Why Praetorian Benchmarks to MITRE ATT&CK™ and Why You Should Too

When it came to improving our Purple Team service line, which maps to “Detect” and “Respond” in the NIST CSF, we wanted to provide a similar high quality of data and metrics to our clients. In our experience, it is hard to drive change in any organization unless those changes can be tied to measurable results. After conducting a survey of known frameworks, we settled on the ATT&CK™ framework from MITRE.
Safely Conduct Security Assessments of Industrial Control System (ICS) Environments

Our current standard of living is made possible due to the massive scale of critical infrastructure that supports our needs as a society. Electricity, Oil, Gas, Water, and Security are a few of the well-known industries whose infrastructure is managed by Industrial Control Systems (ICS). Few systems have the potential for catastrophic consequences from a security incident as is possible with an ICS breach.
Benchmarking Enterprise Cybersecurity Programs with NIST CSF
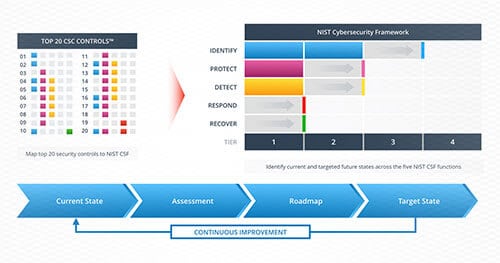
Benchmarking enterprise cybersecurity programs with NIST Cybersecurity Framework (CSF) helps organizations strengthen their security posture.
Summary of April MITRE ATT&CK RELEASE

MITRE’s Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK™) is a curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary’s lifecycle and the platforms they are known to target. ATT&CK is useful for understanding security risk against known adversary behavior, for planning security improvements, and verifying defenses work as expected.
KRACK (Key Installation Attack) Against Wi-Fi Networks
A flaw in the implementation of WPA2-based encryption allows for an attacker within physical range of the wireless network to decrypt traffic from a vulnerable client, allowing for viewing, intercepting, and modifying data in transit. This vulnerability has been assigned CVE numbers CVE-2017-13077 through CVE-2017-13088. There does not yet exist a working public exploit for this attack. However, the research group who discovered it have published their efforts, and working exploit code is likely a matter of days away.
Shadow Brokers After Action Report
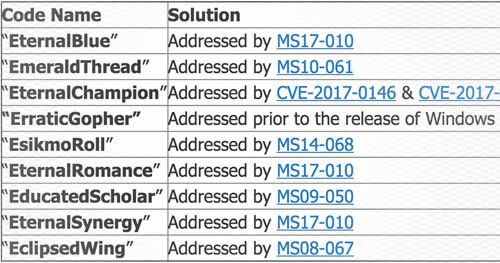
Microsoft released security updates in March that address many of the issues already. Therefore, there are no 0day vulnerabilities included in the toolset that can be used against fully patched versions of Windows. The toolset was built in 2013 which means it doesn’t include Windows 10 and 2016. Legacy versions of Windows are still vulnerable since Microsoft won’t release security updates for them.
Hashjacking: Anyone Can Steal Your Windows Password

There is currently an architectural vulnerability within the Windows SMB authentication protocol that affects modern Windows Operating System. The core of this issue is due to the presumptive nature of current SMB authentication methods. When a user accesses a file share or remote file (by typing “file://” or “” in a browser or file explorer) hashed Windows credentials from the current user are automatically sent to the remote server in attempt to authenticate and access the remote file. The default behavior of assuming the remote server is trusted allows for systems to quickly access file shares in large corporations so that users won’t need to sign in with their company credentials each time to access network resources. However, this implementation presents a significant security risk to user accounts and passwords.
Well-tested Authorization Design Patterns

Authorization is a strange beast. In theory, it appears to be rather straight-forward: a user should not be able to create, read, update, or delete data that it does not have access to. However, from our experience, theory tends to deviate from practice. Missing or incorrect access controls are a dime a dozen for applications we test and this very rarely stems from a complete lack of access controls. More often then not, authorization issues spring up during assessments where the application manages a complex authorization model and an incorrect assumption was made or an edge case was missed. Conversely, we have seen applications that have incredibly complicated authorization models that have zero access control problems.
An Opinionated Series on Why Signal Protocol is Well-Designed: Deniability
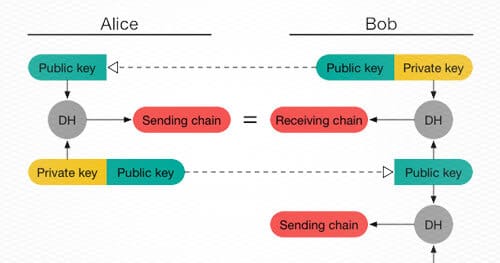
In my previous blog post covering WhatsApp end-to-end encryption, I spoke about Signal Protocol and how certain design decisions allowed Signal Protocol to be efficient on mobile devices. For this blog post, I’ll cover deniable authentication, how it has worked in the Off-The-Record (OTR) Messaging protocol, and how Signal Protocol has approached this problem. Deniable authentication tries to digitally recreate “off-the-record” conversations in the physical realm. If you tell Bob an embarrassing story in-person and Bob proceeds to tell Mallory about that story, it is possible for you to claim that Bob made the story up. Conversely, if you were to “sign” every statement you have ever made to Bob it would be practically impossible to deny that you told that story to Bob.
Email Filters: A Reliable Phishing Protection?
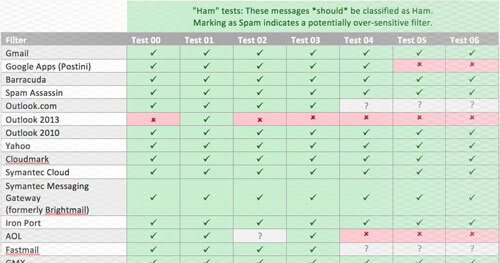
It’s no secret that spear phishing is a prevalent threat and is making an appearance in many CISOs' nightmares. The Verizon’s 2016 breach digest is out and—for anyone who hasn’t looked through it yet—the answer is 30%. That’s the percentage of breaches from 2013 to 2016 that leveraged social engineering tactics to stage a compromise. Of those attacks, phishing accounts for 72% of them. That means that nearly 22% of breaches in the last 3 years have leveraged phishing in some way or another. It's hard enough to secure external and internal assets… but having to secure your employees too? It’s a scary thought. Definitely something to keep one up at night. Current solutions include improving user awareness through training exercises, minimizing and controlling damage through defined incident response programs, and stopping phishing emails before they ever make it to employees' inboxes through email/spam filtering solutions. We're here to talk about the last one. Using a collection of benign and phishy emails alongside a spam filter testing service called Email on Acid, we've taken a stab at comparing 22 different spam filtering solutions. These tests measure each spam filter's ability to stop spear-phishing emails in their tracks. To anyone afraid of long articles, the “tl;dr” reads something like this: Spam filters are okay. They’re not perfect and not terribly intelligent, but they can be effective at times and represent one layer of defense that should be in-place to protect an organization from phishing or spear-phishing attacks.