NSA keeps HeartBleed quiet, everyone left vulnerable. Could you or your organization have been affected?
For anyone who has not heard, a critical SSL vulnerability called HeartBleed was made public earlier this week that affects a widely used version of OpenSSL. In this post, I will demonstrate the HeartBleed vulnerability being exploited on a vulnerable mobile banking application and backend server within our test environments.
The vulnerability occurs in the Heartbeat extension of the SSL/TLS protocol, and it impacts version 1.0.1 and beta versions of 1.0.2 of OpenSSL. If you want to learn more about the mechanics of the Heartbeat (HeartBleed) flaw, I highly recommend watching Dr. Zulfikar Ramzan’s video explanation on Vimeo. If you want to see it exploited in a very simple way, read on.
HeartBleed Exploit Tool
The following exploit tool, authored by Praetorian’s Nick Angelou and Kelby Ludwig, extends Jared Staffor’s original POC of the HeartBleed OpenSSL vulnerability to allow larger organizations to scan multiple hosts in a more efficient manner.
Contact Praetorian to request exploit code »
For demo purposes, I will be exploiting the Heartbeat flaw in our Damn Vulnerable Apps (DVA) project we developed last year. We released the DVA mobile banking apps and backend server code last year as a toolset to help educate and empower mobile developers to write more secure code. I conducted the following exploits in a local testing environment that was still using the vulnerable version of OpenSSL.
Mobile Banking App (User’s POV)
Below is a quick example of actions a typical user may take while using our fake mobile banking application: 1) register for an account, 2) log in, 3) access account information. Much like a traditional mobile banking application, users can also transfer funds between accounts and to other users.
The Attacker Exploiting HeartBleed Vulnerability
Armed with an exploit script, like the one our security engineers designed, an attacker can extract user credentials out of the mobile banking backend server’s memory without leaving evidence of his crime.
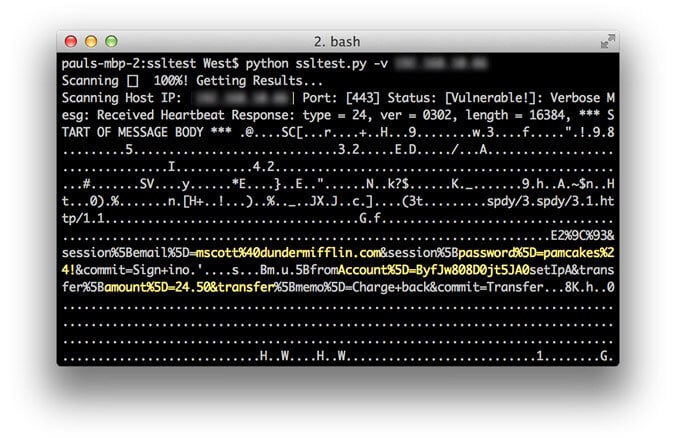
$ python ssltest.py –v x.x.x.x
The output above shows leaked credentials recently used by the user to log in to his mobile banking account. The username is mscott@dundermifflin.com and his password is pamcake$!. It also reveals recent sensitive account information and activity, such as recent transactions and session tokens.
It’s that simple.