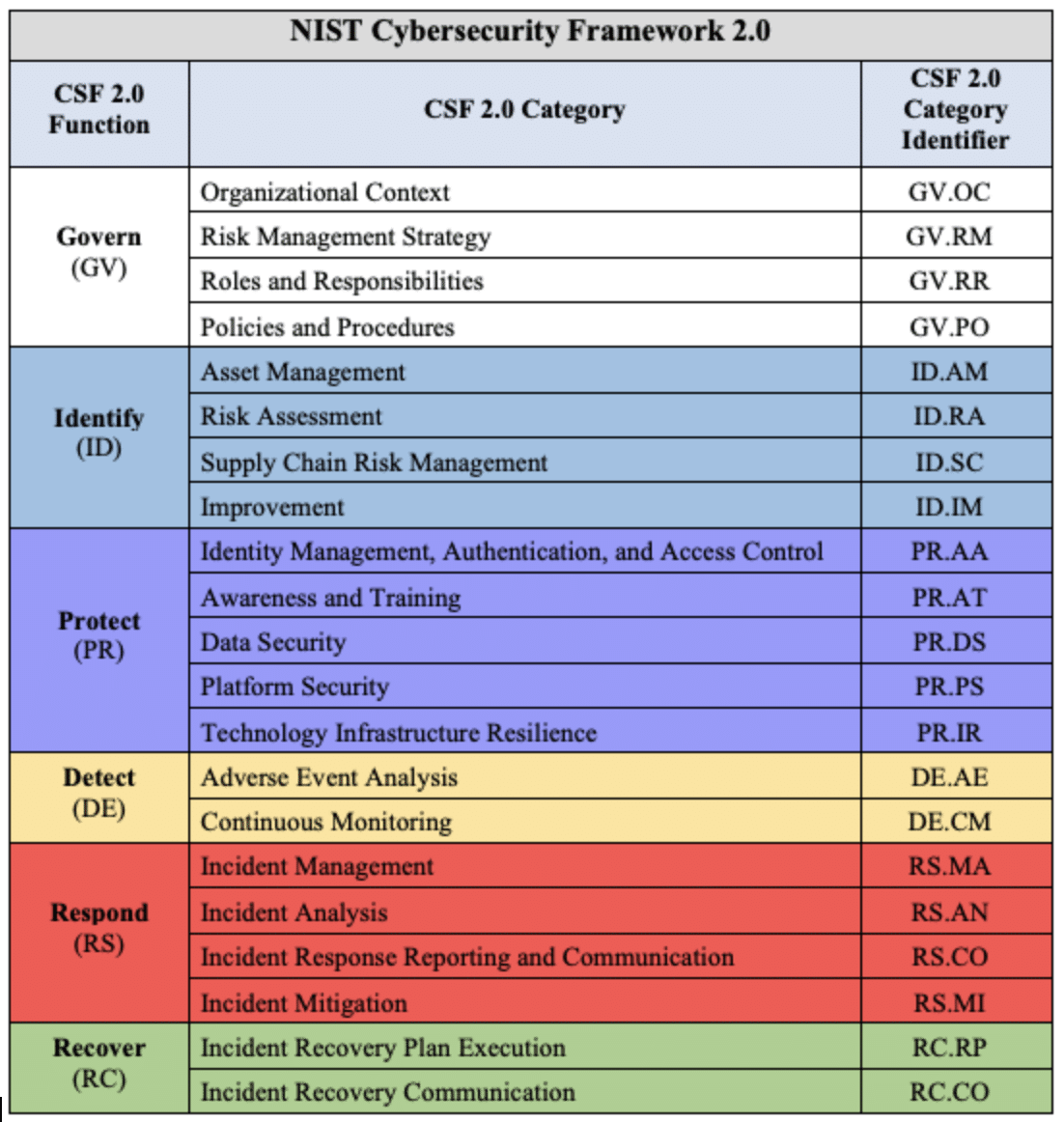
The National Institute of Standards and Technology (NIST) recently released the latest draft of the Cybersecurity Framework (CSF) 2.0, incorporating numerous updates and improvements over its predecessor. Among these changes, the addition of the Governance function has generated significant buzz within the cybersecurity community. We also are particularly excited about the modification of subcategories in the Protect function of NIST CSF 2.0 to address People, Process, and Technology (PPT) effectiveness. This restructuring aligns with our existing scoring methodology and philosophy around how organizations should benchmark and track improvement of their security program.
Why Incorporate People, Process, and Technology to NIST CSF 2.0?
In our previous blog posts, we discussed how our scoring methodology helps enterprises benchmark their security program and track improvement over time. By scoring the PPT aspects of a security program, organizations can gain a more accurate and insightful understanding of their security posture. This multifaceted evaluation method allows for a more targeted identification of vulnerabilities, risks, and areas for improvement. More importantly from our perspective, it also provides the foundation for a holistic security strategy that is adaptable and resilient in the face of emerging threats.
Assessing the People aspect of a security program involves evaluating the skills, knowledge, and awareness of an organization’s workforce in relation to cybersecurity. This can help identify areas where additional training, resources, or personnel are needed, as well as provide insight into the effectiveness of current security policies and practices. By scoring this aspect separately, organizations can better understand the role that human factors play in their overall security posture and tailor their response accordingly.
Similarly, assessing the Process aspect of a security program enables organizations to review policies, procedures, and governance. This encompasses incident response, access control effectiveness, and regulatory compliance. A distinct score for this aspect aids in pinpointing improvement areas and prioritizing security enhancement efforts.
Finally, the Technology aspect of a security program focuses on the tools, systems, and infrastructure that support an organization’s cybersecurity efforts. Scoring this component independently allows for a deeper understanding of the efficacy of current solutions, while highlighting areas where new or updated technologies could enhance security.
Integration of PPT in NIST CSF 2.0
PR.AA-05: Access permissions, entitlements, and authorizations are managed and enforced, incorporating the principles of least privilege and separation of duties (formerly PR.AC-3 and PR.AC-4) (People & Process)
Enforcing access permissions, entitlements, and authorizations based on the principles of least privilege and separation of duties is critical for an enterprise because it minimizes the risk of unauthorized access, data breaches, and insider threats. This approach ensures that employees have only the access necessary to perform their job functions, reducing the likelihood of accidental or malicious misuse of sensitive information. Primarily, it is a people and process subcategory because it involves defining, implementing, and maintaining clear policies, procedures, and roles within the organization.
PR.AA-06: Account activities and access events are audited and monitored to enforce authorized access (formerly PR.AC-1 and PR.AC-3) (Process)
Auditing and monitoring account activities helps enterprises maintain authorized access and detect security threats. The primary benefits of this subcategory include increased visibility into user activities, early identification of unauthorized access attempts or unusual behavior, and the ability to take timely corrective actions to mitigate risks. This is primarily a process subcategory because it involves establishing and implementing systematic procedures for collecting, analyzing, and reporting on access-related events.
PR.AA-01: Identities and credentials for authorized users, processes, and devices are managed by the organization (formerly PR.AC-1) (Technology)
Managing identities and credentials for authorized users, processes, and devices is essential for enterprise security. This technology subcategory reduces unauthorized access risks by using IAM systems and MFA solutions to automate identity management. Thus, enterprises can improve their security posture and protect their digital assets and infrastructure.
For organizations benchmarking against the CSF, these new subcategories ensure comprehensive scoring, while not being needlessly complex. Furthermore, these subcategories indicate the cybersecurity industry as a whole is aligning with what we have long considered best practice in scoring methodology.
Other Changes and Improvements of Note in NIST CSF 2.0
Cybersecurity Governance
The new Govern function covers organizational context, risk management strategy, policies and procedures, and roles and responsibilities. This addition highlights the importance of integrating cybersecurity practices into an organization’s broader management and oversight processes, enabling more effective decision-making and resource allocation.
Previously, the Identify category of the CSF had included some of these subcategories.Providing a separate Govern function ensures more accuracy when organizations analyze effectiveness. It also fosters a culture of accountability and transparency within an organization, which promotes adherence to cybersecurity policies and best practices. In previous versions of the CSF this was not a major focus.
Universal Cybersecurity Outcomes
The CSF 2.0 Core Draft shifts its focus toward universally applicable cybersecurity outcomes, removing language specific to critical infrastructure. Before this update, the language’s focus on critical infrastructure limited its applicability to a narrower range of industries. However, with the new changes, the framework is now more inclusive and versatile, making it an essential resource for organizations of all sizes and sectors.
This broader focus on universally applicable outcomes also emphasizes that cybersecurity is not just a concern for a select few industries. In today’s interconnected digital world, every organization needs to take cybersecurity seriously, as cyber threats continue to evolve and become more sophisticated. By adopting the CSF 2.0 and its universally applicable outcomes, organizations can prepare to face these challenges head-on and protect their valuable digital assets.
Prevention, Detection, and Response
CSF 2.0 emphasizes the prevention of cybersecurity incidents through outcomes in the Govern, Identify, and Protect Functions, and incident detection and response through the Detect, Respond, and Recover Functions. This balanced approach ensures that organizations are prepared to prevent incidents and have the necessary tools to respond and recover when incidents occur.
Supply Chain Risk Management
In the updated CSF 2.0, the framework emphasizes outcome-driven approaches to cybersecurity supply chain risk management. This focus is essential for comprehending and addressing potential risks stemming from third-party vendors and suppliers, which ultimately contributes to safeguarding an organization’s digital assets. Some of the subcategories relating to supplier involvement in detection, response and recovery exercises have also been moved and simplified, while maintaining the spirit of the original subcategory.
Continuous Improvement
A new Improvement Category in the Identify Function emphasizes the importance of continuous improvement in an organization’s cybersecurity efforts. This encourages organizations to constantly review and enhance their cybersecurity strategies, ensuring they remain up-to-date with evolving threats and vulnerabilities. Included within this is a general subcategory relating to continuous improvement of processes and activities across all of the CSF Functions, this encompasses several of the slightly duplicative subcategories such as PR.IP-7, PR.IP-8, RS.IM-1, and RS.IM-2.
Assessment of Security Controls
The updates in CSF 2.0 facilitate the assessment of security controls by providing a comprehensive framework that covers all aspects of cybersecurity, from prevention and detection to response and recovery. Organizations can use the CSF to evaluate the effectiveness of their existing security controls and identify areas for improvement. This comprehensive assessment allows organizations to make informed decisions about resource allocation and prioritize their cybersecurity investments. The development of implementation examples will address the greater security community’s desire for direction in how they should implement controls to address the subcategories of the CSF.
Resilience of Technology Infrastructure
A new Protect Function Category focuses on the resilience of technology infrastructure, emphasizing the need to maintain and protect critical systems and data even in the face of cybersecurity incidents. This resilience helps to minimize disruptions and ensures the continuity of essential operations.
Incident Response Management
New Categories in the Respond and Recover Functions highlight the importance of cybersecurity incident response management, including incident forensics. By incorporating these elements into the CSF, organizations can better prepare for and manage cybersecurity incidents, mitigating their potential impact and facilitating a faster recovery.
Image Source: Discussion Draft of the NIST Cybersecurity Framework 2.0 Core