July 5th, 2024 Update
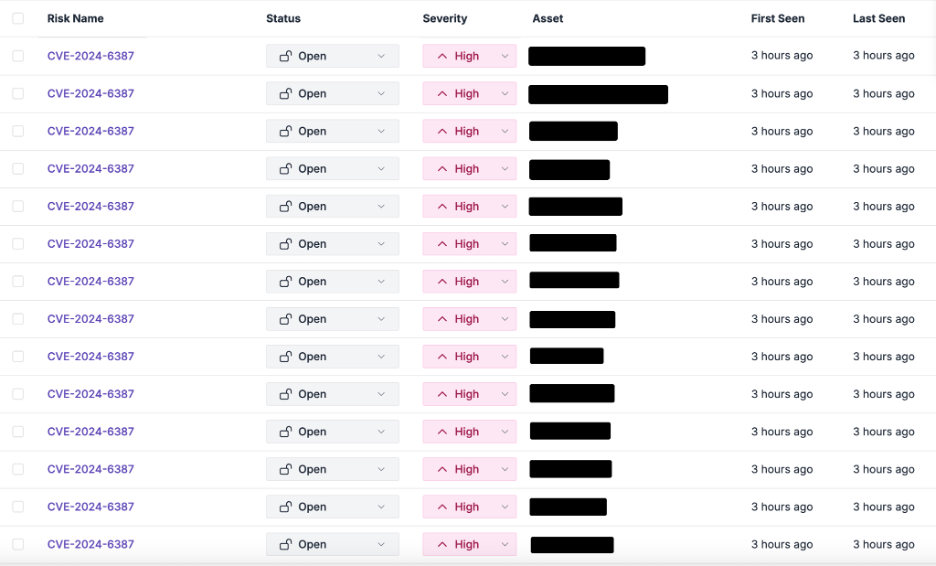
Chariot detected numerous instances of CVE-2024-6387 in our customers’ environments this week. We have notified all of our impacted customers to begin the remediation process.
On July 1, 2024, the Qualys Threat Research Unit (TRU) announced an unauthenticated remote code execution in OpenSSH’s sshd server. Cataloged as CVE-2024-6387, the vulnerability is a regression of CVE-2006-5051, hence its nickname: “RegreSSHion”. In addition to versions impacted by CVE-2006-5051, RegreSSHion affects OpenSSH 8.5p1 – 9.7p1. TRU determined the most recent version of OpenSSH (9.8p1) was not affected.
To ensure our customers match the velocity of novel threats, Praetorian monitors dozens of information sources for new vulnerabilities and attack techniques. After learning about RegreSSHion, we immediately developed a Chariot capability to identify impacted sshd servers. The capability is now running in the platform, and impacted customers will receive notifications to patch shortly.
How Does Chariot’s Capability Work?
Simplicity is bliss. Chariot’s RegreSSHion capability retrieves the server’s SSH banner and compares it against all known vulnerable versions:
SSH-2.0-OpenSSH_8.5p1
SSH-2.0-OpenSSH_8.6p1
SSH-2.0-OpenSSH_8.7p1
SSH-2.0-OpenSSH_8.8p1
SSH-2.0-OpenSSH_8.9p1
SSH-2.0-OpenSSH_9.0p1
SSH-2.0-OpenSSH_9.1p1
SSH-2.0-OpenSSH_9.2p1
SSH-2.0-OpenSSH_9.3p1
SSH-2.0-OpenSSH_9.4p1
SSH-2.0-OpenSSH_9.5p1
SSH-2.0-OpenSSH_9.6p1
SSH-2.0-OpenSSH_9.7p1
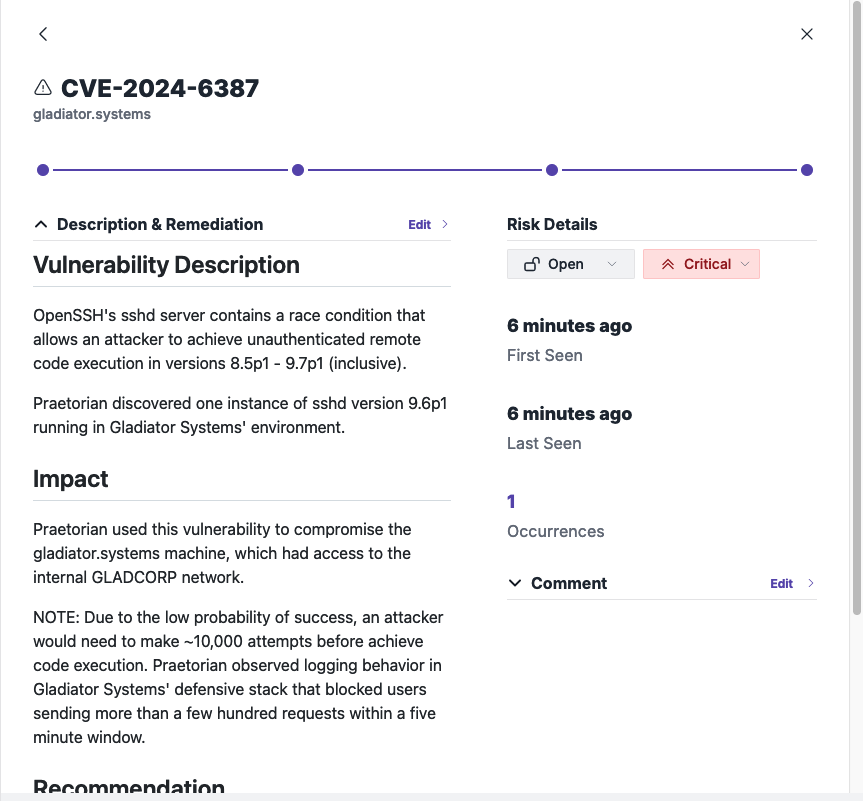
This technique is non-invasive and harmless to the target server. When the capability flags an asset, our Managed Service team collaborates with the impacted client to assess the full business impact, including exploitability, affected assets, and existing mitigations.
Getting Started with Chariot
Curious if CVE-2024-6387 impacts your organization? Start a free ASM scan to find out.