Announcing Gato Version 1.5!

On January 21, 2023 at ShmooCon 2023, Praetorian open-sourced Gato (Github Attack Toolkit), a first of its kind tool that focuses on abusing offensive TTPs targeting self-hosted GitHub Actions Runners. Since then, Praetorian and other offensive security practitioners across the information security community have leveraged Gato for so much more than just self-hosted runner attacks. […]
Improving Performance and Scalability: Updates and Lessons from Inspector, Our End-to-End Testing Solution
Overview In a previous article titled Inspector or: How I Learned to Stop Worrying and Love Testing in Prod, we discussed our end-to-end testing solution, Inspector, which we leverage to perform continuous testing of our external attack surface enumeration scanning system. Here, we discuss some of the recent modifications and updates we made to Inspector […]
Content Discovery: Understanding Your Web Attack Surface
Attack Surface Management (ASM) tools find quite a lot of vulnerabilities on the Web. This really isn’t surprising, given that HTTP/S is by far the most common and broadest of all the services comprising the Internet. In fact, Web-based issues represent the majority of the findings about which our Managed Service Providers (MSPs) inform our […]
In Brief: Chariot Alignment with FDA Section 524B.1

Chariot is more than a product; it’s a partnership that combines automated monitoring and human analysis to identify externally-accessible security risks. In light of the FDA’s latest requirements for in-market device security (summarized in Section 524B), Praetorian’s customers are having success leveraging the Chariot Managed Service as a cost-effective and scalable approach to satisfying Section […]
Cyber Cartography: Mapping a Target
As Phil Venables has said, “at some level, cyber defense is a battle over whether the attacker or defender has better visibility of the target. Action is key, yes, but without good ‘cyber cartography’ it can be hard to act in the right way.” An attacker’s first step is enumeration, or identifying what looks hackable. […]
Find More Secrets with Nosey Parker v.0.12.0

On March 2, 2023, we issued some updates to our secrets sniffing tool, Nosey Parker, which has been available as an Apache 2-licensed open-source project since December 2022. We originally developed the full version to embed in Chariot, our Attack Surface Management solution, because we needed a secrets detection tool that was as fast as […]
Open Source Tools: From Our Lab to Your Fingertips
One of the core decisions we’ve made at Praetorian is to maximize efficiency and effectiveness. In pursuit of this, we carefully select and implement automation and technical solutions for tasks that don’t need human attention. The key is choosing thoughtfully developed tech and tools; when we can’t find what we need, we create it ourselves! […]
Phantom of the Pipeline: Abusing Self-Hosted CI/CD Runners

Introduction Throughout numerous Red Teams in 2022, a common theme of Source Control Supply Chain attacks in GitHub repositories has emerged. After many hours manually hunting for and exploiting these attack paths, we’ve built an all-in-one toolkit called Gato (Github Attack Toolkit) for finding and attacking repositories where these misconfigurations are present. We released the […]
Nosey Parker RegEx: A Positive Community Response

On December 7, 2022, Praetorian Labs released a regular expression-based (RegEx) version of our Nosey Parker secrets scanning tool (see press release). This version improves on two primary pain points the community has historically encountered with other secrets scanning tools. First, Nosey Parker RegEx offers the fastest secrets scanning capability on the market–100 gigabytes of […]
Instrumenting an Automotive Module for Bench Testing
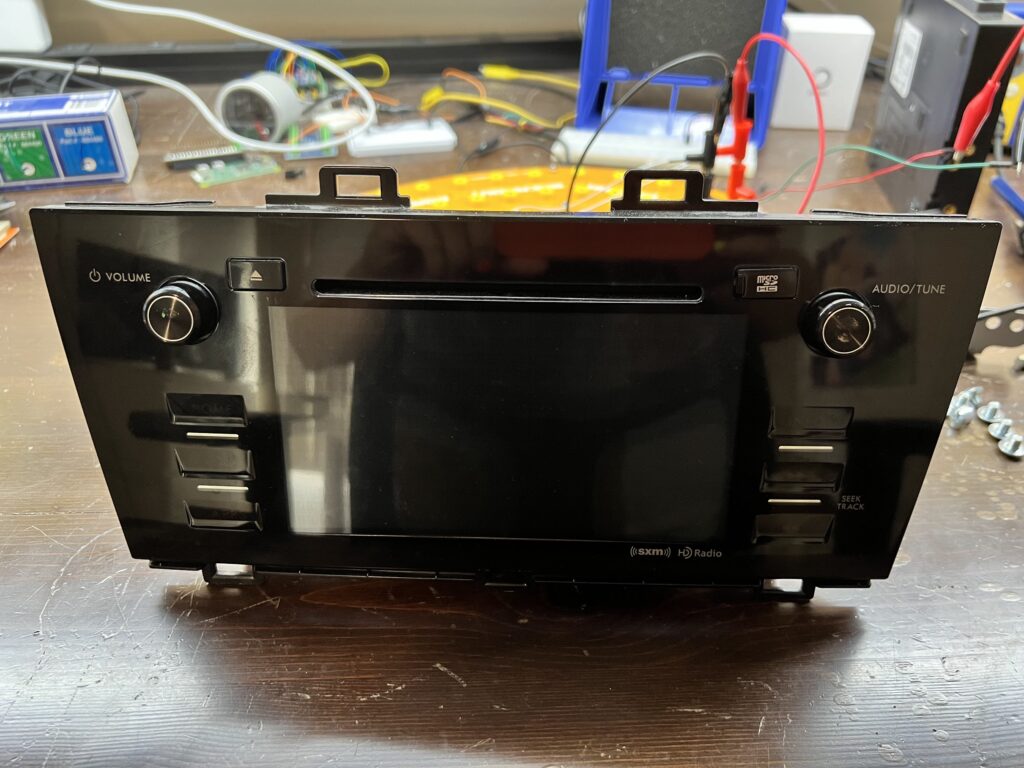
Finding vulnerabilities, hacks, exploits, and full root access are goals for security engineers when they begin to assess a device, right? But when working with hardware, you cannot simply dive into the hacking on day one. Your exploits will only be as successful as the setup work you’ve done! This post will discuss the process […]