Overview
In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities that are likely to impact the security of leading organizations. Exposed embedded devices are a particular area of concern because they typically do not have host-based security controls such as EDR or Antivirus, but still provide an internal network foothold. If an attacker gains persistence on such devices, they can dwell on them for a long period of time while slowly planning further attacks. In the course of our research, we discovered a high risk vulnerability in the Fujitsu IP series real time video transmission line of devices.
All Fujitsu IP series devices running firmware released prior to July 26, 2023 contain hard-coded backdoor credentials that cannot be changed by the end user. This form of backdoor is not acceptable in modern software, and is reminiscent of backdoors more frequently seen in embedded devices from the 1990s.
Praetorian discovered the credentials by reverse engineering firmware update files, and responsibly disclosed this vulnerability to Fujitsu on Tuesday, May 30, 2023. The vulnerability gained the designator CVE-2023-38433, and the vendor released a patch on July 26, 2023. For details about the CVE from NIST NVD, see https://nvd.nist.gov/vuln/detail/CVE-2023-38433.
CISA also released a Cybersecurity Advisory for this vulnerability.
The following devices contain the vulnerability:
IP-HE950E firmware versions V01L001 to V01L053
IP-HE950D firmware versions V01L001 to V01L053
IP-HE900E firmware versions V01L001 to V01L010
IP-HE900D firmware versions V01L001 to V01L004
IP-900E / IP-920E firmware versions V01L001 to V02L061
IP-900D / IP-900?D / IP-920D firmware versions V01L001 to V02L061
IP-90 firmware versions V01L001 to V01L013
IP-9610 firmware versions V01L001 to V02L007.
Impact
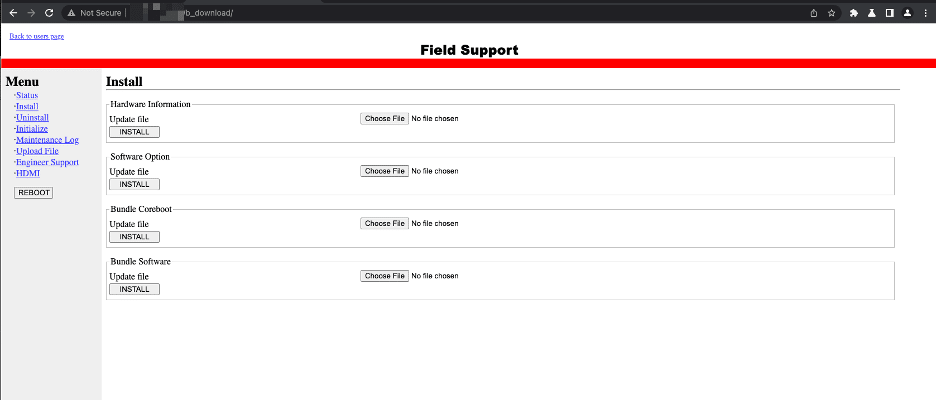
These hardcoded credentials provide administrative access to the devices, which an attacker can use to upload files and firmware updates, as figure 1 shows. A skilled attacker could leverage these vulnerabilities to obtain persistence on the devices.
Figure 1: Field Support Page on Fujitsu IP-9xx Device
Mitigation
Users of the IP series devices should update their devices to the latest version offered by Fujitsu.
Technical Details
The vulnerability is a hard-coded password that end users of the device cannot change without updating the firmware. We discovered these credentials by examining the device software updates.
The vulnerability manifests differently for newer IP-HE9xx devices that are running the lighttpd web server, and the older IP-9xx devices that run the thttpd web server. Both vulnerabilities involve hard-coded credentials, but the credentials for the newer devices only work on a “Field Support” page via the http://{DEVICE_IP}/b_download page. This page provides administrative functionality, such as uploading new firmware files and modifying key system functionality. There is no way for the end user to modify these credentials.
On older IP-9xx devices, the hardcoded credentials provide access to the same device administrator portal that the user-configured administrator account provides. The older devices also have a Field Support page that allows uploading files to update system components. Just like the IP-HE9xx devices, the end user cannot modify the hardcoded credentials.
A skilled attacker could upload a malicious update or software component file to gain remote code execution on the underlying system for both newer and older Fujitsu IP-series devices.
Discovery
For newer IP-HE devices we discovered the vulnerable behavior by analyzing the software update (https://www.fujitsu.com/global/products/computing/peripheral/video/download
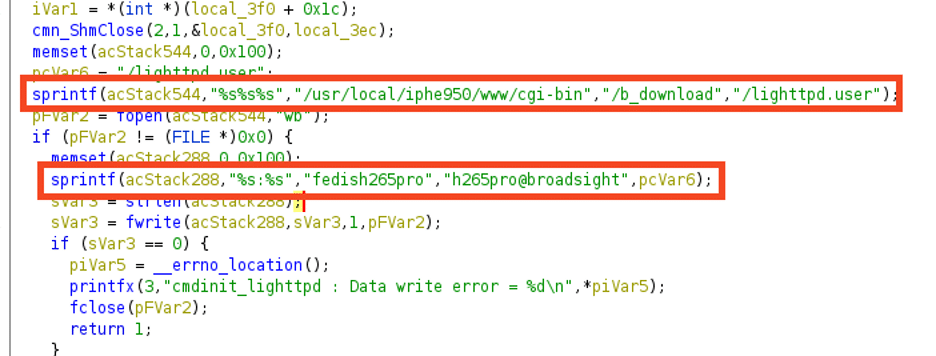
/iphe950e-v01l052.html) and finding that the cmdinit binary at /usr/local/iphe950/bin/cmdinit adds a new user to the lighttpd.user file for the /b_download path and Basic authentication realm, as figure 2 demonstrates.
Figure 2: The initialization application wrote hardcoded credentials to the lighthttpd configuration file.
For the older devices, we discovered the vulnerable behavior by analyzing the software update
(https://www.fujitsu.com/global/products/computing/peripheral/video/download
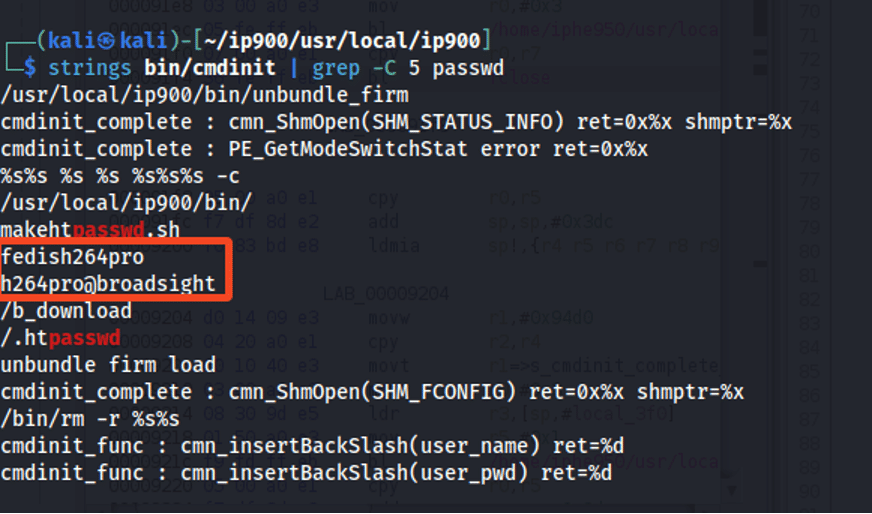
/ip900e-v02l061.html) to determine that the cmdinit binary at /usr/local/ip900/bin/cmdinit wrote hardcoded credentials to the system’s .htpasswd file, as figure 3 shows. Thttpd uses the .htpasswd file to determine which users can log in to the device’s web console.
Figure 3: The strings command revealed hardcoded credentials within the IP-9xx cmdinit binary.
Hardcoded Credentials
Given Fujitsu announced and patched the CVE over 30 days ago, Praetorian is releasing the clear-text hardcoded credentials so that users of these devices can verify if their systems are vulnerable to an unauthorized attacker.
IP-HE9xx Devices
Username: fedish265pro
Password: h265pro@broadsight
IP-9xx Devices
Username: fedish264pro
Password: h264pro@broadsight
Conclusion
Advanced threat actors often will perform reverse-engineering of IoT devices in order to gain initial access to a target network. We cannot simply assume that exposing a device on the Internet is safe just because there are no publicly known vulnerabilities. Praetorian engineers therefore perform vulnerability research on exposed assets and devices in order to identify vulnerabilities before malicious actors can. In this case, a sophisticated attacker could have exploited Fujitsu IP-series devices to gain an internal foothold within large corporations around the world.
The best defense is a proactive one. Understanding your attack surface better and taking proactive steps to reduce exposures and better assess the impact of new vulnerabilities is a critical step of this process. If you’d like to know how the Chariot continuous offensive security platform can help you stay one step ahead of attackers, please don’t hesitate to contact us for a demo.