CRITICAL: Bash “Shellshock” Vulnerability
On September 24, 2014, a vulnerability in Bash—now referred to as the ‘Shellshock’ bug—was publicly announced after its discovery last week by Stephane Chazelas. Security experts expect the Shellshock bug to have significant and widespread impact, potentially more devastating than Heartbleed.
Why You Should Add Joern to Your Source Code Audit Toolkit
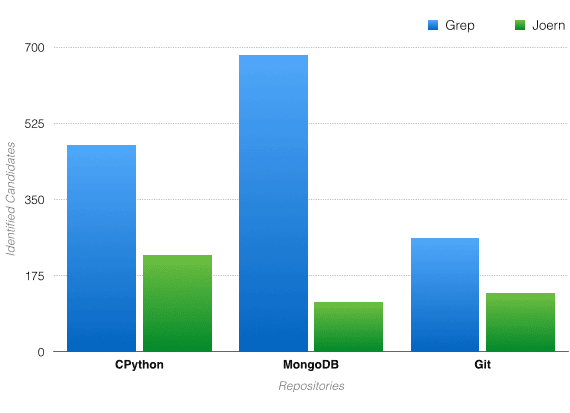
Joern is a static analysis tool for C / C++ code. It builds a graph that models syntax. The graphs are built out using Joern’s fuzzy parser. The fuzzy parser allows for Joern to parse code that is not necessarily in a working state (i.e., does not have to compile). Joern builds this graph with multiple useful properties that allow users to define meaningful traversals. These traversals can be used to identify potentially vulnerable code with a low false-positive rate.
CRITICAL: New Internet Explorer Zero-day Vulnerability
Only a few weeks after Heartbleed hit the Internet by storm, reports of another serious zero-day vulnerability are starting to circulate within the security community. Over the weekend Microsoft released Security Advisory 2963983, which details a new remote code execution vulnerability impacting ALL versions of Internet Explorer (IE6-IE11). Microsoft is aware of “limited, targeted attacks that attempt to exploit the vulnerability.” The company is currently investigating public reports of the vulnerability and it has yet to publicize details to the reserved CVE-2014-1776, but there are steps organizations can take to protect against this threat.
CRITICAL: HeartBleed Vulnerability
There is a new critical vulnerability affecting a widely used version of OpenSSL called HeartBleed (CVE-2014-0160). This new bug allows an attacker to read system memory remotely, without authentication. It has been reported that 60-70% of the Internet is affected. Immediate action should be taken to identify vulnerable systems within your environment and take necessary steps to mitigate risk associated with this critical vulnerability.
Whats up with WhatsApp’s Security?

Facebook’s acquisition announcement coincided with the starting week of Project Neptune’s beta program. Project Neptune is Praetorian’s new mobile application security testing platform that allows companies to keep pace with rapid mobile development cycles by incorporating continuous, on-demand security testing. And what’s a better way to properly kick off our beta program than to test a publicly available mobile app worth $19 billion? Within minutes, Project Neptune picked up on several SSL-related security issues affecting the confidentiality of WhatsApp user data that passes in transit to back-end servers. This is the kind of stuff the NSA would love. It basically allows them—or an attacker—to man-in-the-middle the connection and then downgrade the encryption so they can break it and sniff the traffic. These security issues put WhatsApp user information and communications at risk.
Advanced Threats: Driving Senior Leadership Awareness
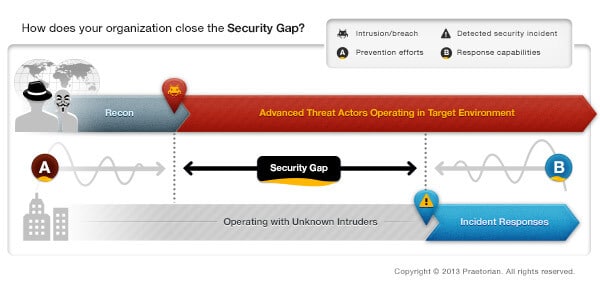
In today’s changing security environment, where advanced persistent threats (APT) are playing such a dramatic and notable role, it is the security organization’s responsibility to ensure that senior leadership understands and accepts risk associated with modern-day advanced threat actors. Regardless of your security maturity levels, you should at least be having the conversation about Advanced Threats. It is incumbent upon security leaders to drive this conversation within your organization in an effort to shift expectations away from thinking…
The Honeynet Project Maps Real-Time Attacks From Around the World
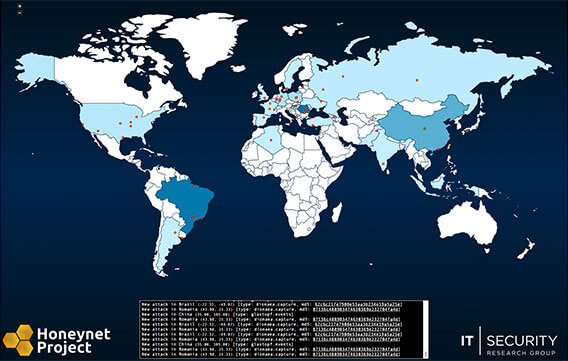
Members of The Honeynet Project’s Giraffe Chapter released a new real-time attack map earlier today. The map shows live attacks from locations around the world, provided by distributed honeypots operated by Honeynet Project chapters. Currently the map is in an alpha release stage, and additional data and input sources are planned for future releases. [Update 9/25/2012: Additional data feeds have been added]
Effectively Measuring Risk Associated with Vulnerabilities in Web Applications
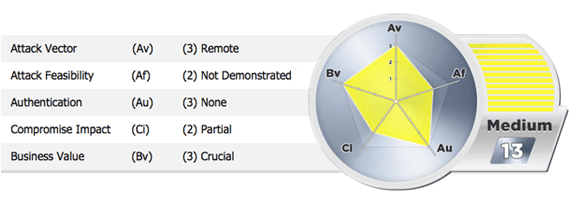
An objective risk rating framework enables our team to compare a standardized measurement of risk across an organization. It also allows our clients to prioritize steps needed in an action plan to mitigate, accept, or transfer organizational risk. Prioritization of vulnerability remediation should be organized objectively based on factors used in the risk rating framework, such as: ease of exploitation, severity of impact if exploited, and level of effort to remedy. If you are considering adopting a risk-rating framework, it is important to tailor a solution that best suits your organizational needs. The following risk rating scale was developed to satisfy the specific needs of our clients, and we hope it provides you with valuable guidance as you plan for the management of risk within your organization…