Praetorian’s Approach to Red Team Infrastructure
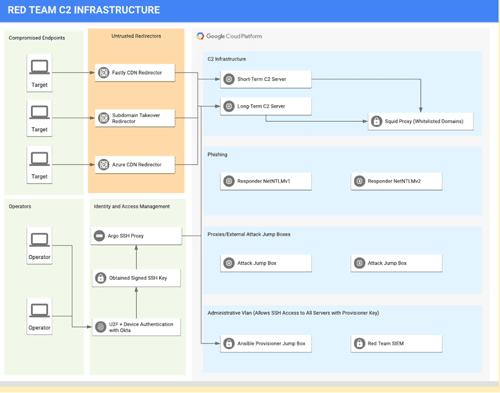
Praetorian provides a best practices approach to Red Team Infrastructure using a Google BeyondCorp architecture
Obtaining LAPS Passwords Through LDAP Relaying Attacks

Commentary on Praetorian’s recent contribution of additional functionality to the Impacket ntlmrelayx utility.
Extending LLVM for Code Obfuscation (2 of 2)
In part one, we covered setting up a development environment for working with LLVM and developed a simple pass that inserted junk code into binaries during compilation to hinder signature-based detection and manual reverse engineering efforts. In this article, we develop a more complex pass that automatically encrypts string literals during the compilation process by […]
Extending LLVM for Code Obfuscation (1 of 2)
Part one of this article covers the necessary background on LLVM, setting up a development environment, and developing an LLVM pass for junk code insertion in an attempt to generate unique polymorphic binaries.
Bypassing Google’s Santa Application Whitelisting on macOS (Part 2 of 2)
This article will examine an example flat PKG installer and demonstrate how to technically abuse Google’s Santa application whitelisting.
Bypassing Google’s Santa Application Whitelisting on macOS (Part 1 of 2)
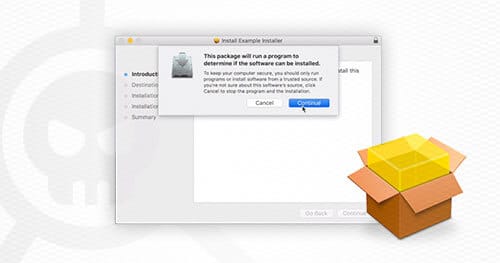
In this blog post, we’ll describe how we developed social engineering payloads for macOS which can be used to bypass Santa’s application whitelisting.
Implementing Application Whitelisting with Google Santa and Upvote (Part 2 of 2)

In part 2 of this series, we will provide technical guidance on how you can deploy Google Santa and Upvote in your organization.
CI/CD Supply Chain Attacks for Data Exfiltration or Cloud Account Takeover
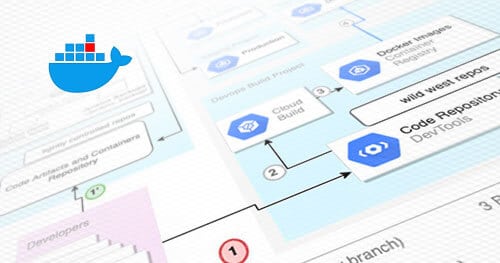
The great challenge of securing CI/CD lies in the nature of the beast. Building arbitrary code and CI/CD scripting tools grant the attacker RCE from the get-go. In this blog we examine a fairly robust architecture, how to break it, and how to further harden the design.
Secure and Scalable Secrets Management in the Cloud for DevOps
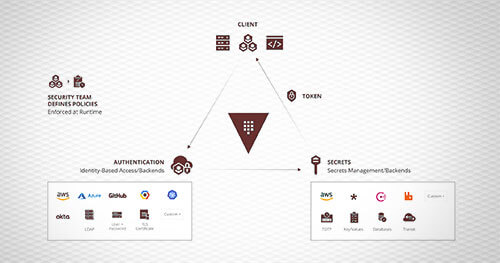
Regardless of industry, size, or tech stack, modern organizations rely on secrets to operate their infrastructure. Increasingly, DevOps teams elect to build or migrate their infrastructure with the cloud. All too often, secure and scalable secret management strategies are forced onto the backlog for the sake of development velocity or underappreciated implications. Ad hoc secret management strategies can have disastrous implications – as application security weaknesses can readily metastasize into complete infrastructure compromise. With increasing complexity and modernization, DevOps operators need a standard method for managing and maintaining secrets within modern environments.
Getting Started with Praetorian’s ATT&CK Automation
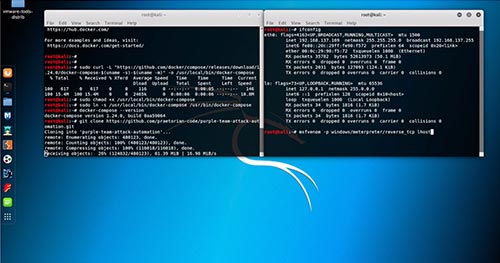
Earlier this month, Praetorian released its automation for emulating adversary tactics, techniques, and procedures (TTPs) based on the MITRE ATT&CK framework. We’ve gotten a number of requests from users asking for more detailed instructions on how to get started with the tool. This blog post accompanies the recently released video tutorial.