Relaying to ADFS Attacks
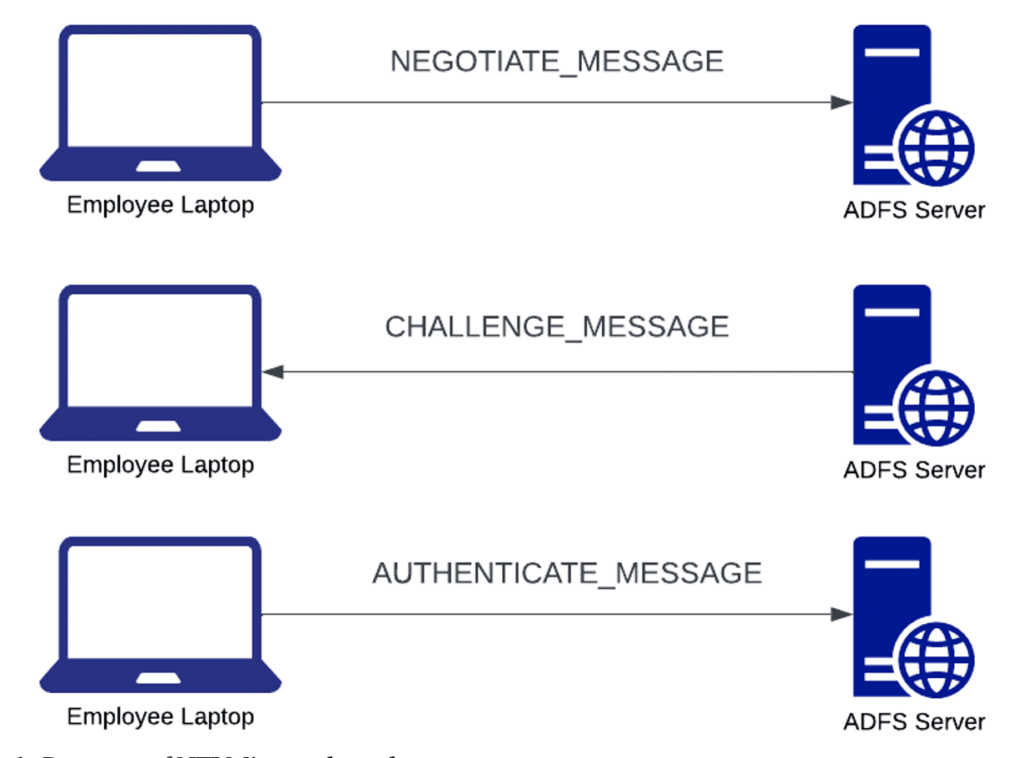
Overview During red team engagements over the last few years, I’ve been curious whether it would be possible to authenticate to cloud services such as Office365 via a relay from New Technology Lan Manager (NTLM) to Active Directory Federation Services (ADFS). If possible, this would unlock an entirely new attack surface for NTLM relaying attacks […]
Chaining MFA-Enabled IAM Users with IAM Roles for Potential Privilege Escalation in AWS

Overview In AWS, sts:AssumeRole is an action within AWS’s Security Token Service that allows existing IAM principals to access AWS resources to which they may not already have access. For example, Role A can assume Role B and then use Role B’s privileges to access AWS resources. Common use cases include assuming a role within […]
Computer Account Relaying Vulnerabilities Part 2
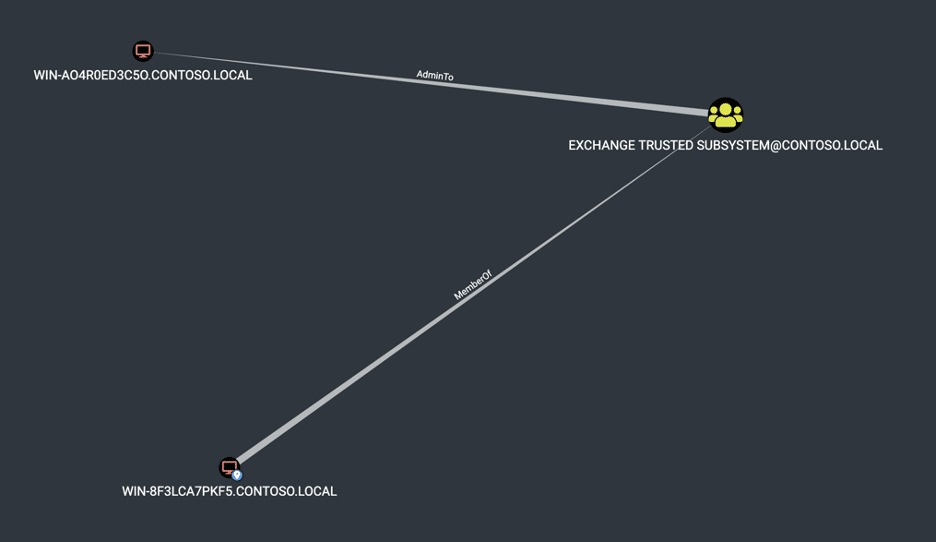
Overview Recently I’ve been working on writing a custom SMB client that implements the initial handshake and NTLM authentication functionality to perform port fingerprinting within Chariot Identify, our attack surface management product. While reading through the SMB specification, I got to thinking about Computer AdminTo Computer vulnerabilities we have exploited over the last few years […]
Log4J Detector Tool

Summary The Log4Shell vulnerability exposed a remote code execution condition in multiple versions of the popular Apache Log4J2 logging library. Disclosure of the vulnerability and patch release were followed shortly by broad exploitation. Attackers reportedly ranged from hobbyists to mature adversaries. Obfuscation of attack traffic and sophisticated weaponization of the exploit soon followed. Companies were […]
Log4j 2.15.0 stills allows for exfiltration of sensitive data

The Apache Software Foundation announced a new vulnerability in Log4j – CVE-2021-45046 – on December 14th. The vulnerability as described states that Log4j 2.15.0 can allow a local Denial of Service attack, but that impacts are limited. However, in our research we have demonstrated that 2.15.0 can still allow for exfiltration of sensitive data in […]
Introducing Snowcat: World’s First Dedicated Security Scanner for Istio

Why Service Meshes Matter Over the last few years, the pace of moving workloads to the cloud has continued to accelerate. Mostly, this has been a boon for innovation, allowing complex monolithic on-prem instances to be broken into microservice architectures, which provide decoupling, agility, and stability. From a development perspective, life has in some ways […]
How to Write and Execute Great Incident Response Playbooks

Introduction Security incidents of any magnitude are bound to happen within any organization, and they should be thoroughly investigated to prevent and protect critical data, resources and services. While it is hard to fully automate the investigation process, we can always introduce scripted plays for common occurrences we might come across – that is where […]
How to Detect and Dump Credentials from the Windows Registry
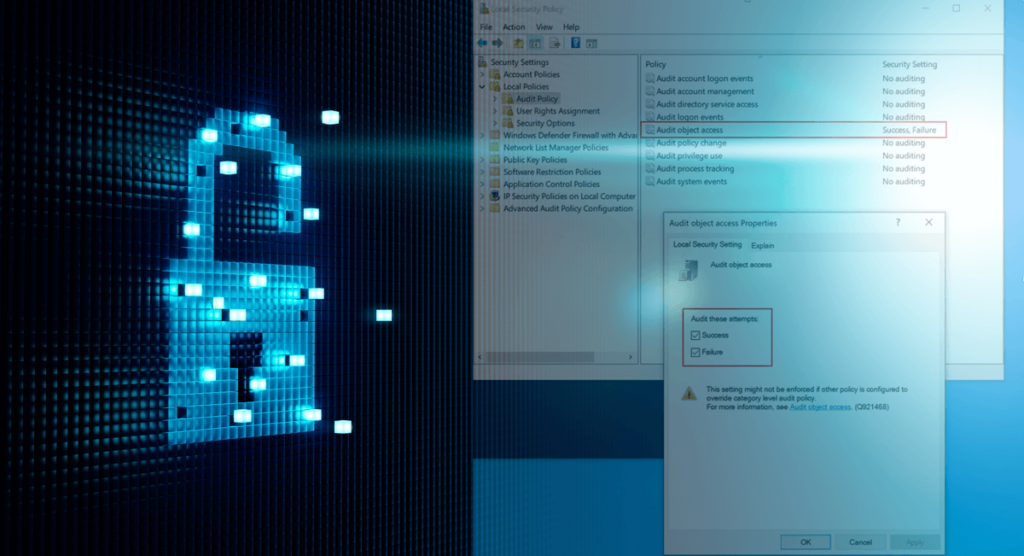
There are several post-exploitation techniques that an attacker can utilize to gather information and compromise assets. One of these techniques is OS credential dumping, and some relevant areas of interest are the Windows Registry and the LSASS process memory. By obtaining additional credentials, an attacker could look to move laterally in the environment by utilizing […]
Incident Response Best Practices: Building an Evidence Wiki

What is an evidence wiki? As Blue Teams work to secure systems, it becomes especially important to keep track of interesting and helpful information gathered through the investigation process. During the investigation of a security incident, one of the very first things teams do is to create a timeline of events via checking various resources. […]
10 Common Security Issues when Migrating from On Premises to Azure

Introduction Cloud migrations often involve moving data, workloads, and applications from an on-premise datacenter to a private or public cloud provider. While cloud migrations can offer significant cost savings, faster product deployments, and improved security controls, there are many common pitfalls to avoid during migration, along with best practices that should be followed to maximize […]