Azure RBAC Privilege Escalations: Azure VM

Microsoft Azure provides administrators with controls to limit the actions a principal can take within the cloud environment. These actions can broadly be split into two categories: those that impact the Entra ID tenant and those that affect the Azure cloud subscription, the latter of which we will call “RBAC actions.” Prior research into Entra […]
Leveraging Microsoft Text Services Framework (TSF) for Red Team Operations
The Praetorian Labs team was tasked with identifying novel and previously undocumented persistence mechanisms for use in red team engagements. Our primary focus was on persistence techniques achievable through modifications in HKCU, allowing for stealthy, user-level persistence without requiring administrative privileges. Unfortunately, while we identified an interesting persistence technique, the method we discuss in this […]
Introducing Nosey Parker Explorer

Introducing Nosey Parker Explorer: an interactive review tool for findings from Nosey Parker – the machine learning powered, multi-phase solution for locating secret exposure.
ETW Threat Intelligence and Hardware Breakpoints
Learn to bypass EDR detection using NtContinue for hardware breakpoints without triggering ETW Threat Intelligence. This technical blog explores kernel debugging, debug registers, and EDR evasion with code examples.
Tarbomb Denial of Service via Path Traversal

Praetorian recently uncovered a denial-of-service vulnerability by chaining together path traversal and legacy file upload features in a CI/CD web application; highlighting the risks of undocumented features and the importance of input validation in web security.
Why Azure B2C ROPC Custom Flows Are Inherently Insecure

Microsoft’s Azure Active Directory B2C service allows cloud administrators to define custom policies, which orchestrates trust between principals using standard authentication protocols. One such custom policy that B2C defines by default is the Resource Owner Password Credentials (ROPC) flow, which implements the OAuth standard authentication flow of the same name and allows users to simply […]
Helpdesk Telephone Attack: How to Close Process and Technology Gaps
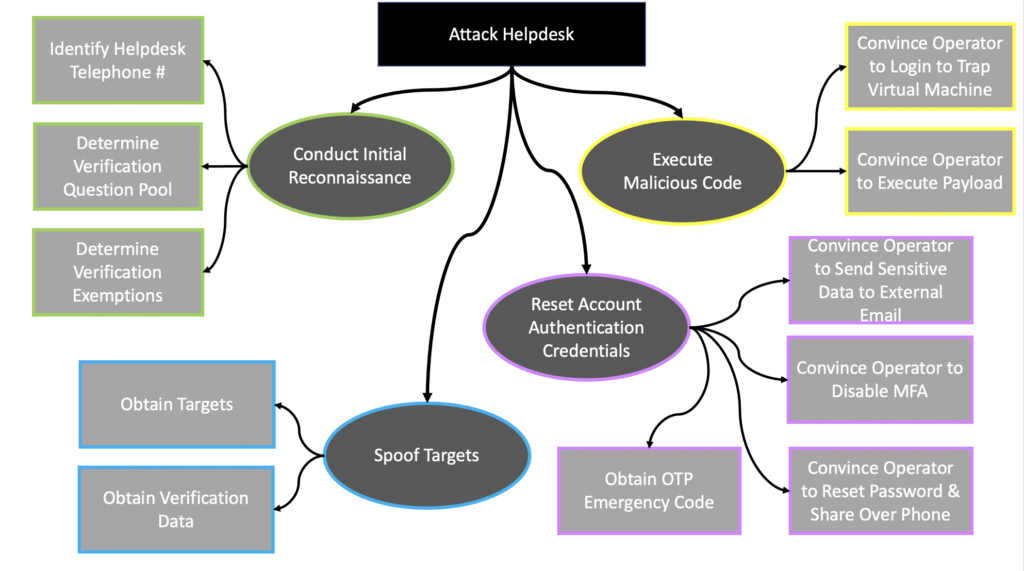
Introduction As we have witnessed in recent weeks with the MGM and Caesars Entertainment breaches, helpdesks are prime attack surfaces that are seeing a surge in exploitation. Although much of the press surrounding these most recent events alludes to helpdesk operators’ roles in the exploits, this type of vulnerability actually is a technology and process […]
Announcing Nosey Parker Update to v0.14.0

Last week we published a new release of Nosey Parker, our fast and low-noise secrets detector. The v0.14.0 release adds significant features that make it easier for a human to review findings, and a number of smaller features and changes that improve signal-to-noise. The full release notes are available here. Release highlights File names and […]
Konstellation: A Tool for RBACpacking in Kubernetes
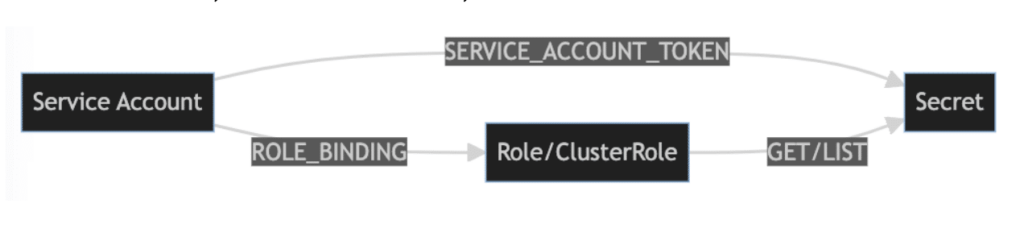
The author presented this paper and corresponding tool at Black Hat: Arsenal 2023 on August 10, 2023. For a more general overview of Konstellation and its capabilities vis a vis Kubernetes RBAC, please see our earlier companion post. Kubernetes Role-Based Access Control (RBAC) is a mechanism for controlling access to resources in a Kubernetes cluster. […]
Introducing Konstellation, for Kubernetes RBAC Analysis
Praetorian is excited to announce the upcoming release of Konstellation, a new open-source tool that simplifies Kubernetes role-based access control (RBAC) data collection and security analysis. Join us August 10, 2023, at Black Hat Arsenal 2023 for a deeper dive on exactly what this tool can do for you. Kubernetes RBAC is a powerful tool […]