Earlier this month, Praetorian released its automation for emulating adversary tactics, techniques, and procedures (TTPs) based on the MITRE ATT&CK framework. We’ve gotten a number of requests from users asking for more detailed instructions on how to get started with the tool. This blog post accompanies the recently released video tutorial.
GitHub Release: Praetorian’s Metasploit Automation of MITRE ATT&CK™ TTPs
A quick start guide to the public release of Praetorian’s Metasploit automation of MITRE ATT&CK™ TTPs. Access the full toolset on GitHub. If you’re more textually inclined, read on.
The first thing you’ll want to do is get your lab setup. We’ve recently become a big fan of DetectionLab from clong so we integrated our automation into a fork. If you’re abstaining from cloud infrastructure or just enjoy running on your own hardware, you’ll need at least 1 Windows workstation VM, another Windows VM (preferably a server), and a Linux VM. We’ve had the most stable results with Ubuntu. The Windows VMs don’t have to be on a domain, but you won’t be able to test a number of the TTPs otherwise.
Once your lab is properly configured, follow the installation instructions. If you run into any issues, please feel free to add a new issue and we’ll look into updating the project or clarifying any instructions.
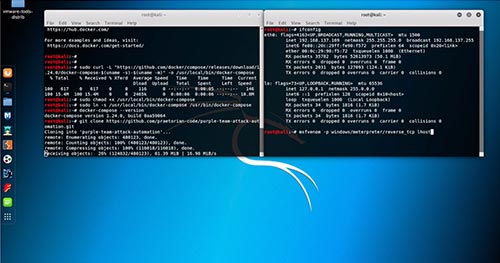
So you have your lab and your docker container running. Now what? Well you need to get a meterpreter agent up and running on one of the Windows boxes. If you’re running your MSF server on an external server, we recommend setting up a valid SSL certificate. Instructions can be found in our operational guide. We recommend installing Metasploit utilizing the nightly installer and running msfvenom to generate a payload natively versus using the docker msfvenom. From there, whitelist the payload and run it on your Windows box. We provided a sample resource script in the operational guide that you can utilize to start your listener.
The next step is actually running a module. The above operational guide provides an example of using TTP T1028 to start the WinRM service and executing calc via WinRM. To view the list of modules provided by Praetorian for Purple Team emulation, you can run “search purple” or view the current list here.
If you have any questions or have any requests for modules, feel free to reach out to us!