Helpdesk Telephone Attack: How to Close Process and Technology Gaps
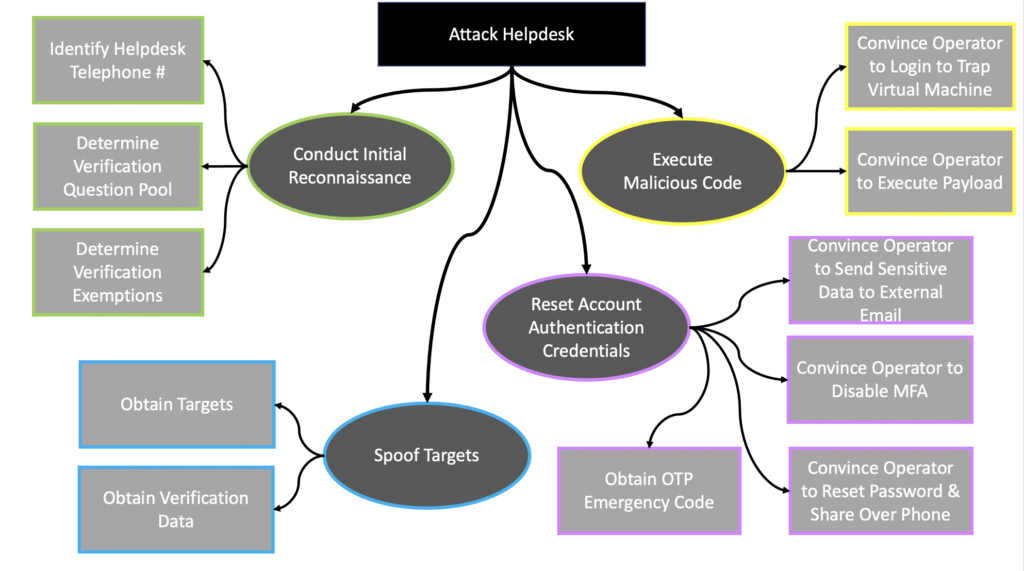
Introduction As we have witnessed in recent weeks with the MGM and Caesars Entertainment breaches, helpdesks are prime attack surfaces that are seeing a surge in exploitation. Although much of the press surrounding these most recent events alludes to helpdesk operators’ roles in the exploits, this type of vulnerability actually is a technology and process […]
Content Discovery: Understanding Your Web Attack Surface
Attack Surface Management (ASM) tools find quite a lot of vulnerabilities on the Web. This really isn’t surprising, given that HTTP/S is by far the most common and broadest of all the services comprising the Internet. In fact, Web-based issues represent the majority of the findings about which our Managed Service Providers (MSPs) inform our […]
ASM: The Best Defense is a Good Offense
About 10 years ago, security was relatively simple because everything occurred on premises. Change releases were tightly controlled by a change ticket and review process. In contrast, current networks consist of auto-scaling containers that run in Kubernetes clusters and even serverless clusters like AWS Lambda. We have transitioned from constrained environments that humans closely scrutinized […]