Automating the Discovery of NTLM Authentication Endpoints
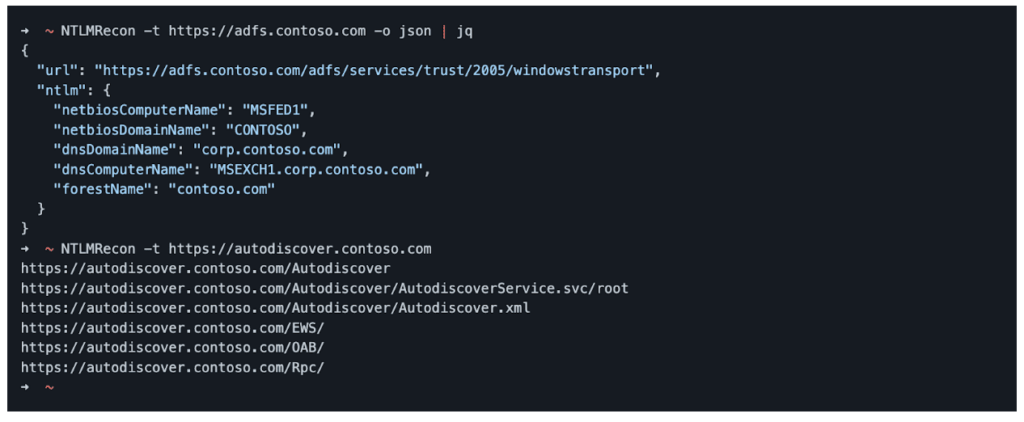
Recently, I have been working on adding support for automated enumeration and discovery of NTLM authentication endpoints to Chariot, our external attack surface and continuous automated red teaming product. Our red team requested this feature as a way to identify NTLM authentication endpoints exposed over HTTP that they could potentially leverage for password spraying attacks […]
Inspector, or: How I Learned to Stop Worrying and Love Testing in Prod
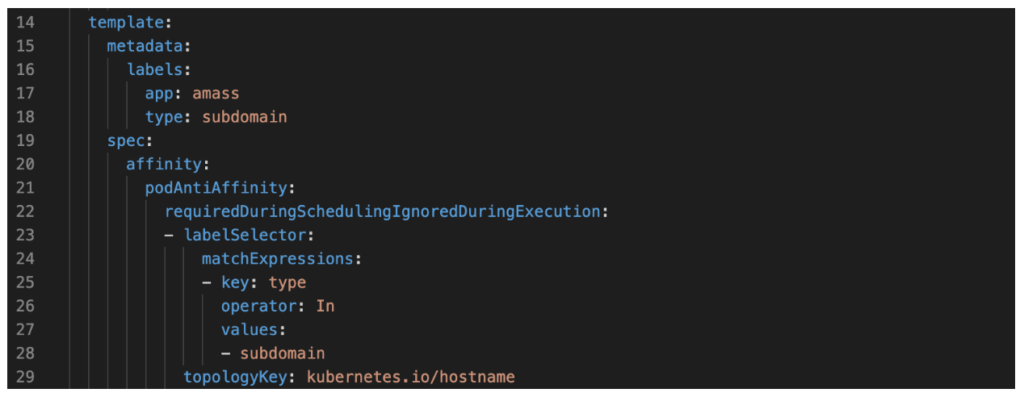
Overview Recently, I’ve shifted from primarily performing red team engagements to assisting in the development of Chariot, Praetorian’s attack surface management (ASM) and continuous automated red teaming (CART) product offering. Our Praetorian Labs team has developed multiple tools to support Chariot and our Services organization. One of these, a subsystem for the core asset enumeration […]
From Self-Hosted GitHub Runner to Self-Hosted Backdoor
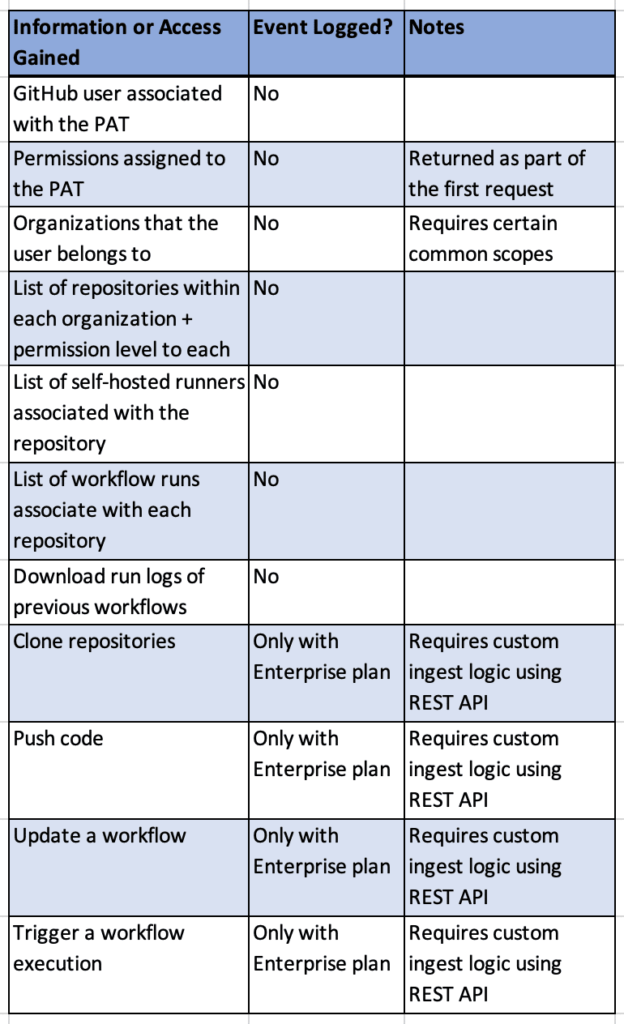
Overview Continuous Integration and Continuous Delivery (CI/CD) systems are powerful and configurable tools within modern environments. At Praetorian, we are seeing organizations migrate to SaaS solutions like GitHub (GitHub.com) as their source code management and CI/CD solution, instead of on-premises tools like BitBucket, Bamboo, and Jenkins. On our Red Team engagements , we routinely employ […]
Six Months of Finding Secrets with Nosey Parker
Earlier this year we announced Nosey Parker, a new scanner that uses machine learning techniques to detect hardcoded secrets in source code with few false positives. Since then we’ve continued its development and expanded its use in security engagements at Praetorian. In a few cases Nosey Parker has contributed to critical-severity findings, such as complete […]
Introducing FingerprintX: The fastest port fingerprint scanner

Introduction Port fingerprinting can detect specific services running on a network, which makes it useful during penetration tests. It expands visibility into potential attack surfaces and vulnerabilities within the network environment. Over the summer, our interns worked towards developing a new tool for port fingerprinting services: Fingerprintx Fingerprintx is a port fingerprinting utility tool useful […]
Safeguarding Memory in Higher-Level Programming Languages
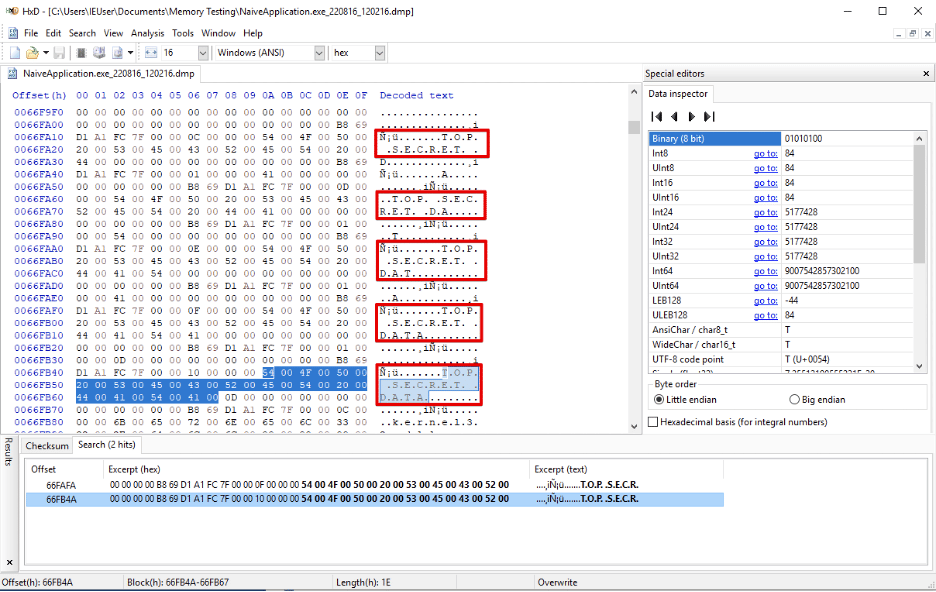
Consider an application written in a higher-level language like Python, NodeJS, or C#. This application must handle sensitive data such as banking credentials, credit card data, health information, or network passwords. The application developers have already hardened the application against malicious users and are confident that it is not vulnerable to database injections, account takeovers, […]
Whitebox Security Assessments: Doing More with More
When deciding on what type of security assessment to get, an organization should consider how much information they are willing to share. Several types of assessments exist, and the key differentiator is how much access an organization grants the testers from the beginning. The terms blackbox, greybox, and whitebox refer to whether a client chooses […]
NTLMv1 vs NTLMv2: Digging into an NTLM Downgrade Attack

Overview During the summer, my colleague Derya Yavuz and I published an article on some of the different methods we’ve leveraged to elevate privileges within Active Directory environments. We discussed authentication coercion techniques such as PrinterBug, PetitPotam, and DFSCoerce. One of the techniques we mentioned in that article was performing an NTLM downgrade attack to […]
Thinking Outside the Mailbox: Modernized Phishing Techniques
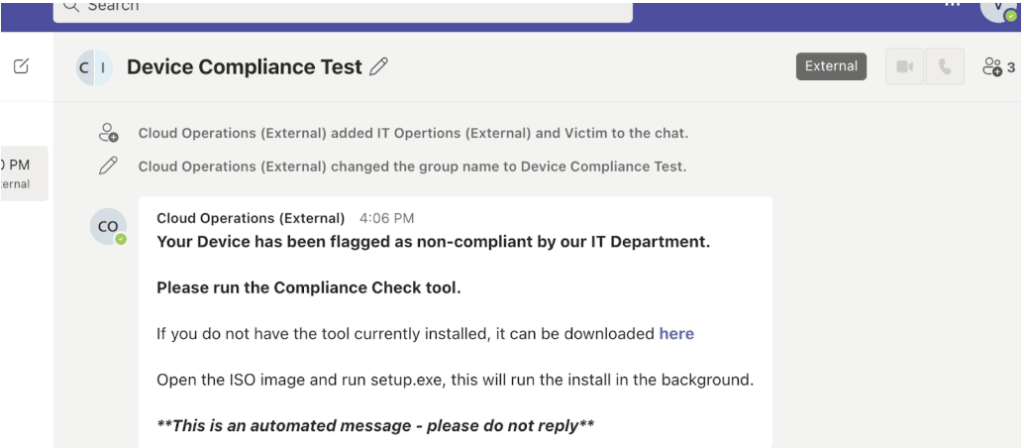
As defensive controls have advanced, so too have adversaries’ approaches to social engineering. Landing a phishing email in an inbox has become harder, and most campaigns that do make it to an inbox are quickly reported, quarantined, or triaged. So, adversaries have asked themselves why not skip the inbox all together or leverage a service […]
Elevating Privileges with Authentication Coercion Using DFSCoerce
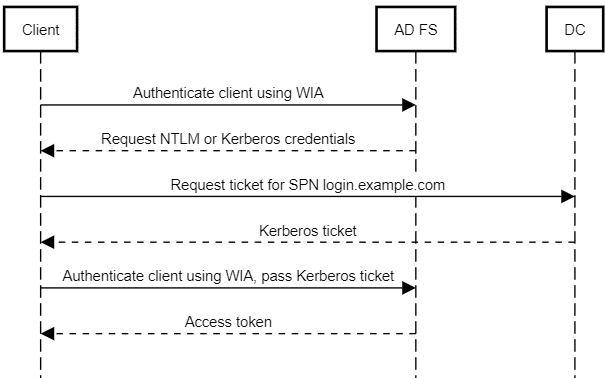
Background In our previous blog post, we talked about the recently-published DFSCoerce utility which is useful for forcing NTLM or Kerberos authentication by interacting with the Distributed File Service (DFS) over Remote Procedure Calls (RPC) on Windows. This forces the victim to authenticate into the attacker’s machine, very much like authentication coercion tools like PetitPotam […]