Path.Combine Security Issues in ASP.NET Applications
Path traversal vulnerabilities are a common class of web application vulnerability, where an attacker aims to access files outside of the intended directory by using “../” patterns to traverse directories or by using absolute paths. These vulnerabilities are commonly found in file upload or download functionality of an application.
KRACK (Key Installation Attack) Against Wi-Fi Networks
A flaw in the implementation of WPA2-based encryption allows for an attacker within physical range of the wireless network to decrypt traffic from a vulnerable client, allowing for viewing, intercepting, and modifying data in transit. This vulnerability has been assigned CVE numbers CVE-2017-13077 through CVE-2017-13088. There does not yet exist a working public exploit for this attack. However, the research group who discovered it have published their efforts, and working exploit code is likely a matter of days away.
Shadow Brokers After Action Report
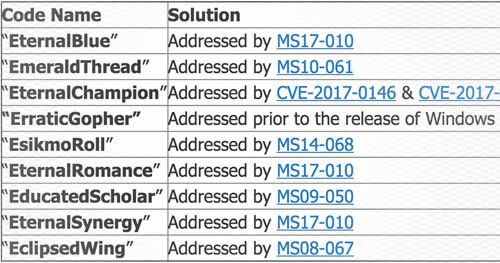
Microsoft released security updates in March that address many of the issues already. Therefore, there are no 0day vulnerabilities included in the toolset that can be used against fully patched versions of Windows. The toolset was built in 2013 which means it doesn’t include Windows 10 and 2016. Legacy versions of Windows are still vulnerable since Microsoft won’t release security updates for them.
Hashjacking: Anyone Can Steal Your Windows Password

There is currently an architectural vulnerability within the Windows SMB authentication protocol that affects modern Windows Operating System. The core of this issue is due to the presumptive nature of current SMB authentication methods. When a user accesses a file share or remote file (by typing “file://” or “” in a browser or file explorer) hashed Windows credentials from the current user are automatically sent to the remote server in attempt to authenticate and access the remote file. The default behavior of assuming the remote server is trusted allows for systems to quickly access file shares in large corporations so that users won’t need to sign in with their company credentials each time to access network resources. However, this implementation presents a significant security risk to user accounts and passwords.
Well-tested Authorization Design Patterns

Authorization is a strange beast. In theory, it appears to be rather straight-forward: a user should not be able to create, read, update, or delete data that it does not have access to. However, from our experience, theory tends to deviate from practice. Missing or incorrect access controls are a dime a dozen for applications we test and this very rarely stems from a complete lack of access controls. More often then not, authorization issues spring up during assessments where the application manages a complex authorization model and an incorrect assumption was made or an edge case was missed. Conversely, we have seen applications that have incredibly complicated authorization models that have zero access control problems.
How to Mitigate Mimikatz WDigest Cleartext Credential Theft
Penetration testers and malicious adversaries often focus on using the easiest attack vector to achieve their objectives. One common attack vector that has been around for several years is to use a tool called Mimikatz and steal cleartext credentials from memory of compromised Windows systems.
Reversing and Exploiting Embedded Devices: The Software Stack (Part 1)
Over the course of the past few months I’ve been traveling around educating people on exploiting embedded devices. My slides alone aren’t able to provide enough information, so I wanted to write everything out for people to digest online. The following blog post is “Part 1”, which will introduce the reader to the software side of embedded devices. I decided to cover software first since most flaws reside within the software stack, ranging from binary applications to drivers. Part 2 will cover the Hardware stack with a focus on educating the reader on how JTAG actually works and how to leverage Hardware modifications to either bypass password protections or to extract secrets that may be baked into the targeted devices.
Broadcast Name Resolution Poisoning / WPAD Attack Vector
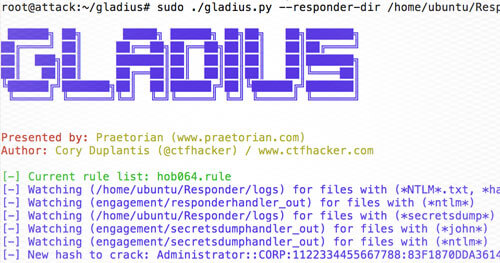
One of the common attack vectors for penetration testing is to leverage an attack known as Broadcast Name Resolution Poisoning. Recently, US-CERT posted an advisory about this attack being used externally. Attackers purchased new generic Top-Level Domains (gTLDS) and setup entries for the Web Proxy Auto-Discovery Protocol (WPAD). This is pretty interesting since it’s an old attack used in a new way. Let’s dive into how Broadcast Name Resolution Poisoning is used during internal penetration testing and go over recommendations for how to fully mitigate all forms of attack.
An Opinionated Series on Why Signal Protocol is Well-Designed: Deniability
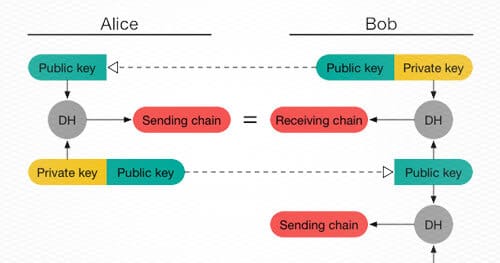
In my previous blog post covering WhatsApp end-to-end encryption, I spoke about Signal Protocol and how certain design decisions allowed Signal Protocol to be efficient on mobile devices. For this blog post, I’ll cover deniable authentication, how it has worked in the Off-The-Record (OTR) Messaging protocol, and how Signal Protocol has approached this problem. Deniable authentication tries to digitally recreate “off-the-record” conversations in the physical realm. If you tell Bob an embarrassing story in-person and Bob proceeds to tell Mallory about that story, it is possible for you to claim that Bob made the story up. Conversely, if you were to “sign” every statement you have ever made to Bob it would be practically impossible to deny that you told that story to Bob.
Engineering Efficiency and Continuous Improvement in Security Services
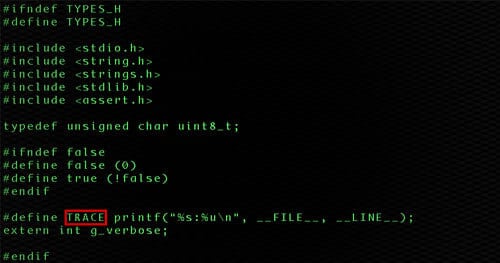
Highlight is a simple utility that creates an image from a text stream, automatically draw boxes around user defined content and automatically blurs sensitive content.
Sometimes we have a text stream, such as the output of a configuration file, and we want to include that as an image into a document. At the same time, we might want to highlight a particular string of text that’s found and we might want to hide other details that might contain things such as passwords. We could use a screen capture utility and then proceed with marking up the image. This leads to inconsistent boxes around text and certainly does not lend itself to automation.
With this utility, the entire process can be automated.