Hob0Rules Released: Statistics Based Password Cracking Rules
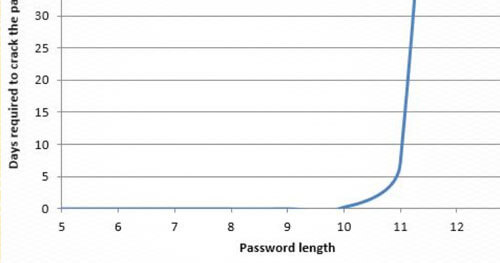
It’s now 2016 and people are still decisively using poor, predictable passwords. Employees around the world will soon be appeasing their mandatory 90-day password rotation by changing their password from ‘Winter2015’ to ‘Spring2016’. This happens in nearly every company – you would be surprised. Previously, I conducted password research to determine common traits of passwords, which was presented at various conferences. The password cracking rules that Praetorian utilizes for all hash cracking have now been released for Hashcat (described below) which are based on these findings. A quick compromise list of 64 of these rules have been released as hob064 and a more extensive ruleset has been released as d3adhob0 for public use. These rulesets were made to compete against their industry standard counterparts, Best64 and d3ad0ne. Both of the released rulesets have bypassed their counterpart in both time speed and number of hashes cracked and will continue to improve. The two sets of rules are living lists and change as the environment of passwords changes.
Ruby Unsafe Reflection Vulnerabilities
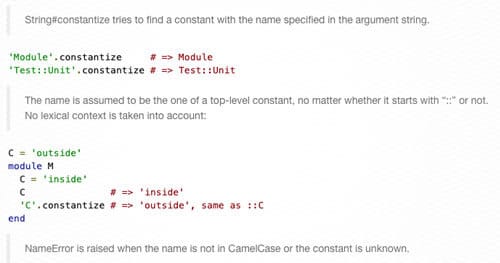
One of the interesting properties of Ruby is the fact that everything is an object. The manipulation of objects at runtime is what makes Ruby so flexible and interesting as a language. At its heart, this is the idea behind reflection. Reflection is a tool to allow a program to examine and modify its own behavior at runtime, granting programmers the ability to simpilify certain constructs (e.g. framework development, dependency resolution).
Gladius: Automatic Responder Cracking
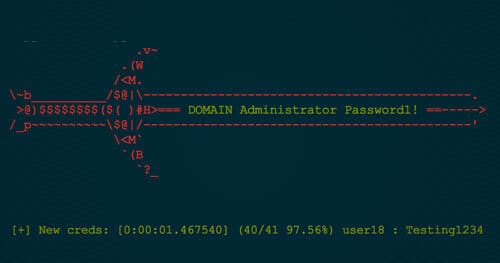
So there you are, performing your internal penetration test, using Responder to potentially grab hashed credentials and thinking "Responder is awesome… but manually cracking credentials isn’t fun." Well, welcome Gladius! Gladius happily listens for Responder hashes (and.. spoiler alert.. secretsdump.py and hashdump) and automatically passes them to hash cat. At its core, Gladius listens in target directories for file events and then performs computations based on the event. Let’s walk through the Responder workflow with Gladius.
Introducing MitM-VM & Trudy: A Dead Simple TCP Intercepting Proxy Tool Set
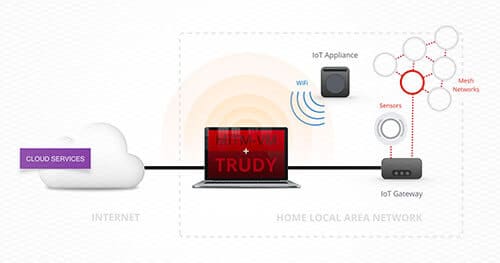
Positioning yourself as a man-in-the-middle (MitM) is a powerful situation to leverage during a security assessment. Unfortunately, in some situations, leveraging an active MitM position is difficult. There are existing proxies that try to alleviate these issues but they all seem to suffer from a flaw that makes using the tool undesirable. MitM-VM and Trudy are a complimentary set of tools that are designed to address several issues with existing proxies. Together they enable easy-to-setup and powerful man-in-the-middle positions. Why build these tools? Modifying custom binary protocols on the fly while sitting between an embedded device and a server is usually a slow process that involves sniffing legitimate traffic and then rebuilding packets programmatically. Trudy makes this process easy by enabling Burp-like features for generalized TCP traffic.
The Reason My Lamp is Insecure

I suffer the struggle many others do. It’s a systemic issue that’s not really talked about much. The issue I’m talking about is the inconvenience of turning my lamp off and then proceeding to stumble around in the dark to get to my bed. I set out to solve this problem by automating my lamp with a Raspberry Pi, a relay, and a simple web application. Those who have worked with electronics before know this setup is not very technically challenging, but I wasn’t going for anything too fancy. My goal was to create a simple web application that could turn my lights on and off, which can be seen in the code below. This code also includes an alarm clock which operates by flashing my lights every morning at a preset time.
Getting Started with Damn Vulnerable Router Firmware (DVRF) v0.1
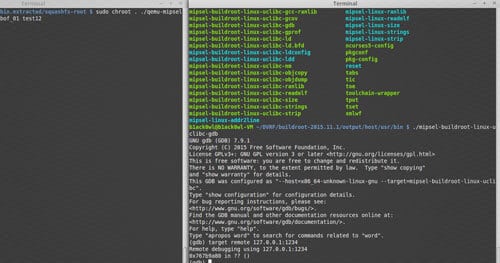
The goal of the DVRF project is to simulate a real-world environment to help people learn about other CPU architectures outside of the x86_64 space. The project will also help people get into discovering new things about hardware. As of now this DVRF firmware is tailored for the Linksys E1550 Device. If you do not have one don’t worry! Ready to get a jump start on learning aspects of embedded device hacking for exploit development? If so, this project is for you.
Group Policy Preferences (GPP) Pwned
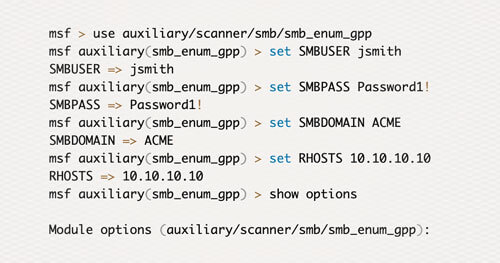
Over the past few months I’ve had a chance to clean up some code that we’ve used internally for penetration testing for some time now. This code was built to demonstrate the weaknesses of using Group Policy Preferences (GPP) to store and distribute local or domain credentials. We have found that many organizations store local admin, domain service, and even Domain Admin account credentials using GPP. The module that I submitted to the Metasploit Github repo provides the ability to enumerate GPP credentials as a domain user with access to the SMB share on the DC. Extracted credentials will be stored in the Metasploit creds tables.
Building the HashCat API in Ruby to Crack Passwords in the Cloud
Have you ever had an amazing idea for automating two or more pieces of technology and then realized one of them doesn’t have an API? I came across this problem more than once during the development of a couple of projects here at Praetorian. In this post, I’ll share some of the libraries and techniques I have used to build out APIs for CLI programs, such as HashCat and nmap. Hopefully, these techniques and libraries will be helpful to you when building out new web applications and frameworks.
Using Developer Debugging Tools to Pentest Mobile Applications
During a recent assessment, I was pentesting a hybrid mobile application that is a companion to a web application. The applications allow users to collaborate while creating new interactive digital content. Through the web interface, content creators are allowed to upload a wide range of files, including HTML files, and share the content with other individuals in their organization. Thus, any user with proper permissions is able to view and edit shared content.
Man-in-the-Middle TLS Protocol Downgrade Attack
A flaw was recently found in OpenSSL that allowed for an attacker to negotiate a lower version of TLS between the client and server (CVE-2014-3511). While this vulnerability was quickly patched, an attacker that has control of your traffic can still simulate this attack today. Let’s explore how this is possible through looking at man-in-the-middle attacks and how browsers handle SSL/TLS connections. In addition, we will see the implications of the attack on cryptographic security.