Background
On March 30, 2022, Praetorian published remediation details for a remote code execution vulnerability for Spring Core on JDK9+ (CVE-2022-22965). A patch for vulnerable systems is now available and Praetorian has notified those affected through our Chariot offering.
Hunting Opportunities
Covering all our bases this early in the disclosure timeline can be a significant challenge. As threat hunters, we want to spend our time chasing leads with the highest probability of uncovering malicious activity. As of now, at least one POC exploit is publicly available. Over time, we expect attackers to combine different payloads to take advantage of the vulnerability for different implementations. This can reduce the effectiveness of our efforts as defenders if our hunts are based on non-essential attributes of the initial POC.
The two opportunities that present the highest probability of identifying successful exploitation are:
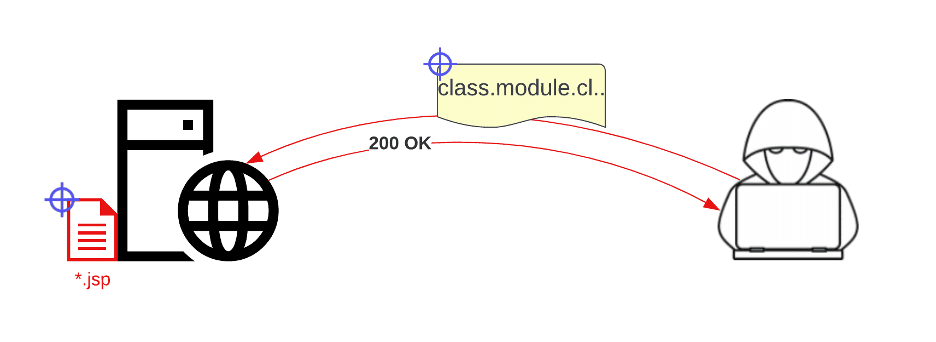
- Searching for the pattern `/.*.?[Cc]lass..*/`, and the string `class.module.classLoader` in the request body or query parameters of HTTP requests followed by a 200 response code.
- Review of files written to the webserver by the user the application is running under.
The first option requires the most visibility, which is often not available due to the cost of retaining access logs. It may be beneficial to explore temporarily collecting these logs to cover the delta between disclosure and patching. Alternatively, most IDSs and WAFs can be set to log and alert on the pattern above. If you have an EDR or logging configuration that covers file creation, the second option only requires a search for files created within the vulnerable application’s working directory since disclosure. Investigation of individual files should prioritize those with a `.jsp` extension. Without file creation logging the next best option would be to scan vulnerable servers’ working directories for `.jsp` files created after disclosure. Take care to exclude backup and development servers that don’t have exposed services to prevent excessive results.
The next best opportunity to uncover compromise is to hunt for general post-exploitation activity. This includes normal threat hunting activities such as scanning for webshells using file signatures, hunting for webshell activity that matches published POCs (e.g. `/pwd=[^&]*&cmd=.*/`), placing additional scrutiny on AV and EDR alerts, and manually auditing process creation on vulnerable servers.
Way Ahead
It’s always a good idea to keep issues like this on your team’s radar until after the vulnerability has been remediated. Keeping a lookout for intelligence on newer implementations can inform your hunting strategy and prevent things from falling through the cracks. For example, future iterations of the exploit may leverage different file extensions. It’s also good to maintain visibility over likely post-exploitation activity to catch anything missed during the initial effort.
