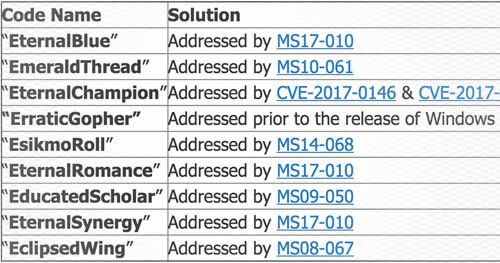
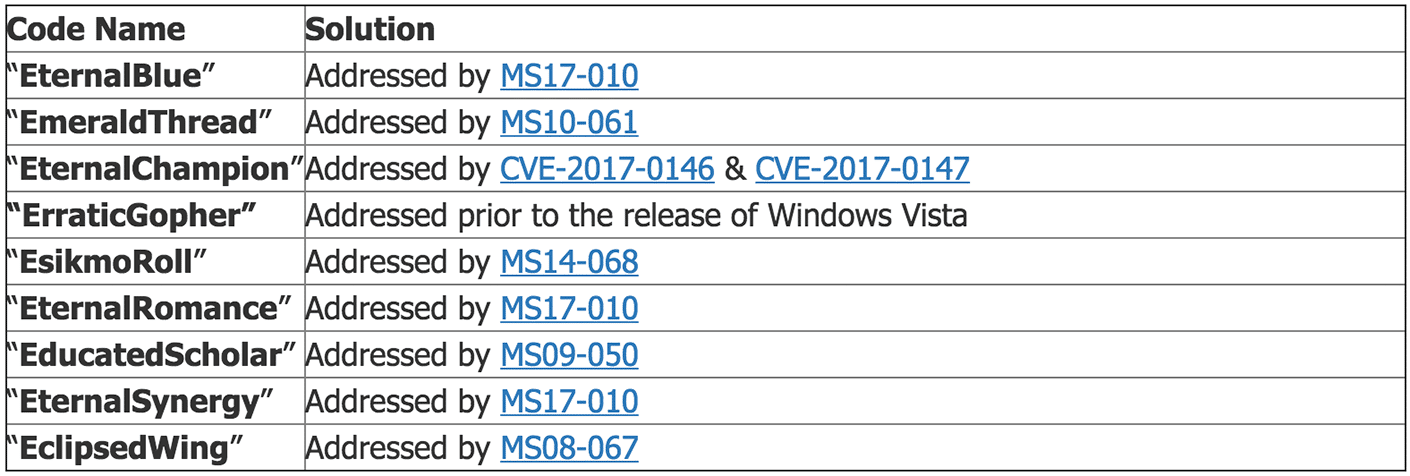
The Shadow Brokers group released the NSA toolset for hacking Windows systems.
Microsoft released security updates in March that address many of the issues already. Therefore, there are no 0day vulnerabilities included in the toolset that can be used against fully patched versions of Windows. The toolset was built in 2013 which means it doesn’t include Windows 10 and 2016. Legacy versions of Windows are still vulnerable since Microsoft won’t release security updates for them.
Impact
An attacker is able to exploit unpatched (or legacy) versions of Windows that have certain ports exposed to other systems on the network. Exploits are publicly available in binary form.
Affected Versions of Windows
- Windows 7
- Windows 2008
Legacy versions of Windows: Many of the exploits affect legacy versions of Windows. Three specific exploits were also released that only affect legacy versions of Windows.
Not Directly Affected
- Windows 10
- Windows 2016
Note: The affected Windows versions may be vulnerable but are not directly exploitable using the publicly released tools using their default configuration.
Recommendations
- Make sure all Windows systems are being patched on a regular basis and being verified using a vulnerability management program.
- Isolate all legacy versions of Windows from other systems on the network.
- Ensure ports like SMB and RDP are never directly exposed to the Internet.
- Focus on basic attacks such as those included in our Top 5 Report.
References
- Microsoft Blog: Protecting customers and evaluating risk
- Praetorian Report: How to Dramatically Improve Corporate IT Security without Spending Millions
- Public GitHub clone: “Lost In Translation” leaked toolsets