Introducing GoKart, a Smarter Go Security Scanner
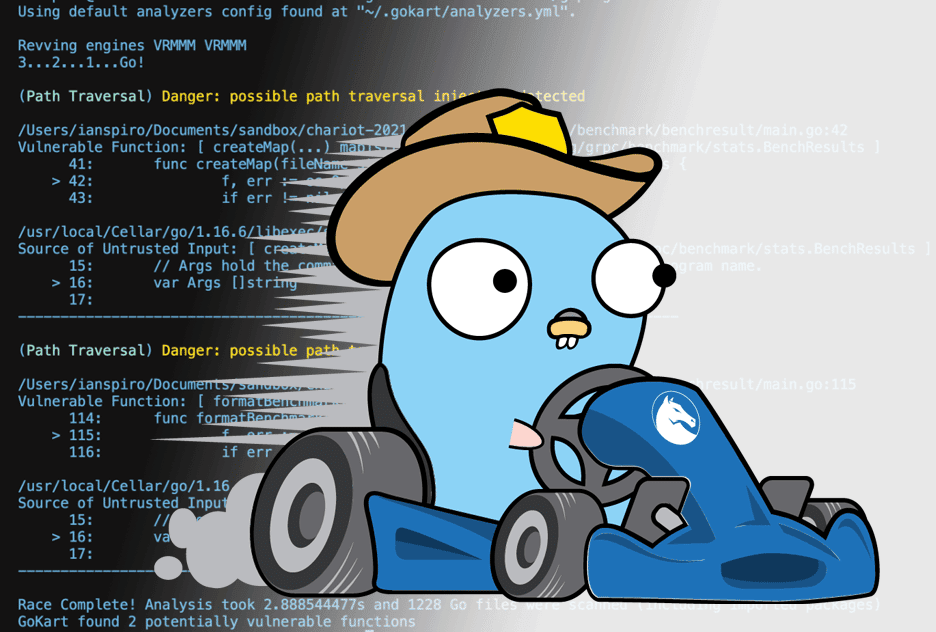
At Praetorian, we’re committed to promoting and contributing to open source security projects and radically focused on developing technologies to enhance the overall state of cybersecurity. We love when our passions and business commitments overlap so today we’re stoked to announce the initial release of GoKart – a smarter security scanner for Go. GoKart is […]
How to improve your Incident Response (IR) with Live Response

Live Response is the process of collecting data from compromised endpoints for an investigation while those assets remain active. Collecting Live Response data is critical to a successful incident response investigation. As Endpoint Detection and Response (EDR) and Antivirus (AV) have grown in capability, so too have attackers. To protect your environment and keep your […]
Threat Intelligence: Tools for Making Your Blue Team Smarter

What is Cyber Threat Intelligence (CTI) There are many definitions of threat intelligence out there. Each vendor has their own ideas about what makes threat intel “threat intel”. Praetorian defines threat intelligence as actionable evidence-based knowledge used to defend against threats. Threat intelligence can take many forms; often, it includes Indicators of Compromise (IOCs), actions, […]
Email Security (SPF, DKIM, and DMARC)

Introduction Our clients occasionally ask us to look into why a particular email that spoofed the client was not blocked by a mail server. Generally these emails are intended to impersonate a user at the company in question, and naturally our clients would want to ensure that the emails are rejected by a receiving mail […]
How to Implement Consistent Identity Management for Improved SaaS Security

Overview The number of SaaS products that businesses integrate into their workflows and processes continues to grow. BMC [1] reports 85% of small companies to have between 25-50 SaaS services in use. Larger organizations (greater than 250 employees) have more than 100 SaaS applications in place. The benefits of SaaS are undeniable: reduced time to […]
Methodology for Hacking IoT: From Chip to Cloud
Introduction Over the past 10 years, Praetorian has tested hundreds of embedded systems, ranging from autonomous vehicles, medical devices, critical infrastructure, and smart consumer devices. Through our collective experience, Praetorian developed techniques and methodologies for testing a large range of IoT systems. In this article, we will go through our methodology to hacking IoT systems, […]
How to redirect traffic from an incoming TCP port using the Portbender utility

Overview In a previous article titled “Active Directory Computer Account SMB Relaying Attack,” we discussed how an attacker could leverage computers assigned administrative rights to other computers to escalate privileges or move laterally using the printer spooler service. Colloquially we often refer to this as a “Computer AdminTo Computer” vulnerability. Exploiting this issue in practice […]
How to Exploit Active Directory ACL Attack Paths Through LDAP Relaying Attacks

Overview This article describes methods by which an attacker can induce a victim user into authenticating using the NT Lan Manager (NTLM) Authentication Protocol to an attacker-controlled “Intranet” site, even in instances where that site points to an external internet-facing IP address. An attacker can then combine this primitive with LDAP relaying capabilities and the […]
Google Cloud IAM: Designs for Self-Service Privilege Escalation

In a perfect world, all organizations would incorporate security into their cloud environments from the start. Unfortunately, common development practices tend to postpone the implementation of security controls in the product environment in favor of shipping product features. The reasons for this are manifold: an early-stage product may ignore robust security processes in favor of […]
Red Team Tooling: Writing Custom Shellcode

Overview This article discusses our recently open-sourced tool Matryoshka [1], which operators can leverage to bypass size limitations and address performance issues often associated with Visual Basic for Applications (VBA) macro payloads. Because Microsoft Office restricts the size of VBA macros, operators can run into size limitations that restrict their ability to include larger payloads […]