JTAGulator vs. JTAGenum, Tools for Identifying JTAG Pins in IoT Devices
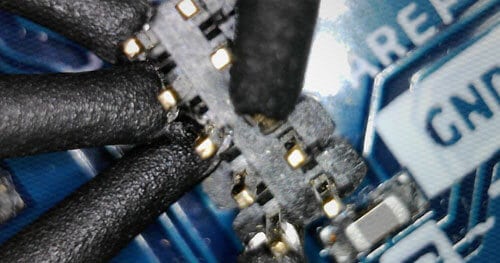
Do you suspect some pins on your device are JTAG? There are several methods out there for identifying if pins are likely to be JTAG or not. One of those methods involves buying a $200 JTAGulator, however there is a cheaper Arduino-based alternative I will be detailing in this post. First I’ll explore the expensive way.
Email Filters: A Reliable Phishing Protection?
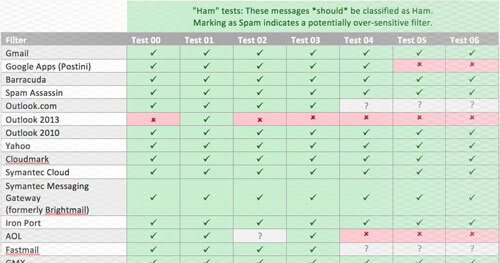
It’s no secret that spear phishing is a prevalent threat and is making an appearance in many CISOs' nightmares. The Verizon’s 2016 breach digest is out and—for anyone who hasn’t looked through it yet—the answer is 30%. That’s the percentage of breaches from 2013 to 2016 that leveraged social engineering tactics to stage a compromise. Of those attacks, phishing accounts for 72% of them. That means that nearly 22% of breaches in the last 3 years have leveraged phishing in some way or another. It's hard enough to secure external and internal assets… but having to secure your employees too? It’s a scary thought. Definitely something to keep one up at night. Current solutions include improving user awareness through training exercises, minimizing and controlling damage through defined incident response programs, and stopping phishing emails before they ever make it to employees' inboxes through email/spam filtering solutions. We're here to talk about the last one. Using a collection of benign and phishy emails alongside a spam filter testing service called Email on Acid, we've taken a stab at comparing 22 different spam filtering solutions. These tests measure each spam filter's ability to stop spear-phishing emails in their tracks. To anyone afraid of long articles, the “tl;dr” reads something like this: Spam filters are okay. They’re not perfect and not terribly intelligent, but they can be effective at times and represent one layer of defense that should be in-place to protect an organization from phishing or spear-phishing attacks.
End-to-End WhatsApp: An Opinionated Series on Why Signal Protocol is Well-Designed

WhatsApp recently announced that client communications are now end-to-end encrypted using Open Whisper System’s “Signal Protocol” (previously Axolotl). This has received quite a bit of press lately due to WhatsApp's massive user base, along with the controversial going dark debates. Less importantly, the crypto-nerd in me loves Signal. Because of all of this, I thought I would write a blog series on some of Signal's design decisions that I feel are well-designed.
Why are JTAG and UART still effective attack vectors for IoT devices?
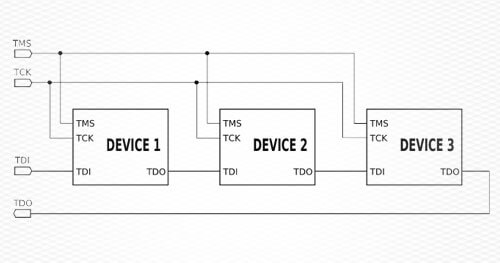
Whether it’s a vulnerable router, an Internet of Things (IoT) connected device, or some other piece of hardware, JTAG and UART debugging test pins left on the device are going to continue to be one of the most effective physical hardware attack vectors available to a malicious actor. Never assume your secrets on IoT devices, such as encryption keys, are safe. You may be wondering what JTAG and UART are, and why they’re left on boards.
Secure Password Storage in Go, Python, Ruby, Java, Haskell, and NodeJS
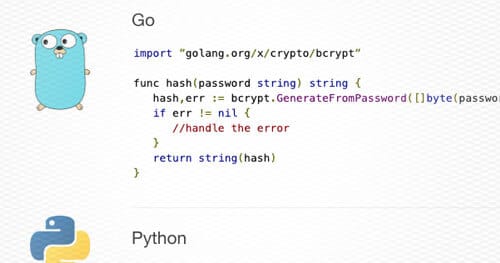
In order to authenticate users, web applications often store user passwords. This can be tricky, because password storage mechanisms are a watering hole for bad advice: there are several solutions to this problem but very few are truly secure. If you store the passwords of your users, your goal should be to make sure that in the event of a data compromise, user passwords should remain safe. The best way to store users passwords is to use a password-based key derivation function (PBKDF) with a sufficient work factor. If your application does not leverage a PBKDF, you should migrate password storage schemes immedietely. More on this later.
Internetwache RE60 Writeup: Symbolic Execution Tramples CTF Challenge
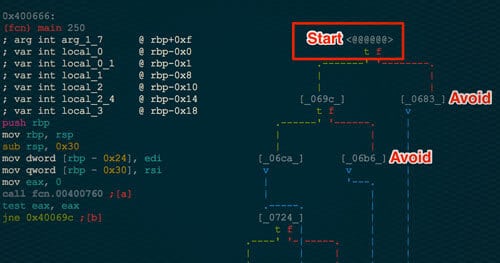
I am always looking for problems that symbolic execution could be applied to in the capture the flag space. This past weekend, this challenge was met during the Internetwache CTF for its RE60 problem. Below I describe the application of symbolic execution to solve the challenge without much knowledge of the inner workings of the binary itself. Symbolic Execution gives the reverse engineer the ability to find a specific path from Point A to Point B in a binary. This path is represented by a series of boolean expressions. These expressions can then be passed to a solver such as Z3 from Microsoft to solve the equation, creating an input that will exercise the found path.
Pentestly Framework: When Pentesting Meets Python and Powershell
Python appears to be an ever growing trend in the security community. Being able to connect Python tools together has proven beneficial for us. Powershell has also seen increasingly more use due to its wide availability in internal environments. Pentestly utilizes the power of these tools together in a familiar user experience.
Machine Learning Tutorial

We see huge benefits of machine learning in the field of computer security. Much of the work we do on a daily basis can be automated and classified by a machine, leaving us to focus on more interesting and challenging problems. One stunning example is the automated binary exploitation and patching research funded by DARPA for the Cyber Grand Challenge. Problems like these are the stepping stones that will lead us to a future of automated computer security. To encourage future candidates (and ourselves) to delve into the world of machine learning, we built a new technical challenge to test the waters. The challenge is based on a CTF problem from SECCON, discovered by @ctfhacker, and features a mysterious compiler that always produces unique binaries.
Hob0Rules Released: Statistics Based Password Cracking Rules
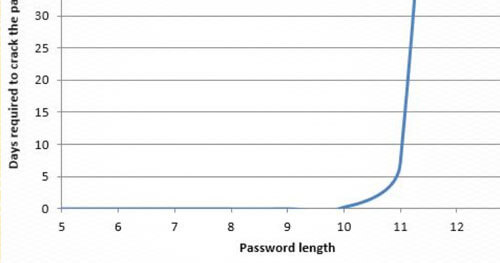
It’s now 2016 and people are still decisively using poor, predictable passwords. Employees around the world will soon be appeasing their mandatory 90-day password rotation by changing their password from ‘Winter2015’ to ‘Spring2016’. This happens in nearly every company – you would be surprised. Previously, I conducted password research to determine common traits of passwords, which was presented at various conferences. The password cracking rules that Praetorian utilizes for all hash cracking have now been released for Hashcat (described below) which are based on these findings. A quick compromise list of 64 of these rules have been released as hob064 and a more extensive ruleset has been released as d3adhob0 for public use. These rulesets were made to compete against their industry standard counterparts, Best64 and d3ad0ne. Both of the released rulesets have bypassed their counterpart in both time speed and number of hashes cracked and will continue to improve. The two sets of rules are living lists and change as the environment of passwords changes.
Ruby Unsafe Reflection Vulnerabilities
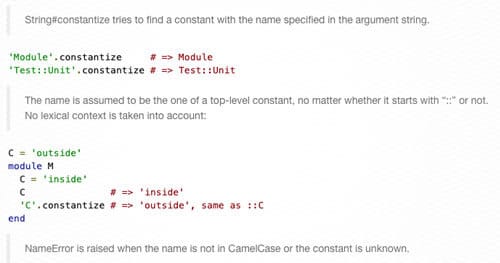
One of the interesting properties of Ruby is the fact that everything is an object. The manipulation of objects at runtime is what makes Ruby so flexible and interesting as a language. At its heart, this is the idea behind reflection. Reflection is a tool to allow a program to examine and modify its own behavior at runtime, granting programmers the ability to simpilify certain constructs (e.g. framework development, dependency resolution).