fwd:cloudsec 2023: Top Four Themes in Cloud Security for 2023

At Praetorian, we pride ourselves on our extensive expertise in cloud security and our commitment to staying at the forefront of the ever-evolving landscape. We consequently were excited to attend the highly anticipated fwd:cloudsec 2023 conference held on June 12–13, in Anaheim, CA. This non-profit conference brings together cloud security professionals, researchers, and practitioners from […]
ASM: The Best Defense is a Good Offense
About 10 years ago, security was relatively simple because everything occurred on premises. Change releases were tightly controlled by a change ticket and review process. In contrast, current networks consist of auto-scaling containers that run in Kubernetes clusters and even serverless clusters like AWS Lambda. We have transitioned from constrained environments that humans closely scrutinized […]
NIST CSF 2.0 Workshop Themes: Praetorian’s View
On 17 August 2022, NIST conducted the first Workshop to organize the effort to update the NIST Cybersecurity Framework (CSF) to version 2.0. Praetorian originally submitted comments to the CSF 2.0 RFI in February 2022. This Workshop provided a forum for NIST to frame the discussion around the major topics that emerged from the RFI. […]
Part 3 – Trends in the Cybersecurity Talent Marketplace in the Face of Sustained Shortages
I’ve written previously about how I believe a team’s expertise and talent are the most important factors in determining the success of a cybersecurity program. I’d like to elaborate a bit more on how I think that is affecting the marketplace for cybersecurity expertise and what it means for people operations. To summarize my previous […]
AWS Security Trends of 2022: Five Themes and Why They Matter

Building securely in the cloud can feel daunting given the sheer volume of ever-changing information to review, assess, and deconflict for your business needs. For example, AWS releases countless updates, new features, and new security services around its summer security conference, re:Inforce. Praetorian analyzed all the information pertaining to AWS’s new releases and security related […]
Part 2 – Adapting Security Strategy to the Rise of Opportunistic Attacks
Over the past two years, we’ve seen a number of our clients’ security programs re-orient to prepare for potential ransomware incidents. Much of these preparations have focused on the controls and processes that would specifically help prevent and respond to a ransomware infection. While this is often effort well-spent, I’d like to suggest that many […]
Multi-Step Attack Vectors: When Vulnerabilities Form an Attack Chain
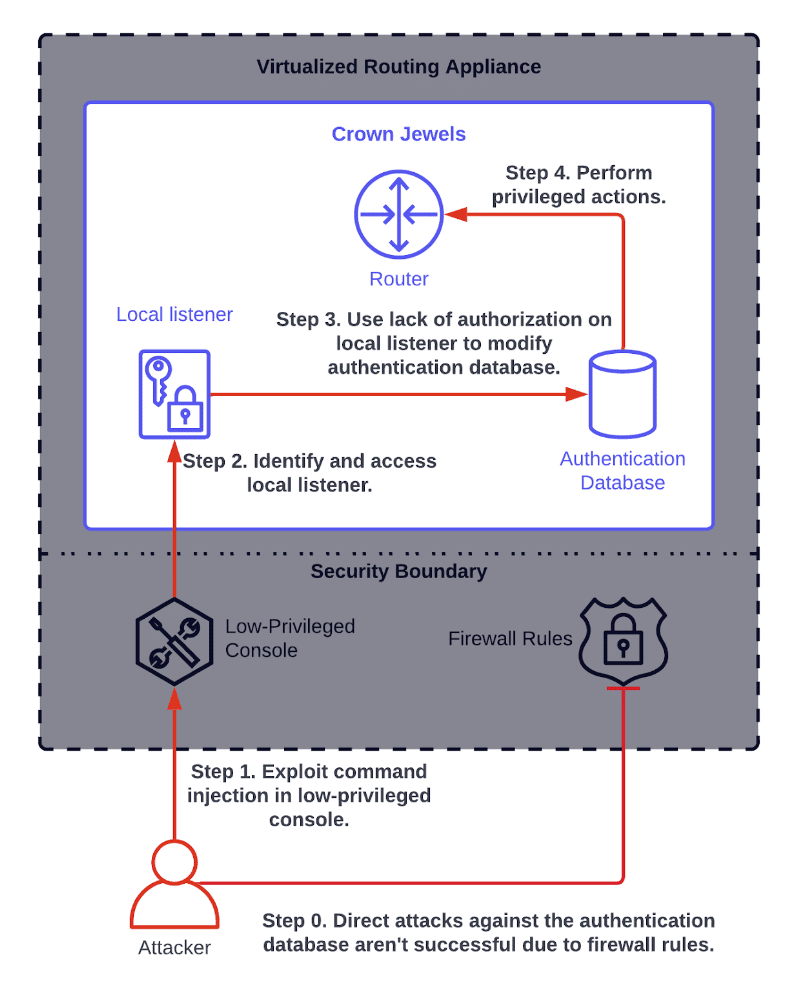
Praetorian’s approach to cybersecurity centers around a core belief that combining innovative technologies and the best people in the business leads to real results. In our experience, neither can fully solve cybersecurity challenges on its own. We therefore have designed our services organization and offerings to blend them seamlessly. We applied the same philosophy when […]
Part I – CyberSecurity is Adversarial, and What that Means for Security Strategy
I have an impression that in the course of the day to day grind, many security leaders have lost sight of a core tenant of cybersecurity: that it is adversarial. Ultimately, the core of most cybersecurity risks is defenders trying to stop attackers. Both sides are seeking to outwit each other. This contest is mediated […]
The Click Heard Around the World

On April 19, 1775, the American Revolutionary War began at Middlesex County in the Province of Massachusetts Bay. While it’s actually hard to define a specific “first shot”, Ralph Waldo Emerson immortalized his view of the event in the “Concord Hymn” which begins with the following familiar stanza: By the rude bridge that arched the […]
North Korean Lazarus APT phishing defense contractors

A new cyber attack campaign launched by North Korean APT Lazarus Group is targeting the military defense industry. Lazarus weaponized two documents related to job opportunities from Lockheed Martin in the spear phishing attack. The discovery was made January 18, 2022. Here’s what you need to know: What might the hackers be looking for? North […]