Metasploit Integration for Password Auditor
Last week I introduced our new Password Auditor, an internal project I’m working on here at Praetorian. Today, I’m back with a followup screencast that demonstrates one of its major features — Metasploit integration! If you missed the previous screencast, I recommend watching it to get a sense of the tool’s basic functionality.
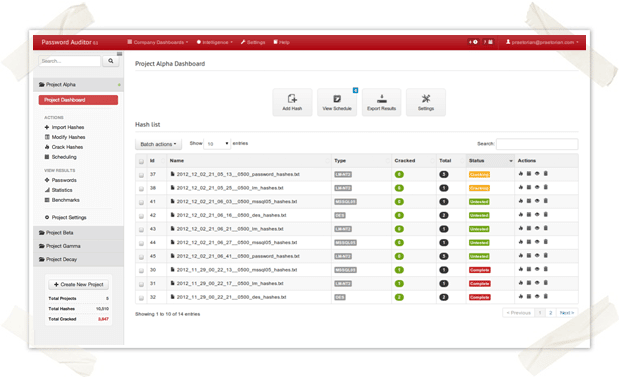
Password Auditing with Style
In my last post, I announced that our team has been developing an easy-to-use password cracking tool with advanced features. Our initial goal for the project was to create something that made password auditing easier for our services team. However, after several internal discussions we’ve decided to share our work with the security community in order to see if this tool has value beyond what we had initially envisioned. We’ve even talked about opening up a private, invite-only Beta to let others get some hands-on time with the tool. I encourage you to learn more about the tool and leave feedback/comments below (it may increase your chances of receiving an early invitation).
Easy to Use Password Cracking Tool with Advanced Features
Looking back over this past year, I have noticed a continuing theme among public security breaches. Similar to 2011, this year’s high profile security breaches often end in a public dump of confidential victim data. It is not uncommon for Hacktivist groups, such as Anonymous, to publically dump password hashes and other confidential data as a way of proving the breach occurred and as a way of embarrassing the victim.
Burp SQLmap plugin for Windows
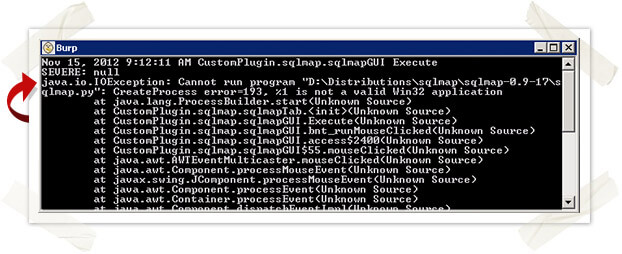
Burp Suite provides a very basic SDK known as Burp Extender. Burp Extender allows third parties to extend the features of an already powerful web application testing suite. In March of this year, Daniel Garcia (cr0hn) created a SQLmap plugin for Burp using the Burp Extender SDK. With Daniel’s SQLmap plugin, automated SQL injection discovery and exploitation is now seamless between two of our favorite web application pentesting tools.
Multi-Core and Distributed Programming in Python
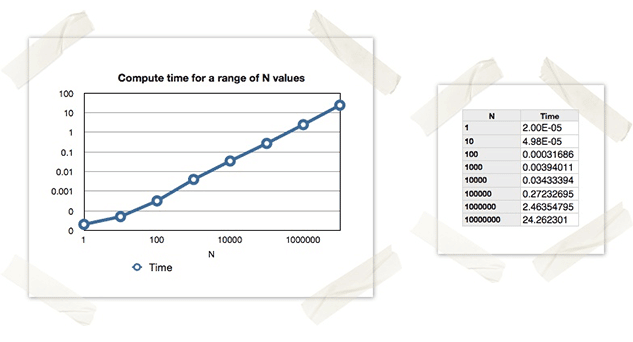
In the age of big data we often find ourselves facing CPU-intensive data processing tasks, therefore it is useful to understand how to harness all available CPU power to tackle a particular problem. Recently we came across a Python script which was CPU-intensive, but when the analyst viewed their overall CPU usage it was only showing ~25% utilization. This was because the script was only running in a single process, and therefore only fully utilizing a single core. For those of us with a few notches on our belts, this should seem fairly obvious, but I think it is a good exercise and teaching example to talk about the different methods of multi-core/multi-node programming in Python. This isn’t meant to be an all-encompassing tutorial on multi-core and distributed programming, but it should provide an overview of the available approaches in Python.
HTTP/HTTPS Bruteforcing Using a List of IPs and Hostnames with Metasploit
Today, I wrote some automation to make it easier to setup and perform HTTP bruteforcing using a list of IPs and hostnames with Metasploit. Metasploit has several auxiliary modules that make it easy to perform various types of bruteforce based attacks. For example, we can easy bruteforce all HTTP BASIC AUTH systems by using the http_login module.