Why Azure B2C ROPC Custom Flows Are Inherently Insecure

Microsoft’s Azure Active Directory B2C service allows cloud administrators to define custom policies, which orchestrates trust between principals using standard authentication protocols. One such custom policy that B2C defines by default is the Resource Owner Password Credentials (ROPC) flow, which implements the OAuth standard authentication flow of the same name and allows users to simply […]
Technical Advisory – Azure B2C – Crypto Misuse and Account Compromise
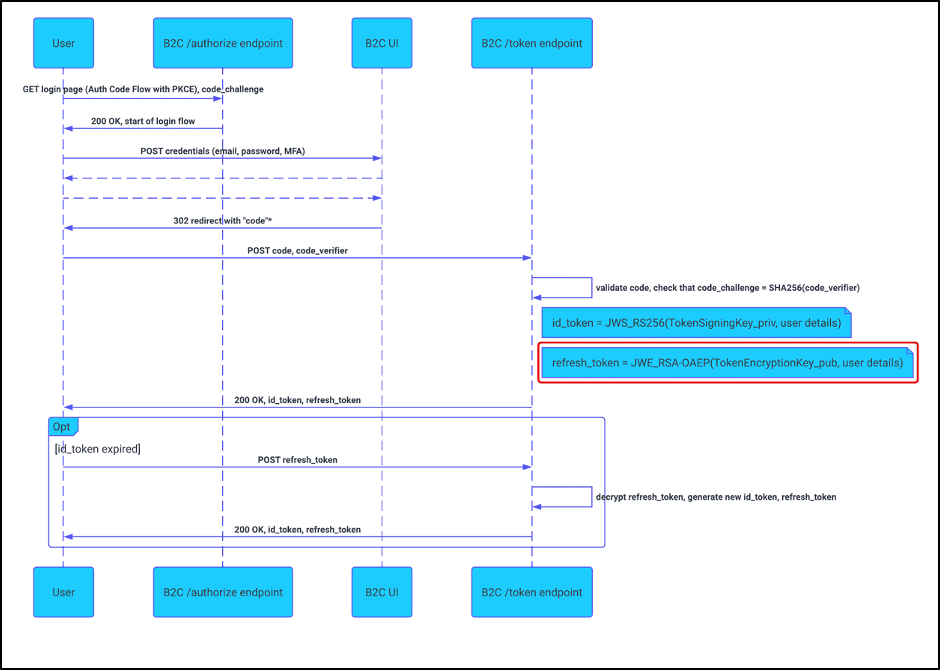
Microsoft’s Azure Active Directory B2C service contained a cryptographic flaw which allowed an attacker to craft an OAuth refresh token with the contents for any user account. An attacker could redeem this refresh token for a session token, thereby gaining access to a victim account as if the attacker had logged in through a legitimate […]
Guest who? Insecure Azure Defaults!
Introduction Azure has an insecure default guest user setting, and your organization is probably using it. The default settings Azure provides would allow any user within the organization (including guest users) to invite guest users from any domain, bypassing any central identity management solutions (e.g. Okta, Auth0) and onboarding processes. Additionally, an attacker may use […]