities.
Signed Scripts Proxy Execution – T1216
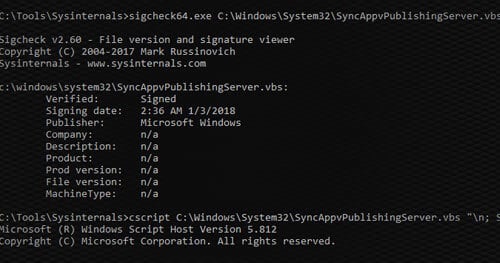
Many organizations trust all signed code from Microsoft. Unfortunately, there are many ways in which attackers can use this trust against them. Previously, we covered using signed binaries to perform malicious activities. In this post, we will be covering how to use signed scripts.
How to use Kerberoasting – T1208 for Privilege Escalation
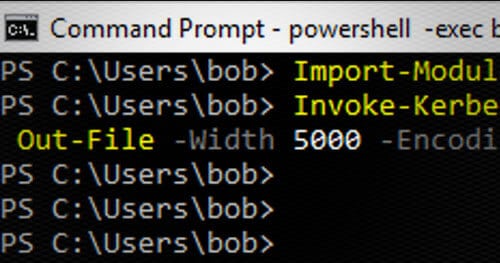
In our experience, Kerberoasting is an attack that is similar to others in that defenders need to fully under it to be able to properly migrate the risks. It’s our goal that through pushing this content into the MITRE ATT&CK framework we have increased the awareness of this TTP so that organizations can be better protected in the future.
Summary of April MITRE ATT&CK RELEASE

MITRE’s Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK™) is a curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary’s lifecycle and the platforms they are known to target. ATT&CK is useful for understanding security risk against known adversary behavior, for planning security improvements, and verifying defenses work as expected.
Privilege Escalation in AWS with PassRole Attacks
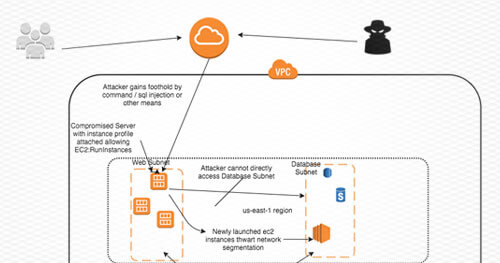
All instances launched by AWS by default have instance credentials supplied by the AWS metadata service. AWS operators can attach PassRole policies given to an instance at launch time.
Breaking Through Single Sign On (SSO)
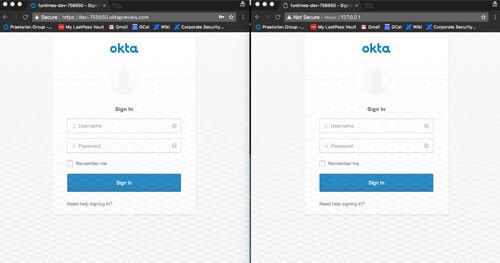
During my internship with Praetorian, I was able to create a new tool—Okta Watering Hole—that was used on some of the red team engagements. I created this tool because our team ran into the issue of not being able to get past two factor authentication on various web portals—so this is how we got around that. Okta Watering Hole sets up a carbon copy of a target Okta site and begins to capture credentials and sessions of visitors. This can be used to check how a company’s procedures and policies stand up to the “next generation” phishing attacks we are beginning to see. This new tool supports traditional phishing attacks as well as targeting two factor authentication devices—meaning perimeter security has to work double time.