It’s now 2016 and people are still decisively using poor, predictable passwords. Employees around the world will soon be appeasing their mandatory 90-day password rotation by changing their password from Winter2015 to Spring2016. This happens in nearly every company – you would be surprised. Previously, I conducted password research to determine common traits of passwords, which was presented at various conferences. The password cracking rules that Praetorian utilizes for all hash cracking have now been released for Hashcat (described below) which are based on these findings. A quick compromise list of 64 rules have been released as hob064 and a more extensive ruleset has been released as d3adhob0 for public use.
These rulesets were made to compete against their industry standard counterparts, Best64 and d3ad0ne. Both of the released rulesets have bypassed their counterpart in both time speed and number of hashes cracked and will continue to improve. The two sets of rules are living lists and change as the environment of passwords changes. The outline of the previous research, from which many of these rules are based, is defined in my last blog post “Statistics Will Crack Your Password”. Many of the internal rulesets that we utilize take advantage of these scenarios and their various combinations.
Machine Learning:
Currently, I am putting together a more comprehensive tool which will analyze the success of individual rules and autonomously improve the ruleset. We can pull from several sources of data to train the ruleset. Internally, this is referred to as project Kraken, and will be released for public consumption when appropriate. This tool will also be utilized to deliver our clients value when performing password audits on their environment over time.
Why You Should Audit Your Passwords
IT Manager:
As an IT manager you should be implementing policies to help protect your users. Running password audits to determine where areas of weaknesses exist, is an important metric to keep your organization from being compromised. Run these rule lists against your domain hash dump to see how many of your employees are susceptible to quick compromise from weak passwords. Attackers are doing this, why shouldn’t you?
Everyone Else:
You might think your password is secure because you followed all the rules laid out by your IT organization, but you might be surprised by how universally people think about building a password. Put your password into an NTLM hash generator and run these rules with hashcat against your hash to see if it can be easily cracked by an attacker. Hopefully if you are reading this, you care enough about security to not fall into these password attacks.
Get the rules:
The rules were created for the password cracking engine, hashcat, which has recently been released as open source. If you don’t have hashcat, download it: http://hashcat.net/hashcat/
git clone https://github.com/hashcat/hashcat.gitcd hashcatmake
If you now have hashcat you can Git clone from the praetorian GitHub page for rules:
git clone https://github.com/praetorian-inc/Hob0rules.git
This also comes with wordlists that are recommended to use with these rules. However, you may consider adding your own custom words based on the context of whatever you are cracking.
Use the rules:
Cracking NTLM hashes you dumped from an active directory domain controller?
hashcat –a 0 –m 1000 wordlists/rockyou.txt -r hob064.rule -o cracked.txt
This will store the cracked passwords in a file called cracked.txt.
Keep in mind that this will not crack lots of passwords but will at least give you a quick and easy way to find particularly weak passwords within a set of hashes.
Fix the problem:
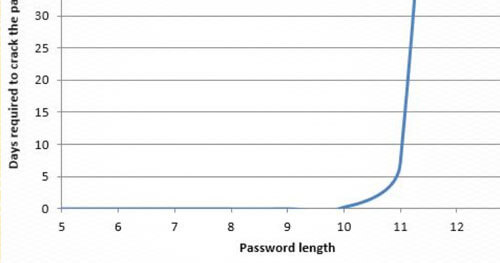
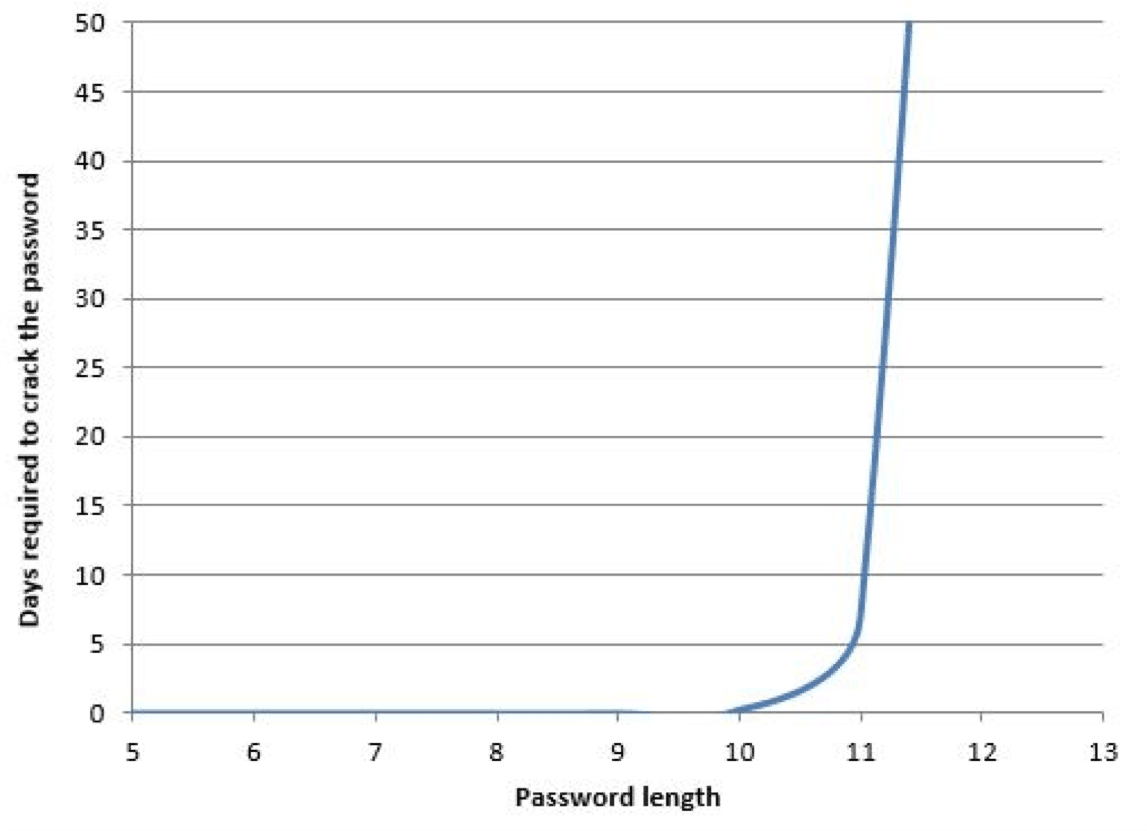
Transition to 16 character minimum passwords. This is not as scary as it sounds. For years people have had the wrong idea about passwords ingrained in their heads. Why not choose a specific sentence that is easy to remember. The password: PraetorianPicksPrettyPowerfulPasswords is extremely strong due to its length and it’s significantly easier to remember than the weak 8 character password q#rC3piV.
The difference in strength between these two passwords is extraordinary. The long easy to remember password would take a quindecillion years (yes that’s a real number) to brute force at 4 billion guesses per second. Whereas, using the same machine, it would take under 3 days to guarantee uncovering the shorter password. Complexity doesn’t make your password much more secure, length does. Make a compromise that if you switch to 16 character minimums, passwords should only be rotated twice a year. In case you were curious it would take over 22 billion years to brute force a 16 character password that just uses letters. It is possible for attackers to attack this structure by assembling random sequences of words, but I promise the key space for doing so is much smaller.
Use password managers with two factor authentication:
LastPass and OnePass are good solutions to use so that all of your passwords are strong, secure and random. You don’t even need to know what your passwords are for websites anymore. You just need one passphrase and your phone for a second factor of authentication. This second form of authentication protects you against having one password access all the eggs in your basket.
When you think about it, these are really simple solutions for an issue that protects your entire livelihood. Think about it people.